Access to many operating systems may be accomplished on a single server by using VMware’s ESXi servers. According to a story that was published by Reuters on Tuesday, some of the victims of ESXiArgs ransomware included the Supreme Court of Florida, the Georgia Institute of Technology, Rice University, and other colleges located in Hungary and Slovakia. On Friday, officials in charge of European cybersecurity started issuing warnings about “large active network exploitation.” Over the course of the weekend, the National Cybersecurity Agency (ACN) of Italy joined the computer emergency response team (CERT-FR) of France and the Cybersecurity Center of Finland in issuing warnings on the campaign. The ESXiArgs ransomware has been wreaking havoc on enterprises all across the globe since last Friday. The Cybersecurity and Infrastructure Security Agency has provided a procedure for retrieving data for organizations that have been hit by the ransomware. The
On the evening of Tuesday, February 12, CISA posted a message on its GitHub website advising victims to analyze the script before using it to attempt to restore access to impacted files. The script was adapted from the efforts of two Turkish software engineers, who earlier this week published a comprehensive how-to guide.
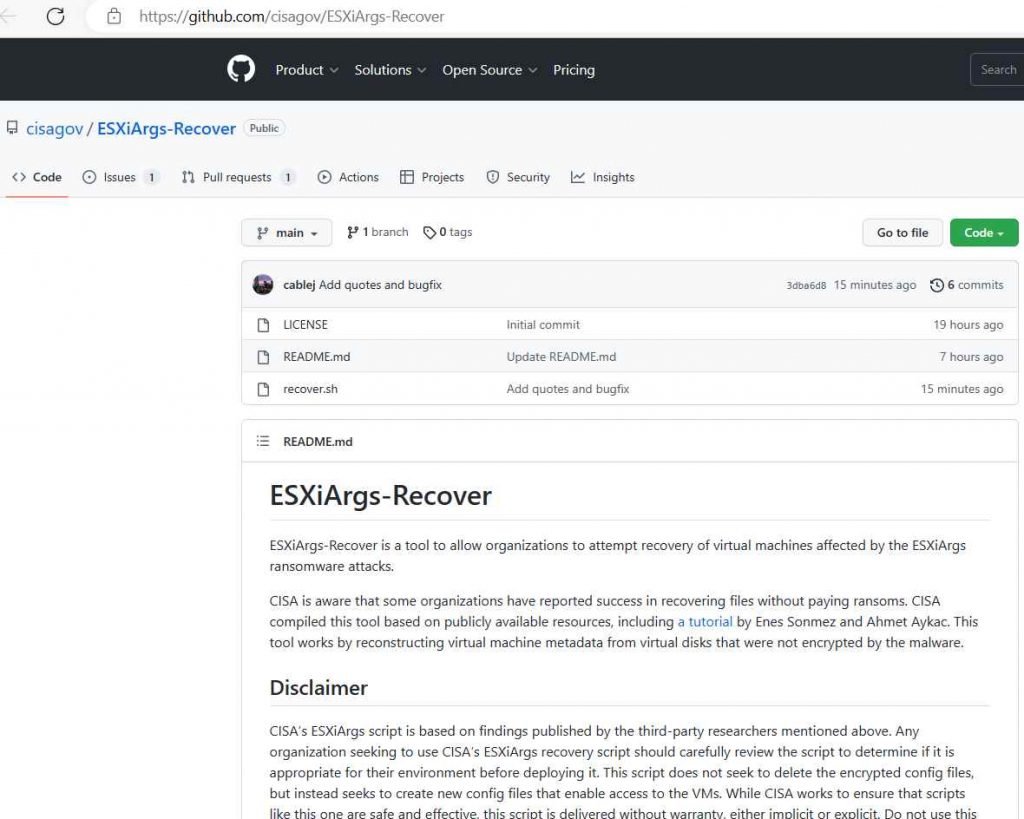
The ransomware takes use of a weakness that has been present in VMWare servers for the last two years (CVE-2021-21974), and it has already encrypted the data of more than 3,800 businesses in a variety of countries, including the United States, France, Italy, and others. In the year 2021, the firm released a patch. The ESXiArgs ransomware has been wreaking havoc on enterprises all across the globe since last Friday. The Cybersecurity and Infrastructure Security Agency has provided a procedure for retrieving data for organizations that have been hit by the ransomware.
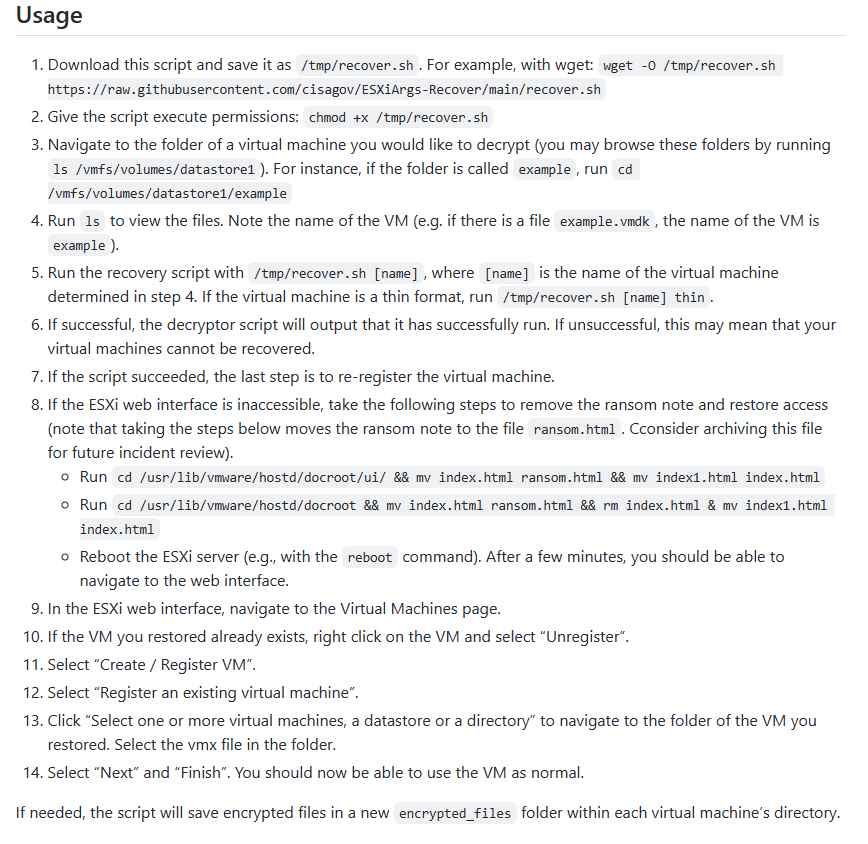
In light of the fact that VMWare released a patch for CVE-2021-21974 in February 2021, a number of other industry professionals have said that the debacle demonstrates how many firms struggle to apply patches in a timely manner.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











