A new ransomware was discovered that tries to impersonate the well known Locky ransomware. It calls itself Locky and even adds .Locky to encrypted files, but on closer examination there was definitely something off. First, the ransom note is completely different and it does not utilize Tor for its Command & Control servers. When I dug down farther I saw that it was also created in the AutoIt scripting language rather than Visual C++.
Once Fabian Wosar of Emsisoft saw the decompiled AutoIt script, he quickly found a vulnerability that he could exploit to decrypt those who were affected. Unfortunately, it is unknown at this time how AutoLocky is distributed.
In the article below I will outline how to decrypt your files and provide a brief technical overview of the AutoLocky encryption process. For those who want to see a list of Emsisoft’s free ransomware decryptors, you can visit their decryptor page.
How to Remove AutoLocky and decrypt its Locky Files
If you are infected with AutoLocky, the first thing you want to do look at the properties of its startup folder link to determine the executable that is launching it. Once you determine the executable name, start Task Manager and end it’s process. You can then delete the associated executable. The startup link will be found at %UserProfile%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Start.lnk.
Once the ransomware process has been terminated and the startup link removed, download the AutoLocky decryptor from the link below and save it on your desktop.
Once it has been downloaded, double-click on the decrypt_autolocky.exe executable to launch the program. The program will start and you may be presented with a UAC prompt. Please click on Yes button to proceed. The program will now start and attempt to retrieve the decryption key. When a key was able to be found, it will display it an a new window like the one below.
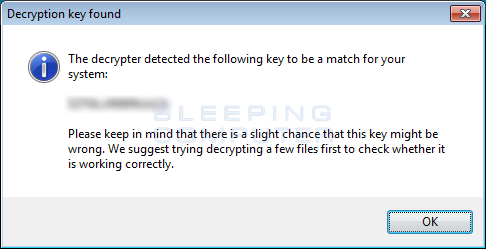
When you press the OK button you will be presented with a license agreement you must agree to. To continue, press the OK button and the main AutoLocky Decryptor screen will be shown as seen below.
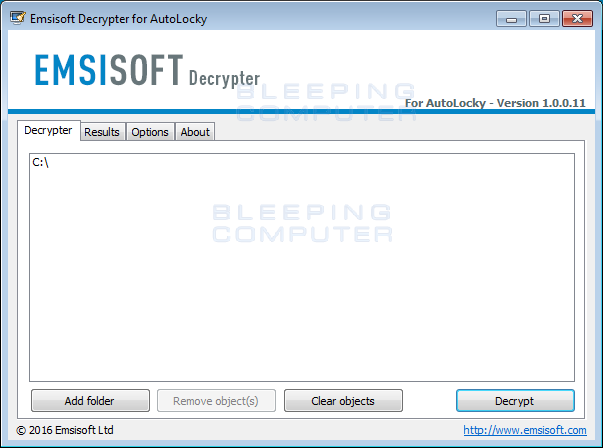
By default, the decryptor is only going to decrypt files on the C: drive. If there are other drives with encrypted files, click on the Add folder button to add the drive to the list. When ready, click on the Decrypt button to begin decrypting your files. Once you click Decrypt, the decryptor will decrypt all the encrypted files and display the decryption status in a results screen like the one below.
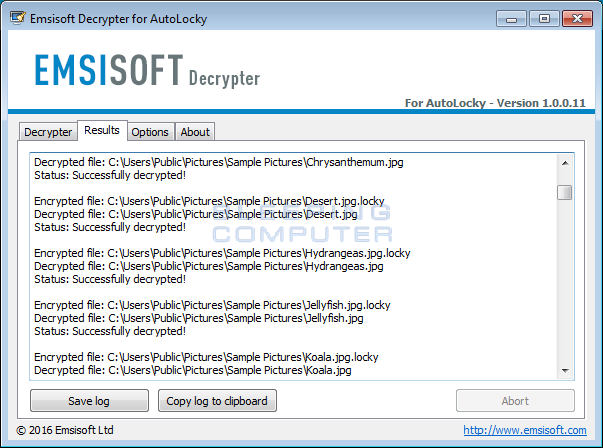
All of your files should now be decrypted and you can close the decryptor.
