A security researcher named Mosh has discovered a new variant of the 7ev3n Ransomware, which has rebranded itself as 7ev3n-HONE$T. This ransomware will encrypt your data and then ransom your files for approximately $400 USD in bitcoins. It is currently unknown how it is being distributed or what encryption type it uses. Unfortunately, there is no way to decrypt the files for free at this time.
When 7ev3n-HONE$T encrypts your data it will rename your files to sequential numbers using the .R5A extension. For example, a folder’s files would be renamed to 1.R5A, 2.R5A, 3.R5A, etc. 7ev3n-HONE$T will then add the name of the encrypted file to the C:\Users\Public\files file.
When it has finished encrypting your data it will connect to the Command & Control server and upload a variety of information and statistics. The information sent is your assigned bitcoin address, the total amount of files encrypted, the amount of each type of file extensions, and your unique ID. According to Mosh, the Command & Control server is located at the IP address 46.45.169.106 (Turkey Istanbul Radore Veri Merkezi Hizmetleri As / AS197328).
When done, the following files will be located in the C:\Users\Public folder:
- C:\Users\Public\conlhost.exe – The ransomware executable
- C:\Users\Public\files – The list of encrypted files
- C:\Users\Public\FILES_BACK.txt – An alternative method to contact the ransomware developer.
- C:\Users\Public\testdecrypt – A list of files that can be decrypted for free.
- C:\Users\Public\time.e – The timestamp of when the ransomware encrypted your files.
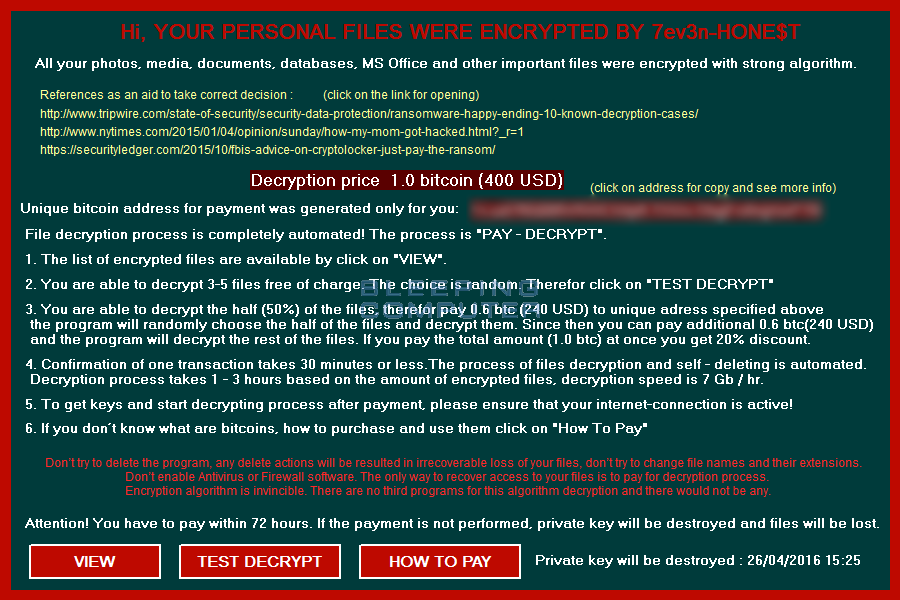
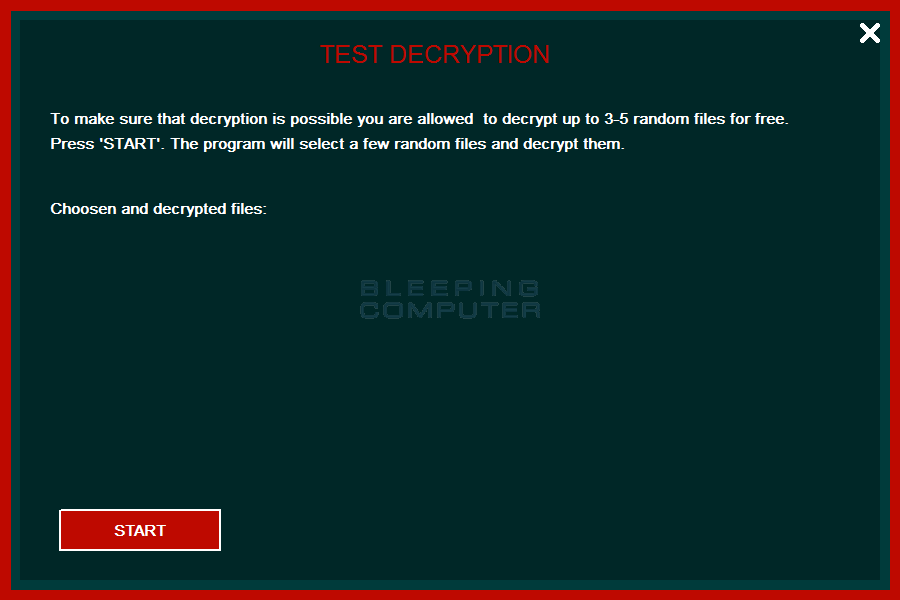
The ransomware lock screen is broken up into four different windows. The first window is main lock screen, as shown above, and displays the ransom note and bitcoin address that payment should be sent to. The second screen allows you to perform a test decryption on three to five files.
