Locky is a new ransomware that has been released (most probably) by the Dridex gang (source). Not surprisingly, it is well prepared, which means that the threat actor behind it has invested sufficient resources for it, including its mature infrastructure. Let’s take a look.
Analyzed samples
- 7a23368ee84781d7584e058a9922f324
- payload: 74dde1905eff75cf3328832988a785de <- main focus of this analysis
- d9df60c24ceca5c4d623ff48ccd4e9b9
- e7aad826559c8448cd8ba9f53f401182
Behavioral analysis
Locky is usually delivered via malicious MS Office document (i.e. DOC) e-mail attachment in a phishing campaign. The payload is a 32-bit Windows executable, containing the malicious core packed in a dropper (droppers are various, with various icons).

After being deployed it disappears and runs its dropped copy (renamed to svchost.exe) from the %TEMP% folder.
Encryption process
Files that have been encrypted are fully renamed. The beginning of the name (first 16 characters) is the unique ID of the victim. Then comes the ID of the file and the extension.locky that is typical for this ransomware.

The encrypted content has a high level of entropy and no patterns are visible.
Below: visualization of raw bytes of square.bmp. Left: unencrypted, right: encrypted.


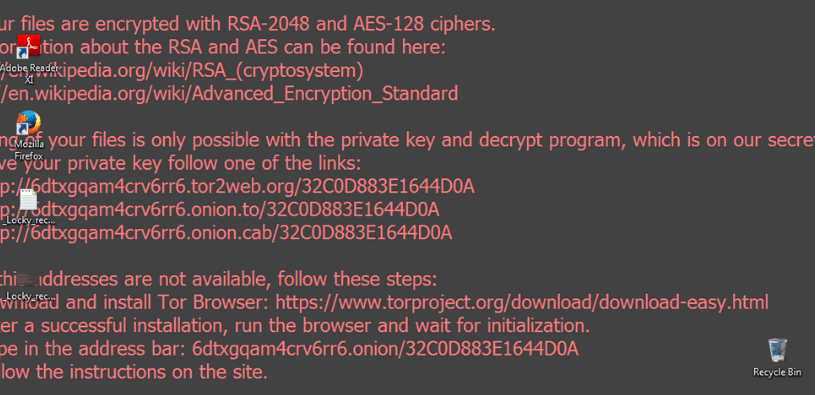
After executing, Locky displays the ransom note in text and bitmap forms, setting the latter as the affected user’s wallpaper.
 Text is localized to the language detected in the system. Translation looks professional enough (not from the auto translator), which may indicate that the threat actors target multiple countries – and prepared about this particular detail well. See sample translations (Polish, Spanish) here.
Text is localized to the language detected in the system. Translation looks professional enough (not from the auto translator), which may indicate that the threat actors target multiple countries – and prepared about this particular detail well. See sample translations (Polish, Spanish) here.
Registry keys
Looking at the registry we can find that a few elements have been added.
Key in autorun, to start the malware automatically after the system restart:

Data specific to the victim – individual ID, public RSA key and text of the ransom note to be displayed:

Public key stored in the registry:

Website for the victim
Each Locky victim has a Web page that can be accessed via Tor. These pages contain further instructions to the victim and support for managing payments.

Network communication
Locky communicates with the CnC, but it is difficult to analyze it via simple sniffing tools because full communication is encrypted:

More about the protocol can be learned by reading the code…
Inside
Every sample of Locky comes packed in some crypter, so the code is unreadable at first.
 However, the core itself is not that obfuscated. After unpacking the outer layer of its defense, we can see valid strings and function calls. They give some explanation to the unreadable network capture. The RSA key as well as the ransom note are fetched from the server by a HTTP based protocol. The current sample comes with a list of 3 IP addresses.
However, the core itself is not that obfuscated. After unpacking the outer layer of its defense, we can see valid strings and function calls. They give some explanation to the unreadable network capture. The RSA key as well as the ransom note are fetched from the server by a HTTP based protocol. The current sample comes with a list of 3 IP addresses.

