A recent investigation has uncovered a series of sophisticated cyber-attacks by the Advanced Persistent Threat (APT) group known as GoldenJackal, which successfully breached air-gapped government systems in Europe. These isolated networks, designed to prevent unauthorized access by being physically separated from unsecured networks, were compromised using specially developed malware that leverages USB drives and other custom tools. The breaches have allowed GoldenJackal to steal sensitive information, raising concerns over the security of critical infrastructure and governmental systems.
Overview of the Breaches
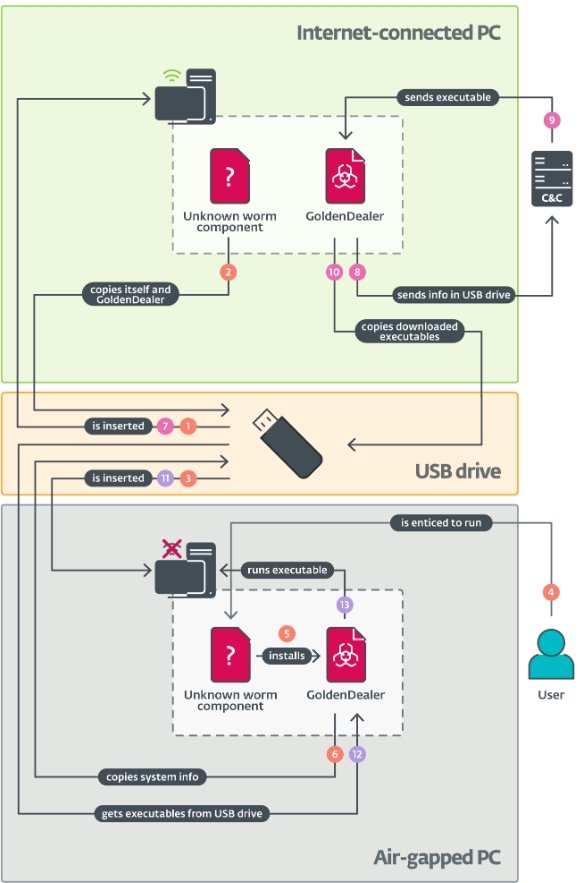
GoldenJackal’s attack strategy involves a multi-phase process beginning with the infection of internet-connected systems, which are then used to introduce malware into the air-gapped environment. Initial infections are likely delivered via spear-phishing or through compromised software containing trojanized files. Once the malware, known as GoldenDealer, infects these internet-facing systems, it waits for a USB drive to be connected. The malware then copies itself onto the USB drive, along with additional payloads, to prepare for insertion into the isolated, air-gapped network.
The malware suite includes two primary components for air-gapped infiltration:
- GoldenHowl: A backdoor that allows GoldenJackal to maintain control over the infected system, collect data, and execute commands. It is versatile, capable of scanning for vulnerabilities, and communicates directly with GoldenJackal’s command and control (C2) infrastructure.
- GoldenRobo: A data-stealing component that scans for files of interest, such as documents, encryption keys, images, and other confidential data. This malware collects these files in a hidden directory on the USB drive for exfiltration.
Once the USB drive is inserted back into the internet-connected system, GoldenDealer automatically transfers the collected data to the C2 server, thereby bypassing network security barriers.
