Security researchers have discovered yet another sizable haul of malicious packages on the open source registries npm and PyPI. These packages, which could cause problems if developers downloaded them without realizing it, can be found here. It comes with a number of different packages, all of which contain the same malicious package. go file is a Trojan horse programme that was developed to mine cryptocurrency on Linux computers. According to Sonatype, sixteen of these were able to be traced back to the same actor known as trendava, who has since been removed from the npm registry.
Other discoveries include something called PyPI malware “minimums,” which is programmed to look for the presence of a virtual machine (VM) before carrying out its intended function. The goal is to thwart the efforts of security researchers, who frequently test suspected malware in virtual machines (VMs), in order to learn more about the danger.
The total number of packages that have been identified as malicious, suspicious, or proof-of-concept since 2019 has nearly reached 107,000 thanks to the discoveries made by the company’s AI tooling.
A new piece of Python malware with capabilities combining those of a remote access tool (RAT) and information stealer was also found by the security vendor.
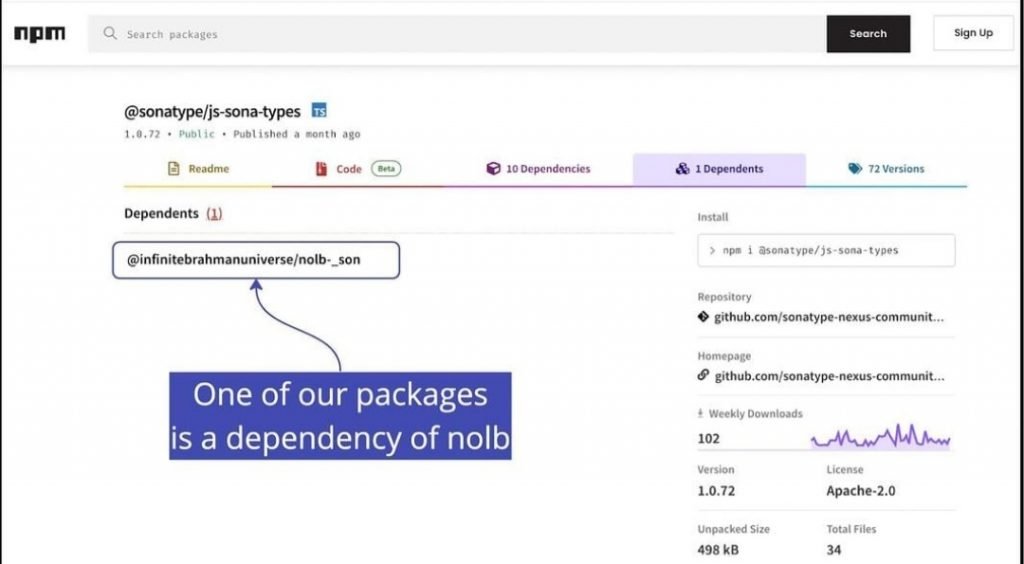
Last but not least, it discovered a developer with a dubious appearance who went by the name “infinitebrahamanuniverse” and uploaded more than 33,000 packages that described themselves as sub-packages of “no-one-left-behind” or “nolb.” The latter was taken off the market a week ago after it was discovered by the npm security team that it was dependent on every other npm package that was publicly available. Now take into consideration a malicious actor who is exploiting this dependency in order to launch an attack. This threat actor can launch a Denial of Service (DoS) attack against a company’s download channel by adding it to a typosquatting package. This attack can waste the time of developers by forcing them to wait for their npm environment to be ready. The installation of a package that has this dependency can also result in an excessive consumption of resources. If you have been following along with this series, you should already be aware that the events depicted here are not completely implausible.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