- 31.41.47.37
- 188.138.88.184
- 85.25.138.187
Additionally it makes use of DGA – Domain Generation Algorithm (more described here).
Communication protocol
Locky’s communication protocol is pretty simple: it consists of a POST request with parameters in a typical key=value format. However, as mentioned before, they are not sent by an open text, but wrapped and encrypted. First, the request is prepared and it’s parameters are filled. Then its MD5 is calculated. Both elements are concatenated and encrypted together.
Example of wrapped request (before encryption):

Similarly, when the response comes, first it gets decrypted, then its MD5 is validated – and if it passed the validation then it is parsed.
Example of received response (encrypted):

Decrypting:

Decrypted response turns out to be an RSA key prompted by its hash:
 Locky uses 3 commands (identified by the key act):
Locky uses 3 commands (identified by the key act):
- getkey
- gettext
- stats
We have explained the actions in further detail below.
[getkey] Initial registration and fetching the RSA key:
id=[16]&act=getkey&affid=1&lang=[2:lang]&corp=[0-1]&serv=[0-1]&os=[Windows name]&sp=[num]&x64=[0-1]
Unique user ID is 16 byte long hexadecimal string, created locally (pseudocode):
win_dir = GetWindowsDirectory mount_point_name = GetVolumeNameForVolumeMountPoint(win_dir) GUID = get_GUID(mount_point_name) md5sum = MD5(GUID) id = md5sum.uppercase().substr(0,16)
After that follows:
Language: obtained by functions: GetLocaleInfo , GetUserDefaultUILanguage. System info – fetched by GetVersionEx and GetSystemMetrics(SM_SERVERR2) and translated to the built in lists. IsWow64Process is used to identify if the system is 64bit.
[gettext] Fetching the ransom text:
id=[16]&act=gettext&lang=[2:lang]
[stats] Sending statistics about encrypted files:
id=[16]&act=stats&path=[root_path]&encrypted=[num]&failed=[num]&length=[num]
What is attacked?
Locky attacks 3 types of local drives: fixed, removable and ramdisks…

…as well as network resources. Network shares are mapped using WNetAddConnection2

For every drive a new encrypting thread is started.
How does the encryption work?
In the ransom note attackers claimed that Locky uses both RSA and AES algorithms. Looking at the code we can confirm this. Cryptography is implemented using Windows Crypto API and really uses the mentioned algorithms.
First, RSA key (2048 bit) is fetched from the server and imported:

The RSA key is used to encrypt AES keys, which are randomly generated for each file. Below – importing a random AES key (128 bit long):

Processing of the files starts by enumerating them and storing in a list. Then the encryption proceeds by this list.
 Every thread collects statistics about the encrypted files (i.e summary of how many files has been encrypted in a particular path):
Every thread collects statistics about the encrypted files (i.e summary of how many files has been encrypted in a particular path):
 Statistics are encrypted and sent to the C&C.
Statistics are encrypted and sent to the C&C.
Ransom note
As mentioned before, ransom note in a language detected language byGetUserDefaultUILanguage is downloaded from the server.
Most ransomware drops ransom notes in HTML form, and then opens it in a Web browser. Locky does something more interesting: it renders and sets a bitmap as wallpaper.
 Bitmap rendering:
Bitmap rendering:
 Wallpaper settings are edited by registry keys:
Wallpaper settings are edited by registry keys:
 After successful rendering and saving the bitmap, it sets it as a wallpaper usingSystemParamsInfo (action 0x14 = SPI_SETDESKWALLPAPER)
After successful rendering and saving the bitmap, it sets it as a wallpaper usingSystemParamsInfo (action 0x14 = SPI_SETDESKWALLPAPER)

Conclusion
Locky struck in February but it has already gained popularity. Due to the fact that it is a wide spread attack, carried by the same entities that distribute Dridex, it easily triggered interest of many researchers. Upon closer inspection, however, we can say that it is not that different from common ransomware. It looks solidly written and well prepared, but it doesn’t show too much novelty so far.
Source:https://blog.malwarebytes.org

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.