When a victim visits a website ending in .ZIP, a recently developed phishing method known as “file archiver in the browser” may be used to “emulate” file-archiving software in the target’s web browser.
According to information published by a security researcher named mr.d0x last week, “with this phishing attack, you simulate a file archiver software (e.g., WinRAR) in the browser and use a.zip domain to make it appear more legitimate,”
In a nutshell, threat actors could develop a realistic-looking phishing landing page using HTML and CSS that replicates genuine file archiving software. They could then host the website on a.zip domain, which would elevate social engineering tactics to a higher level.
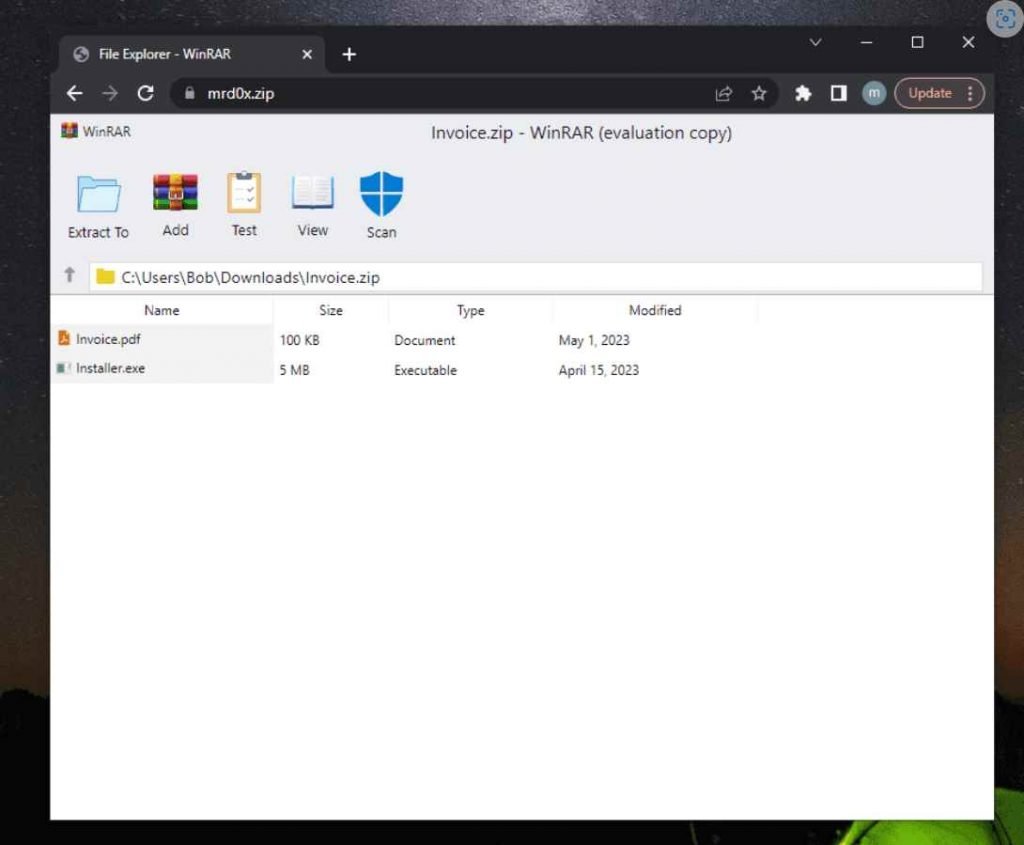
When a user clicks on a file that is “contained” inside the false ZIP package, a malicious actor might exploit this deception to redirect them to a website that collects credentials and use those credentials to gain access to the user’s account.
In addition to this, the search box in Windows File Explorer has the potential to become a deceptive portal via which users may search for a file that does not exist.If the file’s name corresponds to a valid.zip domain, then opening it in a web browser will automatically trigger the opening of the file.
This new information comes at the same time as Google introduced eight new top-level domains (TLDs), some of which include “.zip” and “.mov.” This move has caused some people to express worry that it may encourage phishing and other forms of online fraud.
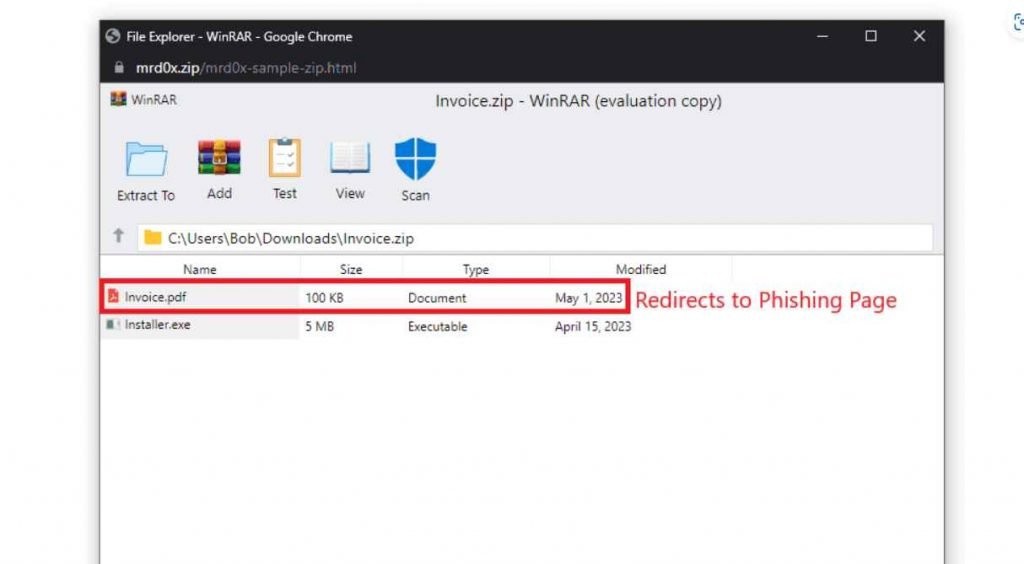
This is due to the fact that .ZIP and .MOV are both valid file extension names, which has the ability to trick unwary users into visiting a malicious website rather than opening a file, which then leads to the user inadvertently installing malware.
Organizations and individual users may defend themselves against attacks that abuse top-level domains (TLDs) by being watchful and exercising care when receiving URLs with unknown top-level domains (TLDs) and avoiding clicking on them unless they are convinced that they are authentic. This protects them from the risk of falling victim to a TLD-based attack. When the mouse cursor is moved over a link, the actual URLs that the links are supposed to go to may be previewed. In addition, businesses and software developers should make sure that their tools, scripts, and apps do not depend on filename extensions but rather verify the file type based on the file headers. If this is not done, a URL might cause undesired or perhaps dangerous behavior from the tools and scripts.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











