Researchers from Tencent Labs and Zhejiang University have collaborated to develop a new technique known as “BrutePrint,” which enables the forcible extraction of fingerprints from modern smartphones. This technique was recently shown to the public.

This approach sidesteps user authentication, therefore providing unauthorized access and complete control over the device that is the focus of the attack.Researchers from China were able to undertake brute-force attacks and acquire unauthorized access to accounts, systems, and networks by effectively circumventing the current security mechanisms on smartphones, such as attempt limitations and liveness detection, by exploiting two zero-day vulnerabilities. This enabled the researchers to gain unauthorized access to accounts, systems, and networks.The following zero-day vulnerabilities have been exploited, and we have listed them below:
Cancel-After-Match-Fail (CAMF)
Match-After-Lock (MAL)
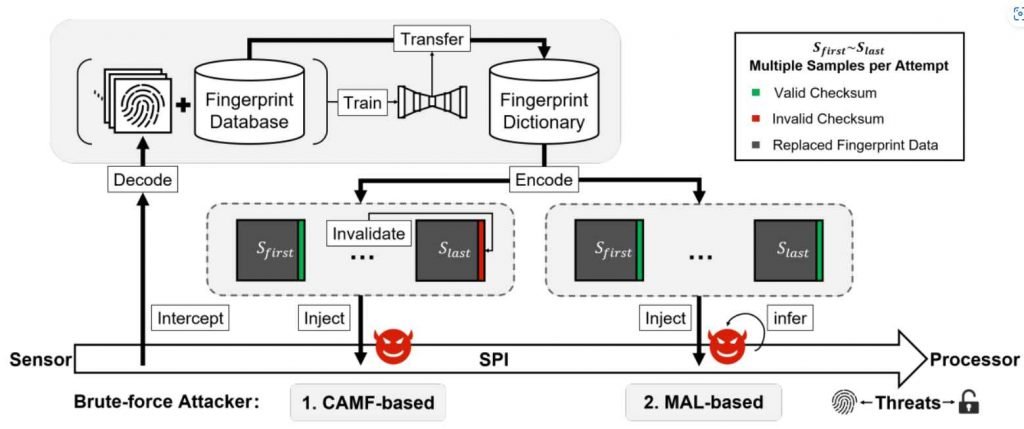
In addition, researchers found a potential vulnerability in the protection of biometric data that was being communicated by fingerprint sensors via the Serial Peripheral Interface (SPI).In order to analyze the efficacy of BrutePrint and SPI MITM attacks, a thorough test was run on 10 different types of smartphones that are quite popular.
The findings showed that these attacks were effective in allowing an infinite number of tries on any Huawei device running Android or HarmonyOS; however, iOS devices indicated a restricted vulnerability, allowing for just an extra 10 attempts to be made.
The primary idea of BrutePrint is to send an unconstrained series of fingerprint image submissions to the device that is being targeted. This process is repeated until a match is discovered with the user-defined fingerprint, and there are no restrictions placed on the number of times the process may be carried out.
An attacker can launch a BrutePrint attack on a target device by first gaining physical access to the device, then gaining access to a fingerprint database, and finally using equipment that costs around $15. This allows the attacker to manipulate the False Acceptance Rate (FAR) in order to increase the acceptance threshold for fingerprint matches and achieve easier unauthorized access.
By exploiting the CAMF issue, BrutePrint injects a checksum mistake into the fingerprint data. This enables it to circumvent security mechanisms and gives attackers the ability to try an endless number of fingerprint matches on smartphones without being discovered.By exploiting the MAL vulnerability, attackers get the ability to determine the authentication results of the fingerprint photographs they test on the target device, even while the device is in a “lockout mode” state of operation.The BrutePrint attack sidesteps the lockout mode by exploiting a process known as MAL. It also makes use of a method known as “neural style transfer” to change fingerprint pictures in the database so that they more closely match sensor scans taken by the target device. This increases the probability that the authentication will be successful.