Evolution of GoldenJackal’s Toolsets
GoldenJackal’s tactics have evolved over time. By 2022, the group had introduced a new modular toolset written in Go, allowing them to assign specific roles to various devices in the attack chain. This approach not only streamlines their operation but also makes it harder to detect by distributing tasks across multiple systems. Key tools in this updated arsenal include:
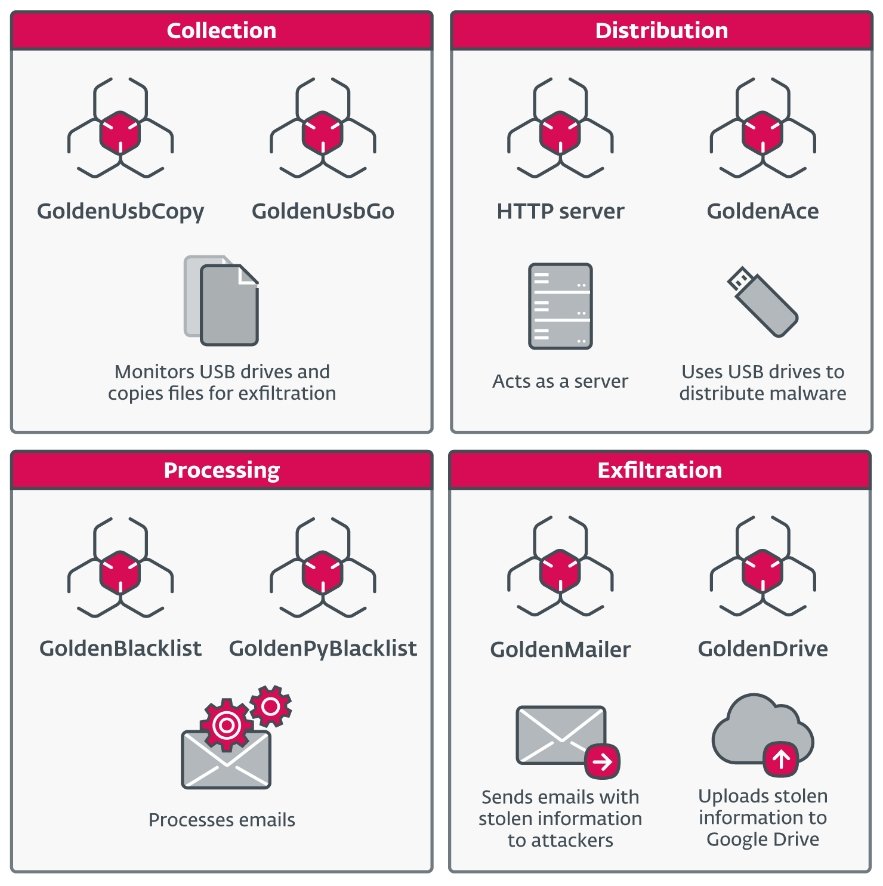
- GoldenUsbCopy and GoldenUsbGo: These tools facilitate USB-based infection and are designed to detect and exfiltrate specific types of data, including files modified within the last two weeks and files that contain sensitive keywords such as “login,” “password,” or “key.”
- GoldenBlacklist and GoldenPyBlacklist: These components filter and archive specific emails from compromised systems, ensuring that only relevant information is exfiltrated.
- GoldenMailer and GoldenDrive: These modules handle the exfiltration process, using email and cloud storage services like Google Drive to transmit data back to GoldenJackal. GoldenMailer automatically emails collected files, while GoldenDrive uploads them to cloud storage.
1. GoldenDealer
- Purpose: Transfers files and malware between connected and air-gapped systems using USB drives.
- Functionality:
- Monitors USB insertion and internet connectivity on both connected and air-gapped systems.
- Downloads executables from a C&C server when a connection is available and stores them on USB drives for air-gapped systems.
- Automatically executes payloads on air-gapped systems without user interaction.
- Technical Details:
- Persistence: Establishes persistence by creating a Windows service
NetDnsActivatorSharingor modifying theRunregistry key. - Registry Key Modification: Creates
ShowSuperHiddeninHKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advancedto hide files in Windows Explorer. - Configuration Files: Uses encrypted JSON files for:
- Status (
b8b9-de4d-3b06-9d44), - Storing executables (
fb43-138c-2eb0-c651), and - Network information (
130d-1154-30ce-be1e).
- Status (
- Persistence: Establishes persistence by creating a Windows service
- Example: GoldenDealer could be used to install surveillance malware on a voting machine that’s isolated from the internet. By inserting a compromised USB, the malware collects data, which is later exfiltrated when the USB is connected back to an internet-enabled PC.
