Barracuda said that some of its customers who use the Email Security Gateway were affected by a hack that occurred the previous week and took use of a zero-day vulnerability present in the appliance.
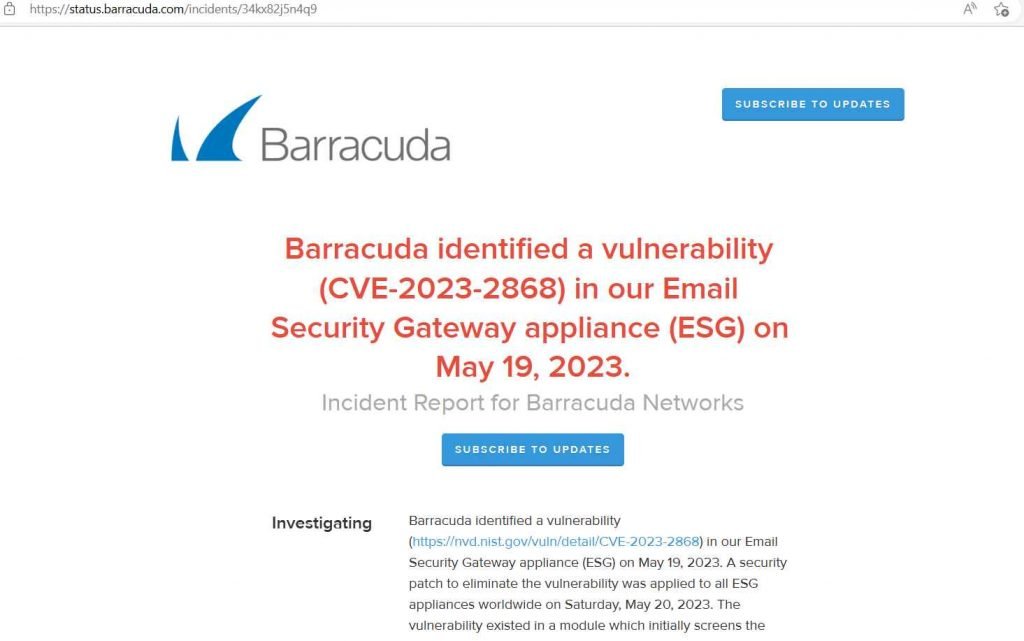
In its announcement, the cybersecurity provider did not provide any information on the number of impacted clients. Barracuda disclosed this information in an article published on Tuesday, stating that the vulnerability was found on May 19, and that the firm applied a fix “to all ESG appliances worldwide” the day after that. On May 21, a second patch was applied to all of the Email Security Gateway equipment that were in use.
According to what has been discovered by the investigation up to this point, the vulnerability “resulted in unauthorized access to a subset of email gateway appliances.” Barracuda has reportedly spoken with all of its affected customers. According to Barracuda, the enterprise-level security solutions it offers are currently employed by more than 200,000 organizations across the globe. These firms include Samsung, Mitsubishi, Kraft Heinz, Delta Airlines, and a number of other well-known businesses.
The vulnerability, which has been assigned the tracking number CVE-2023-2868, is located in the module that is responsible for filtering email attachments.Due to the fact that the affected Email Security Gateway (ESG) appliances are used by hundreds of thousands of enterprises all over the globe, including some prominent companies, the problem has the potential to have a substantial effect.
Other Barracuda products are not affected by the vulnerability, and the business has said that its SaaS email security services are not impacted by this problem.
The organization conducted an investigation into the vulnerability and found that it had been used in an attack against a subset of email gateway equipment. The business informed the clients whose home appliances they believed to be affected by sending a message via the ESG user interface.
Barracuda advised its affected clients in a blog post to “review their environments and determine any additional actions they wish to take.”

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