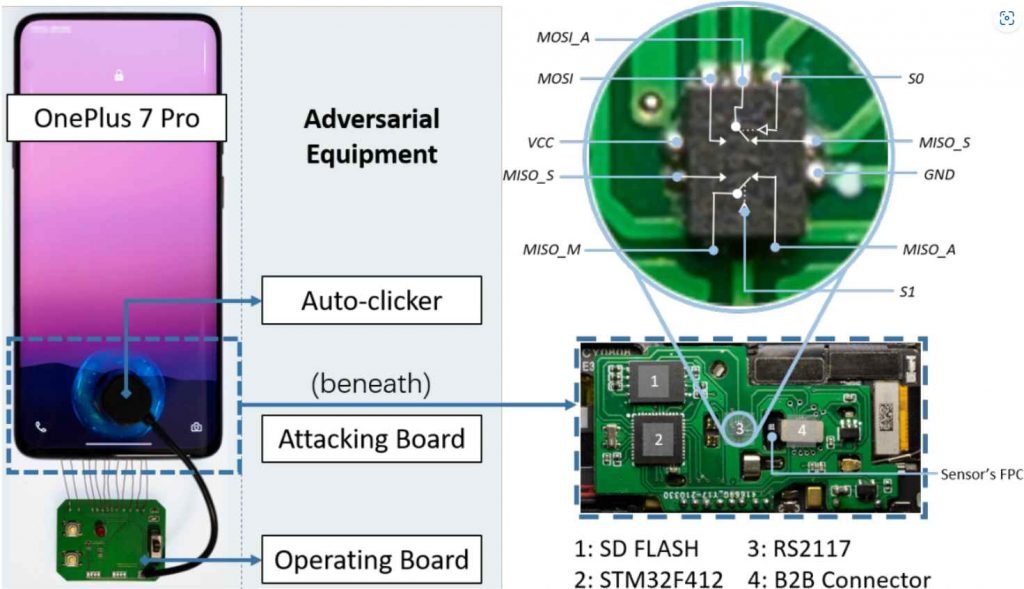
The researchers found that every Android and iOS device they tested had a vulnerability to at least one known vulnerability after running a series of tests on those devices. The tests were carried out on a selection of 10 different mobile devices.
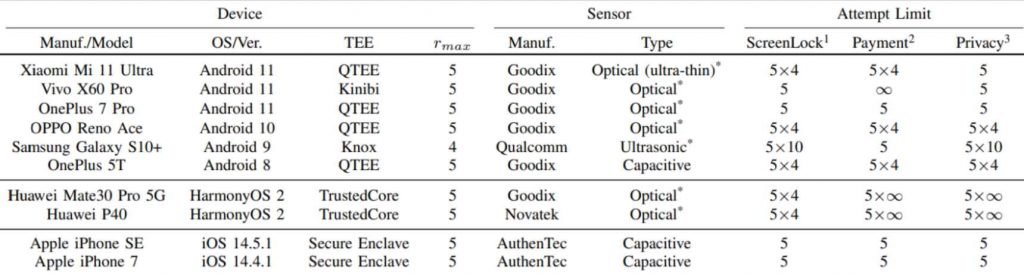
The researchers found that certain iPhone models are susceptible to CAMF, but due to the limited number of fingerprint attempts (up to 15), it is impractical to brute-force the owner’s fingerprint. Additionally, the researchers found that all tested Android devices are susceptible to the SPI MITM attack, with the exception of iPhones, which encrypt fingerprint data on the SPI, rendering any interception ineffective.
BrutePrint may appear to have limitations due to the requirement that it must have prolonged access to the device it is targeting; however, its potential for enabling thieves to unlock stolen devices and extract private data, as well as the ethical concerns and privacy rights implications for law enforcement during investigations, raise significant issues regarding rights violations and the safety of individuals in countries with a dominant political or economic position.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