2. GoldenHowl
- Purpose: A modular backdoor for executing commands on connected systems, with remote control capabilities.
- Functionality:
- Uses Python modules to perform various tasks, such as stealing files, scanning networks, and tunneling over SSH.
- Communicates with a C&C server to receive commands, encrypted with Fernet for security.
- Technical Details:
- Modules: Some key modules include:
sshcmdfor reverse shell connections,eternalbluecheckerto detect SMB vulnerabilities,portscannerandipscannerto scan the local network for open ports and active IPs.
- Directory Structure: Configures directories for C&C communication:
download_dirfor requests,upload_dirfor responses, anddata_dirfor decrypted data.
- Modules: Some key modules include:
- Example: GoldenHowl could be deployed on a sensitive government laptop, where it could scan for important files and run commands remotely, enabling attackers to gather intelligence or propagate the attack within the network.
3. GoldenRobo
- Purpose: Collects specific files from air-gapped systems and exfiltrates them back to the attacker.
- Functionality:
- Searches for files with particular extensions (e.g., .doc, .pdf, .xls) and archives them using
Robocopy. - Uses a USB drive to store collected files and later uploads them when connected to the internet.
- Searches for files with particular extensions (e.g., .doc, .pdf, .xls) and archives them using
- Technical Details:
- File Filtering: Targets sensitive files based on specific extensions like
.docx,.pdf, and.jpg. - Exfiltration: Archives files and sends them to
https://83.24.9[.]124/8102/in a base64-encoded ZIP file.
- File Filtering: Targets sensitive files based on specific extensions like
- Example: An attacker might use GoldenRobo to collect files from a research lab’s isolated computer, targeting sensitive documents for later retrieval when the USB drive is connected to a system with internet access.
4. GoldenUsbCopy
- Purpose: Monitors USB drives for specific files and saves them in encrypted containers.
- Functionality:
- Checks inserted USB drives for files matching criteria in an encrypted configuration (e.g., last modified date or size).
- Encrypts and stores the files in a hidden container for later extraction.
- Technical Details:
- Configuration Encryption: Uses AES with a hardcoded RSA key to encrypt the config file
reports.ini. - File Selection Criteria: Only files with specific extensions or last modified dates are copied.
- Storage Format: Encrypts selected files and stores them in a ZIP container, with AES keys encrypted via RSA.
- Configuration Encryption: Uses AES with a hardcoded RSA key to encrypt the config file
- Example: GoldenUsbCopy could be used in an environment like a corporate network where users frequently transfer files via USB. The tool would collect recently modified files that match specific criteria and save them for later retrieval by the attacker.
5. GoldenUsbGo
- Purpose: A streamlined version of GoldenUsbCopy, used for quick and simple file exfiltration.
- Functionality:
- Operates with hardcoded conditions instead of a config file, targeting files based on extension and file size.
- Compresses and encrypts files with AES, storing them in a specified directory for exfiltration.
- Technical Details:
- Encryption: Uses AES with a fixed key
Fn$@-fR_*+!13bN5in CFB mode. - File Handling: Filters files that contain keywords like “password” or “login” and stores them in
SquirrelCache.dat.
- Encryption: Uses AES with a fixed key
- Example: In an isolated office, GoldenUsbGo could automatically capture files with keywords like “confidential,” compress and encrypt them, and save them to an accessible location for later extraction by the attacker.
6. GoldenAce
- Purpose: Spreads malware and collects data through USB drives, targeting air-gapped systems.
- Functionality:
- Hides malware on USB drives and installs it on systems automatically.
- Uses a lightweight worm component (
JackalWorm) to spread malware.
- Technical Details:
- Persistence: Creates hidden directories on USB drives and uses a batch file (
update.bat) to execute malware. - Infection Process: Changes directory attributes and uses a hidden executable with a folder icon to lure users.
