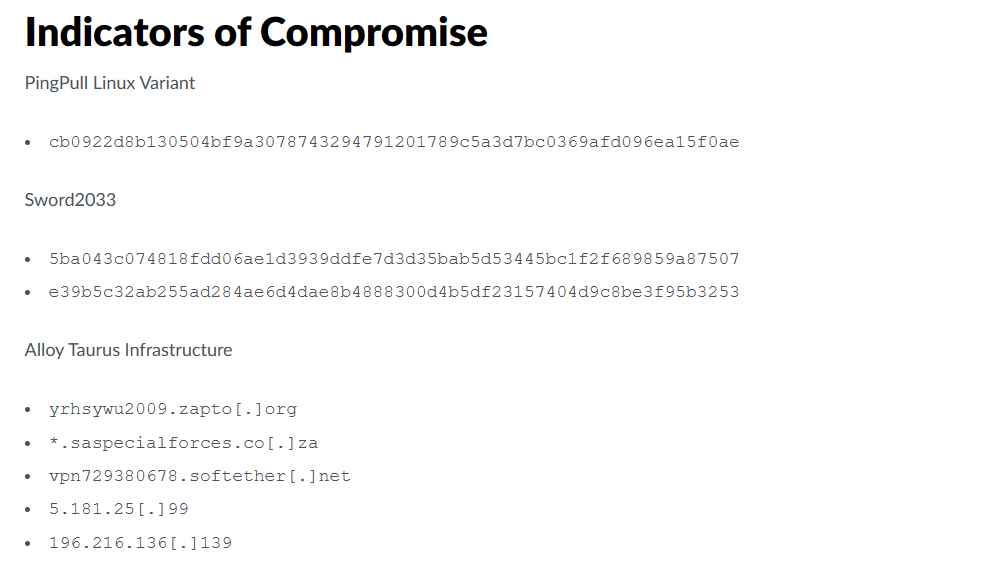
PingPull is a piece of malware that targets Linux computers and is employed by the Chinese advanced persistent threat (APT) organization known as Alloy Taurus. Researchers from Unit 42 have just found a new variation of PingPull. This organization, which is also known as GALLIUM or Softcell, is notorious for carrying out cyberespionage operations against telecommunications corporations, financial institutions, and government bodies located in Asia, Europe, and Africa. The researchers not only found a variation of PingPull, but they also found a backdoor known as Sword2033 that is tied to the same command and control (C2) infrastructure. The first known examples of the PingPull malware were discovered in September of 2021. Unit 42 produced research in June 2022 explaining the operation of PingPull and linked the usage of the tool to Alloy Taurus. This study was based on monitoring the tool’s use throughout many campaigns. There were 62 different vendors, and just three of them deemed the sample to be harmful. In spite of the fact that the decision was mostly positive, subsequent research has shown that the sample in question is in fact a Linux variation of the PingPull virus. The concordance between the HTTP communication structure, the POST parameters, the AES key, and the C2 instructions allowed for this conclusion to be reached.
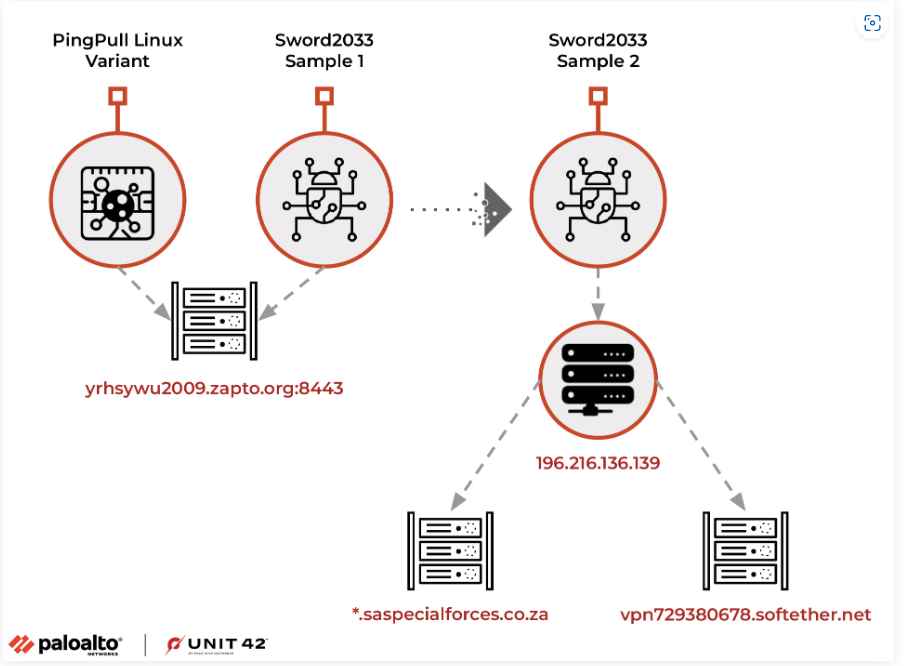
The recently found Linux form of the PingPull virus utilizes a statically linked OpenSSL library and talks with a domain for C2 through port 8443. It uses the same AES key as the original Windows PE form of PingPull and has some characteristics in common with the web shell known as China Chopper. It is possible to upload a file to the system using the Sword2033 backdoor, get a file from the system using the Sword2033 backdoor, and execute a command using the Sword2033 backdoor. The investigation into the C2 domain uncovered connections to the actions of Alloy Taurus, including proof that the domain impersonated the South African military. This impersonation is especially noteworthy since it took place during the month of February 2023, when South Africa took part in joint naval drills with Russia and China.
In addition, the researchers discovered persistent connections between the Sword2033 C2 server and the IP hosting subdomains for an organization that finances extended-term urban infrastructure development projects in Nepal. This finding sheds light on the continuous danger presented by the Alloy Taurus gang and stresses how important it is for businesses and other organizations to maintain a diligent vigilance in their cybersecurity operations.
It is important to note that Alloy Taurus continues to pose a serious risk to governmental, financial, and telecommunications institutions across Southeast Asia, Europe, and Africa. The discovery of a Linux edition of the PingPull virus, together with the recent usage of the Sword2033 backdoor, hints that the gang is continuing to develop its operations in order to assist their spying endeavors. We strongly recommend that all companies make use of our results in order to advise the implementation of defensive measures in order to defend themselves against this danger group.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











