Cobalt Strike, a legitimate commercial penetration testing tool, has inadvertently become a favored instrument among cybercriminals for its efficacy in infiltrating network security. Initially released in 2012 by Fortra (formerly known as Help Systems), Cobalt Strike was designed to aid red teams in identifying vulnerabilities within organizational infrastructures. Despite stringent customer screening and licensing for lawful use only, malicious actors have successfully obtained and distributed cracked versions of the software, making it a prevalent tool in cyberattacks involving data theft and ransomware.
Cobalt Strike 4.9 is now available. This release sees an overhaul to Cobalt Strike’s post exploitation capabilities to support user defined reflective loaders (UDRLs), the ability to export Beacon without a reflective loader which adds official support for prepend-style UDRLs, support for callbacks in a number of built-in functions, a new in-Beacon data store and more.
Cobalt Strike 4.9 Features
The latest release, version 4.9, introduces several significant features and improvements:
- User-Defined Reflective Loaders (UDRLs): This feature enhances post-exploitation capabilities by allowing users to define and use their reflective loaders, providing more flexibility and control over the loading process of the Beacon payload.
- Export Beacon Without a Loader: Users can now export the Beacon payload without a reflective loader, which officially supports prepend-style UDRLs, allowing for more versatile deployment and execution of the Beacon payload in various environments.
- Callback Support: Version 4.9 introduces support for callbacks, enabling users to implement and handle custom callback routines effectively.
- Beacon User Data Structures Improvement: These structures have been improved to prevent crashes and provide more stability during operations. They also allow a Reflective Loader to resolve and pass system call information to Beacon, overriding Beacon’s default system call resolver.
- Host Profile Support for HTTP(S) Listeners: This feature addresses limitations in HTTP(S) processing by introducing a new Malleable C2 profile group named
http-host-profiles. - WinHTTP Support: The update adds support for the WinHTTP library to the Beacon’s HTTP(S) listener.
- Beacon Data Store: This feature allows users to store Buffer Overflow Frameworks (BOFs) and .NET assemblies in a structured manner.
Cracked Versions in the Wild
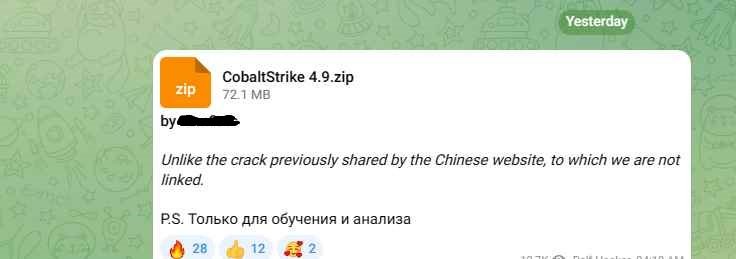
Google researchers have recently identified 34 different cracked versions of the Cobalt Strike hacking toolkit actively being used in the wild. These cracked versions are exploited by cybercriminals for various malicious activities, emphasizing the tool’s popularity and widespread illicit use in the cybercriminal community. The discovery of cracked version 4.9 of Cobalt Strike highlights the significant challenges and risks associated with the illicit use of this powerful toolkit.
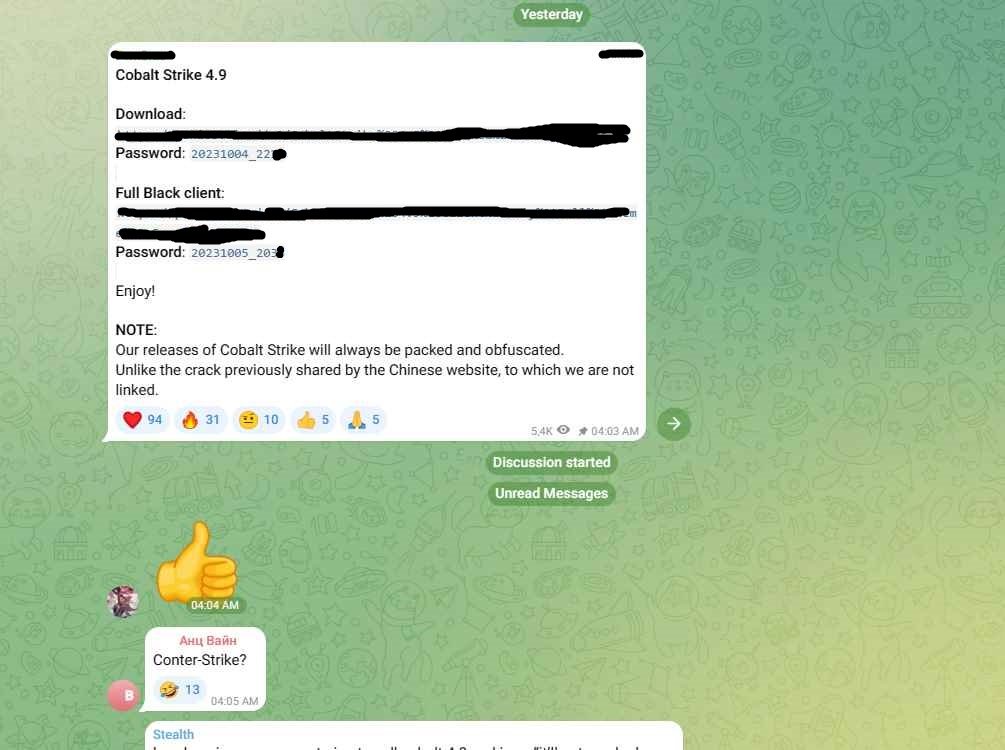
The Crackdown
Microsoft, in collaboration with Fortra and the Health Information Sharing and Analysis Center (Health-ISAC), has initiated a widespread legal crackdown on servers hosting these cracked copies. This concerted effort aims to dismantle the malicious infrastructure and disrupt the operations of threat actors utilizing Cobalt Strike for nefarious purposes.
Why Cobalt Strike?
Cobalt Strike has gained notoriety among cybercriminals for its post-exploitation capabilities. Once the beacons are deployed, these provide persistent remote access to compromised devices, allowing for sensitive data harvesting or the dropping of additional malicious payloads.
The Users
Cobalt Strike’s cracked versions are used by unidentified criminal groups, state-backed threat actors, and hacking groups acting on behalf of foreign governments. These actors have been linked to numerous ransomware attacks impacting various industries, causing significant financial and operational damage.
Remediation Efforts
To counteract the malicious use of Cobalt Strike, various entities have provided resources to assist network defenders in identifying Cobalt Strike components within their networks. These resources include open-sourced YARA rules and a collection of indicators of compromise (IOCs).
The illicit use of Cobalt Strike poses a significant threat to global cybersecurity. The ongoing crackdown led by Microsoft, Fortra, and Health-ISAC represents a crucial step towards mitigating the risks associated with Cobalt Strike, underscoring the importance of collaborative efforts in the fight against cybercrime.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











