Researchers from the University of the West Indies have uncovered critical vulnerabilities in the Wi-Fi Protected Access 3 (WPA3) protocol, exposing potential risks to networks believed to be highly secure. By combining Man-in-the-Middle (MITM) attacks with social engineering techniques, the team demonstrated how attackers could bypass WPA3 protections and obtain network credentials, raising concerns within the cybersecurity community.
Background: WPA3’s Enhanced Security Framework
Introduced in 2018 as a successor to WPA2, WPA3 was designed to address known weaknesses in its predecessor. A hallmark of this protocol is the Simultaneous Authentication of Equals (SAE) handshake mechanism, intended to enhance password protection and prevent offline dictionary attacks. WPA3 also features a “transition mode” to ensure backward compatibility with WPA2 devices. However, this transition mode has emerged as a significant point of exploitation.
The Attack Methodology: A Closer Look
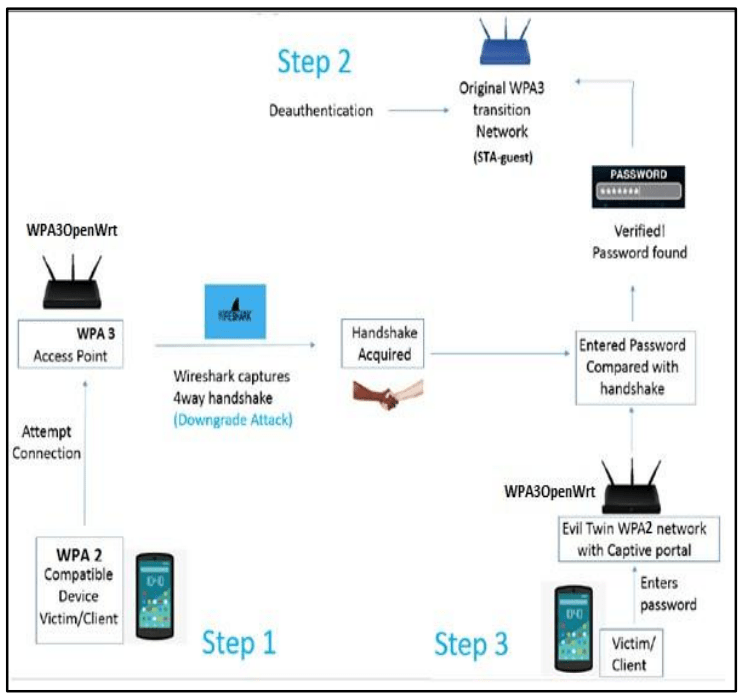
The research team, led by cybersecurity experts Kyle Chadee, Wayne Goodridge, and Koffka Khan, outlined a multi-step attack process that takes advantage of WPA3’s vulnerabilities in transition mode. The attack requires specific conditions, such as a misconfigured network or users unaware of potential risks. Here’s a breakdown of their methodology:
- Handshake Downgrade and Capture
- Attackers initiated a downgrade attack to force the network to fall back to WPA2 settings, enabling the capture of a portion of the WPA3 handshake. This was crucial for subsequent exploitation.
- Deauthentication of Users
- Legitimate users were forcibly disconnected from the original WPA3-secured network, creating an opportunity for attackers to launch a rogue access point.
- Creation of an “Evil Twin” Network
- Using a Raspberry Pi and tools like Airgeddon, the attackers simulated a malicious access point (commonly referred to as an “evil twin”) that mimicked the legitimate WPA3 network.
- Social Engineering via Captive Portal
- Victims attempting to reconnect to the network were redirected to a fake captive portal. Here, users were tricked into entering their Wi-Fi passwords, which were then validated against the captured handshake.
Key Technical Observations
The research highlights several weaknesses in WPA3, particularly in its transition mode. Most notably:
- The attack was only feasible when Protected Management Frames (PMFs) were not implemented. PMFs, which enhance the protection of management communications between devices, are often disabled by users who lack technical expertise.
- Devices that failed to connect to WPA3 transition networks undermined claims by the Wi-Fi Alliance regarding seamless backward compatibility with WPA2.
The team also emphasized that although the attack required specific conditions, such as network misconfigurations and user interaction, the implications are significant for environments relying on WPA3 for critical infrastructure security.
Implications for Wireless Security
This research underscores the ongoing challenges in securing wireless networks, even with advanced protocols like WPA3. As the use of wireless technology expands across industries, vulnerabilities like these pose risks to businesses, governments, and individual users. Cybercriminals can potentially exploit these gaps to access sensitive data, disrupt operations, or launch further attacks.
Impact on the Cybersecurity Community:
- Loss of Trust in WPA3 Security: Many organizations and consumers have adopted WPA3 under the assumption that it offers strong protections. This study calls that assumption into question.
- Increased Risk for IoT Devices: With IoT devices relying on wireless connectivity, a breach of WPA3-protected networks could compromise entire ecosystems.
Recommendations for Mitigating Risks
To address these vulnerabilities, the researchers and cybersecurity experts recommend the following best practices:
- Enforce Secure Configurations: Users and administrators should ensure that Protected Management Frames (PMFs) are enabled across all devices and access points.
- Conduct User Awareness Campaigns: Educating users about the dangers of rogue networks and how to recognize malicious captive portals is critical.
- Limit the Use of Transition Mode: Where possible, organizations should disable WPA3’s transition mode and fully migrate to WPA3-only networks.
- Monitor Network Activity: Implement intrusion detection and prevention systems to monitor for unusual activity, such as unauthorized deauthentication or rogue access points.
Additionally, the cybersecurity community is encouraged to push for ongoing improvements to the WPA3 standard, as well as the development of countermeasures to address these emerging threats.
A Call for Further Research and Innovation
This study serves as a reminder that even the most robust security protocols can be susceptible to creative exploitation by attackers. As the battle between cybersecurity professionals and adversaries intensifies, continuous innovation is essential.
The research team has announced plans to further investigate WPA3 vulnerabilities and work on developing more advanced safeguards for future wireless protocols. Their work is part of a broader effort to ensure that wireless security evolves in tandem with the increasing complexity of modern cyber threats.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