For those who wish to know more technical information about this ransomware, you can read the following sections.
AutoLocky may be the first crypto-ransomware created in AutoIt
One of the interesting characteristics of this crypto-ransomware is that it may be the first one to be programmed using AutoIt. AutoIt is a scripting language that was originally developed to aid in PC “roll-out” implementations. Overtime is has grown into a powerful language that allows you create programs for almost any task.
One of the weaknesses of AutoIt malware programs is that they can be decompiled back into a readable script. This allows researchers to see the almost exact code as the original script that was then compiled into an executable. Analyzing a malware in its original form them becomes trivial.
The AutoLocky Enryption cMethod
It is currently unknown how the AutoLocky ransomware is being distributed. It’s icon impersonates an Adobe PDF icon, so it is possible that it is distributed via email attachments. Once installed, AutoLocky will scan all fixed drives for targeted data files and encrypt them using the AES-128 algorithm. When a file is encrypted, the ransomware will append the .locky extension on to the filename. So the file, test.jpg would become test.jpg.locky. The files types targeted by the AutoLocky ransomware are:
docm,docx,dot,doc,txt,xls,xlsx,xlsm,7z,zip,rar,jpeg,jpg,bmp,pdf,ppsm,ppsx,ppam,potm,potx,pptm,pptx,pps,pot,ppt,xlw,xll,xlam,xla,xlsb,xltm,xltx,xlm,xlt,xml,dotm,dotx,odf,std,sxd,otg,sti,sxi,otp,odg,odp,stc,sxc,ots,ods,sxg,stw,sxw,odm,oth,ott,odt,odb,csv,rtf,accdr,accdt,accde,accdb,sldm,sldx,drf,blend,apj,3ds,dwg,sda,ps,pat,fxg,fhd,fh,dxb,drw,design,ddrw,ddoc,dcs,wb2,psd,p7c,p7b,p12,pfx,pem,crt,cer,der,pl,py,lua,css,js,asp,php,incpas,asm,hpp,h,cpp,c,csl,csh,cpi,cgm,cdx,cdrw,cdr6,cdr5,cdr4,cdr3,cdr,awg,ait,ai,agd1,ycbcra,x3f,stx,st8,st7,st6,st5,st4,srw,srf,sr2,sd1,sd0,rwz,rwl,rw2,raw,raf,ra2,ptx,pef,pcd,orf,nwb,nrw,nop,nef,ndd,mrw,mos,mfw,mef,mdc,kdc,kc2,iiq,gry,grey,gray,fpx,fff,exf,erf,dng,dcr,dc2,crw,craw,cr2,cmt,cib,ce2,ce1,arw,3pr,3fr,mdb,sqlitedb,sqlite3,sqlite,sql,sdf,sav,sas7bdat,s3db,rdb,psafe3,nyf,nx2,nx1,nsh,nsg,nsf,nsd,ns4,ns3,ns2,myd,kpdx,kdbx,idx,ibz,ibd,fdb,erbsql,db3,dbf,db-journal,db,cls,bdb,al,adb,backupdb,bik,backupWhen it has finished encrypting the files, it will create the Info.html and Info.txt ransom notes on the Windows desktop. Once the ransom notes have been created, it will then upload your encryption key to the Command & Control server located at crazyloading.cc.

Oddly, this ransomware does not attempt to delete the Shadow Volume Copies on the infected computer.
Associated AutoLocky Files:
%UserProfile%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Start.lnk
%UserProfile%\Desktop\info.html
%UserProfile%\Desktop\info.txtAssociated Network Hosts:
crazyloading.cc
Source:https://www.bleepingcomputer.com/
Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