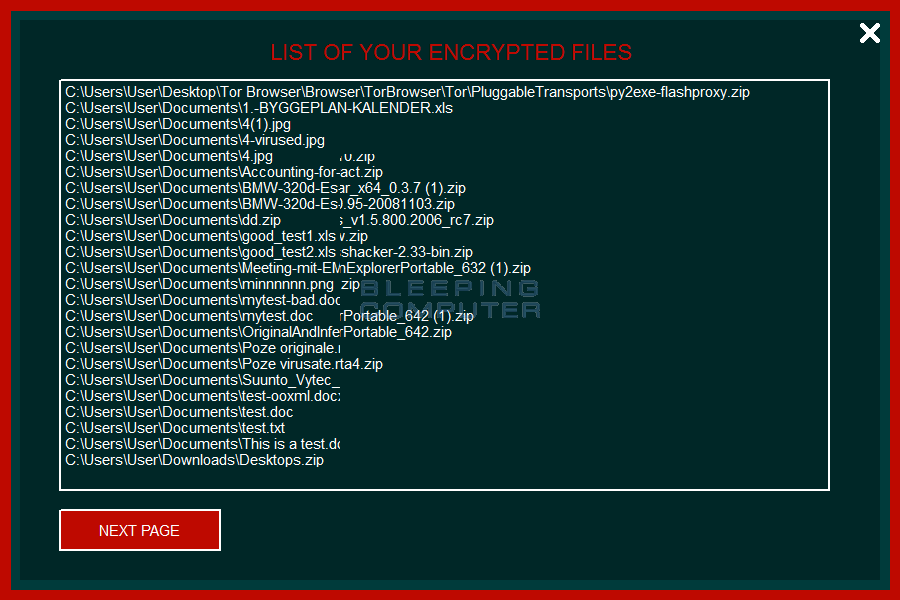
The third screen displays a list of all encrypted files.
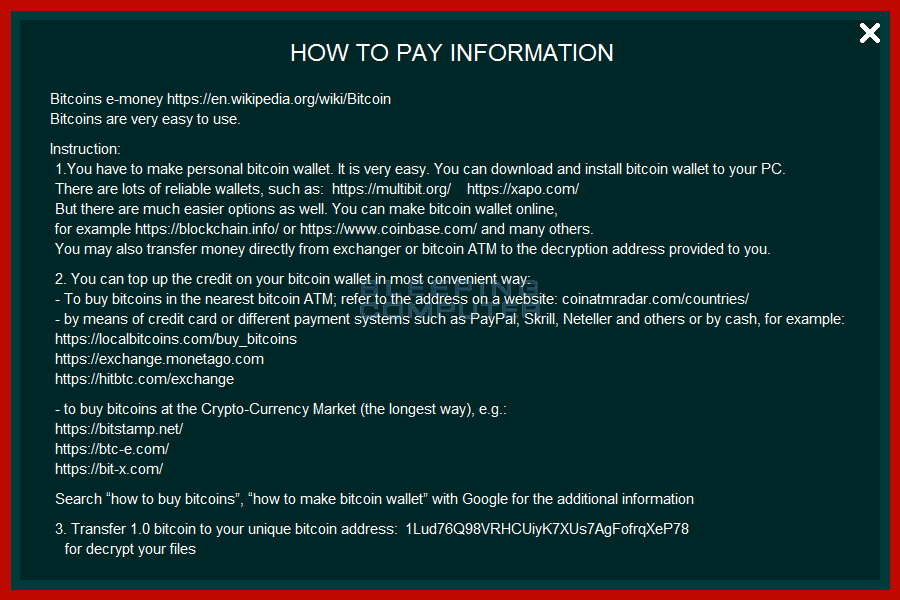
The fourth screen provides information on how to pay the ransom.
At this time there is no way to decrypt the files for free, but if anything changes I will be sure to update this article.
Files associated with 7ev3n-HONE$T:
C:\Users\Public\conlhost.exe
C:\Users\Public\files
C:\Users\Public\FILES_BACK.txt
C:\Users\Public\testdecrypt
C:\Users\Public\time.e
%Temp%\fpnzzreRegistry entries associated with 7ev3n-HONE$T:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\allkeeper C:\users\Public\conlhost.exe
HKCU\Software\crypted 1
HKCU\Software\testdecrypt 1Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.