- Persistence: Creates hidden directories on USB drives and uses a batch file (
- Example: In a facility with isolated control systems, GoldenAce could be used to infect these systems via USB drives, executing a payload automatically once the USB is inserted, thus compromising the isolated environment.
7. GoldenBlacklist
- Purpose: Filters out non-relevant emails and archives selected ones for exfiltration.
- Functionality:
- Downloads an encrypted email archive from a local server and decrypts it.
- Filters emails based on blocklists or content types (like attachments).
- Technical Details:
- Email Filtering: Uses a blocklist of sender addresses and looks for emails containing attachments.
- Encryption: Decrypts the initial archive with AES and re-encrypts filtered emails with the same key.
- Example: GoldenBlacklist could be used to target a corporate network where only emails with sensitive attachments are kept for later exfiltration. This helps in reducing the volume of data exfiltrated, focusing only on relevant information.
8. GoldenPyBlacklist
- Purpose: Python-based tool similar to GoldenBlacklist for filtering and archiving emails.
- Functionality:
- Focuses specifically on
.msgfiles (Outlook email format) and adds extra filtering based on file extensions.
- Focuses specifically on
- Technical Details:
- Archive Creation: Uses 7-Zip to archive emails, adding an additional layer of encryption.
- Directory Use: Processes emails in
System32\temp, creating a final encrypted archive namedArcSrvcUI.ter.
- Example: This variant could be used to process a large volume of Outlook emails, extracting only those with attachments like contracts or reports for later transfer to the attacker.
9. GoldenMailer
- Purpose: Exfiltrates stolen files via email attachments.
- Functionality:
- Sends files to attacker-controlled email accounts using legitimate email services (Outlook/Office365).
- Technical Details:
- SMTP Configuration: Stores credentials and configurations in
cversions.ini, and sends emails with attachments. - Email Format: Uses a simple format with hardcoded subjects and a single attachment per email.
- SMTP Configuration: Stores credentials and configurations in
- Example: GoldenMailer could be deployed on a compromised system to send collected documents directly to an attacker’s email address, disguised as routine email traffic.
10. GoldenDrive
- Purpose: Uploads stolen files to Google Drive for remote access by attackers.
- Functionality:
- Uses Google Drive API with hardcoded credentials to upload files one at a time.
- Technical Details:
- Credential Storage: Finds
credentials.jsonandtoken.jsoncontaining client details for Google Drive access. - Upload Process: Handles one file per upload session, minimizing bulk traffic and making detection more difficult.
- Credential Storage: Finds
- Example: An attacker could use GoldenDrive to regularly upload sensitive files from an isolated computer, which would be accessible on their Google Drive account, thus bypassing standard email monitoring systems.
GoldenJackal’s tools leverage USB drives, network scanning, and encrypted communication, demonstrating a sophisticated approach to compromising and exfiltrating data from air-gapped systems. Each tool serves a specific purpose, and together they create a comprehensive toolkit for targeted espionage in sensitive environments.
Implications and Security Concerns
GoldenJackal’s successful infiltration of air-gapped systems underscores a significant threat to government networks and critical infrastructure. By leveraging removable media and creating custom malware optimized for these secure environments, the group demonstrates a high level of sophistication and technical ability. The presence of dual toolsets, which overlap with tools described in past cybersecurity reports, highlights GoldenJackal’s capability to rapidly adapt and refine its methods.
The group’s targeting of governmental and diplomatic entities suggests a focus on espionage, likely with political or strategic motivations. These incidents emphasize the need for advanced security measures, particularly in air-gapped networks often used to protect highly sensitive information.
In light of these findings, cybersecurity experts recommend reinforcing security protocols around removable media, implementing more stringent access controls, and regularly monitoring for indicators of compromise (IoCs). Advanced detection tools and user awareness training are also essential in preventing unauthorized access and mitigating the impact of such sophisticated threats.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.










