In December 2024, Arctic Wolf Labs uncovered a targeted campaign exploiting Fortinet FortiGate firewalls via publicly exposed management interfaces. This campaign enabled threat actors to gain unauthorized access, alter configurations, and extract credentials using advanced techniques such as DCSync. The attack likely leveraged a zero-day vulnerability, with affected devices running firmware versions 7.0.14 to 7.0.16. The exploitation has highlighted critical vulnerabilities in public-facing interfaces, urging organizations to reevaluate their security posture.

Campaign Analysis
The attack unfolded in four distinct phases:
- Vulnerability Scanning (November 16–23, 2024): Threat actors initiated widespread scans to identify vulnerable devices. They used spoofed IP addresses, including loopback addresses and public DNS resolvers, to access administrative functionalities via the
jsconsoleinterface. - Reconnaissance (November 22–27, 2024): After identifying vulnerable devices, the attackers made minor system console changes to validate their access. These modifications, such as toggling the system output settings between “more” and “standard,” indicated attempts to test their control over the CLI interface.
- SSL VPN Configuration (December 4–7, 2024): Threat actors established persistence by creating super admin accounts and configuring SSL VPN portals. In many cases, they hijacked existing user accounts, including the default “guest” account, to maintain access. New VPN portals were assigned non-standard ports such as 4433, 59449, and others to evade detection.
- Lateral Movement (December 16–27, 2024): Using domain admin credentials obtained via DCSync, the attackers performed credential dumping and began lateral movement within compromised environments. Evidence pointed to the use of tools such as workstations with kali identifiers to facilitate these activities.
Technical Observations
Anomalous jsconsole Activity:
- Administrative logins were observed from spoofed IP addresses, such as:
- 127.0.0.1 (loopback)
- 8.8.8.8 and 8.8.4.4 (Google DNS)
- 1.1.1.1 and 2.2.2.2 (Cloudflare DNS)
Web Management HTTPS Traffic:
- Unusual HTTPS sessions originated from IPs associated with VPS providers. Key indicators included:
- Data transfers exceeding 1MB.
- Session durations of over 100 seconds.
- Connections terminated by RST packets initiated from the client side.
SSL VPN Modifications:
- New super admin accounts were created, often using random alphanumeric names.
- Existing accounts were hijacked and repurposed for VPN access.
- Custom VPN portals with non-standard ports were configured, ensuring persistent access.
Timeline of Activity:
- Firmware versions 7.0.14 to 7.0.16 were exploited.
- Initial activity began in November 2024, with significant malicious configuration changes observed in December 2024.
Tactics, Techniques, and Procedures (TTPs)
Initial Access:
- Exploitation of public-facing management interfaces (T1190), potentially involving a zero-day vulnerability.
Persistence:
- Creation of local admin accounts (T1136.001).
- Modification of SSL VPN configurations (T1133).
- Hijacking of default accounts (T1078.001).
Credential Access:
- Credential dumping via DCSync (T1003.006).
Defense Evasion:
- Modification of system console configurations to obscure activity (T1562).
Lateral Movement:
- Exploitation of remote services using compromised credentials (T1210).
Detection Opportunities
To mitigate risks, organizations should monitor for the following indicators:
- jsconsole Activity:
- Administrative logins originating from unusual IP addresses, such as loopback or public DNS resolvers.
- Web Management Traffic:
- HTTPS sessions exceeding 1MB originating from VPS provider IPs.
- Sessions with durations over 100 seconds.
- SSL VPN Modifications:
- New VPN portals configured on non-standard ports (e.g., 4433).
- Suspicious logins from unfamiliar IP addresses.
- Credential Dumping and Lateral Movement:
- Detection of DCSync activities and unauthorized Active Directory replication events.
Remediation Recommendations
Secure Management Interfaces:
- Restrict access to management interfaces using IP allowlists or VPN-only access.
- Disable web-based CLI access unless absolutely necessary.
- Enforce multi-factor authentication (MFA) for administrative logins.
Patch and Update Firmware:
- Apply the latest firmware updates to FortiGate devices.
- Monitor vendor advisories for emerging vulnerabilities and patches.
Enhance Monitoring and Logging:
- Implement intrusion detection/prevention systems (IDS/IPS).
- Set up logging and alerts for unusual jsconsole and VPN activity.
Incident Response Preparedness:
- Remove unauthorized accounts and reset credentials on compromised systems.
- Conduct thorough log reviews to identify additional indicators of compromise.
Educate and Train Personnel:
- Train IT staff on the secure configuration of FortiGate firewalls.
- Maintain awareness of emerging threats and vulnerability disclosures.
Conclusion
This campaign underscores the persistent risk posed by public-facing management interfaces and the importance of proactive cybersecurity measures. Organizations using Fortinet FortiGate firewalls are strongly advised to implement the recommended remediation steps and continuously monitor their systems for anomalous activity. Arctic Wolf Labs remains committed to providing timely updates and insights as more information becomes available.
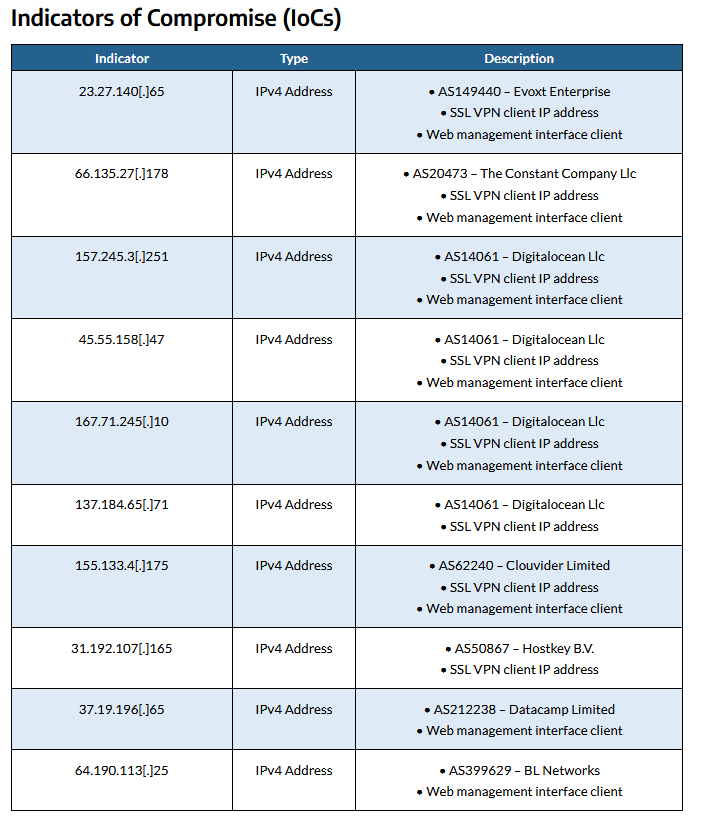
For further technical details and IoCs, refer to the comprehensive indicators outlined by Arctic Wolf Labs.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











