Last week Kafeine posted an analysis of a new ransomware called CryptXXX on the Proofpoint blog. Based on their analysis they determined that CryptXXX is affiliated with the developers of the Angler Exploit Kit as well as the Reveton screen locking ransomware family.
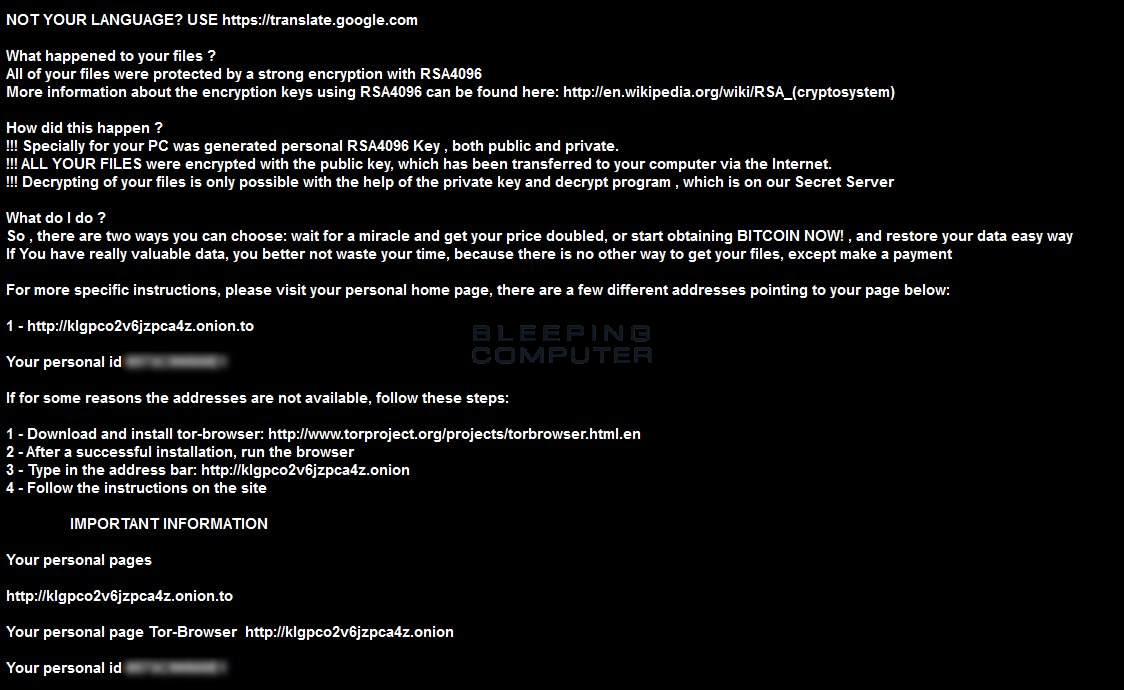
When a user is infected with CryptXXX, all of their data will be encrypted and have the .cryptextension appended to the filenames. The ransomware developers would then demand 500 USD or approximately 1.2 bitcoins to get the decryption key. To make matters worse, this ransomware will also attempt to steal your bitcoin wallet and harvest information and credentials related to your FTP client, instant messenger clients, emails, and browsers.
Thankfully, yesterday Kaspersky released a free decryptor for this ransomware.
Kaspersky releases a free decryptor for CryptXXX files
With the amount of ransomware being released and the torture they bring to people, it is a good day when someone releases a free decryptor for a ransomware program. Yesterday, Kaspersky was able to figure out a weakness in the CryptXXX ransomware and release a free decryptor that a victim can use to get their files back.
This new decryptor is called RannohDecryptor and will try to determine the decryption key in a encrypted file. If it is unable to do so, a victim will need to input into the program the same file in its encrypted and unencrypted format. Using this file pair, the decryptor can then determine the decryption key used by all of the encrypted files. As a heads up, you will most likely need to find a pair of files that are both encrypted and unencrypted.
What I usually suggest people do when they need a pair of files (unencrypted + encrypted) is to use the sample pictures found in the C:\Users\Public\Pictures\Sample Pictures folder. These images are always encrypted by a ransomware and their unencrypted versions can easily be downloaded from another computer. To make it easier, I have created a repository of the Windows 7 sample pictures here: https://download.bleepingcomputer.com/public-sample-pictures/. If you find Windows 8 or Widows 10 use different files, let me know and I will upload a repository from those operating systems.
KASPERSKY RANNOHDECRYPTOR.EXE DOWNLOAD NOW
To start the decryption process, simply download and execute the above file. When you run the program and click on the Start button it will ask you to select a encrypted file. Once you select a file, it will try to determine the decryption key. It most likely will not be able to do so and will prompt you to select a pair of the same file that are encrypted and unencrypted.
Select an encrypted file from the C:\Users\Public\Pictures\Sample Pictures and it will then ask you to select an unencrypted version of the same file. Simply download the corresponding unencrypted image from here and select it. The decryptor should then be able to determine the decryption key and start decrypting your files.
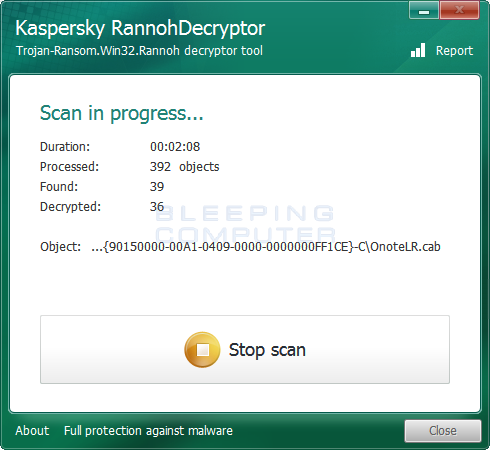
When it has finished decrypting your files, you can close the decryption program and remove it from your computer. It is also suggested that you scan your computer with the antivirus or anti-malware program of your choice to remove any other leftovers.
Files associated with CryptXXX:
de_crypt_readme.bmp
de_crypt_readme.txt
de_crypt_readme.html
%AppData%\[id].dat
%Temp%\{C3F31E62-344D-4056-BF01-BF77B94E0254}\api-ms-win-system-softpub-l1-1-0.dll
%Temp%\{D075E5D0-4442-4108-850E-3AD2874B270C} \api-ms-win-system-provsvc-l1-1-0.dll
%Temp%\{D4A2C643-5399-4F4F-B9BF-ECB1A25644A6}\api-ms-win-system-wer-l1-1-0.dll
%Temp%\{FD68402A-8F8F-4B3D-9808-174323767296}\api-ms-win-system-advpack-l1-1-0.dll
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











