BlueNoroff is a part of the infamous Lazarus Group, and it has been detected incorporating new strategies into its playbook. These new strategies allow BlueNoroff to circumvent the defenses provided by Windows Mark of the Web (MotW).
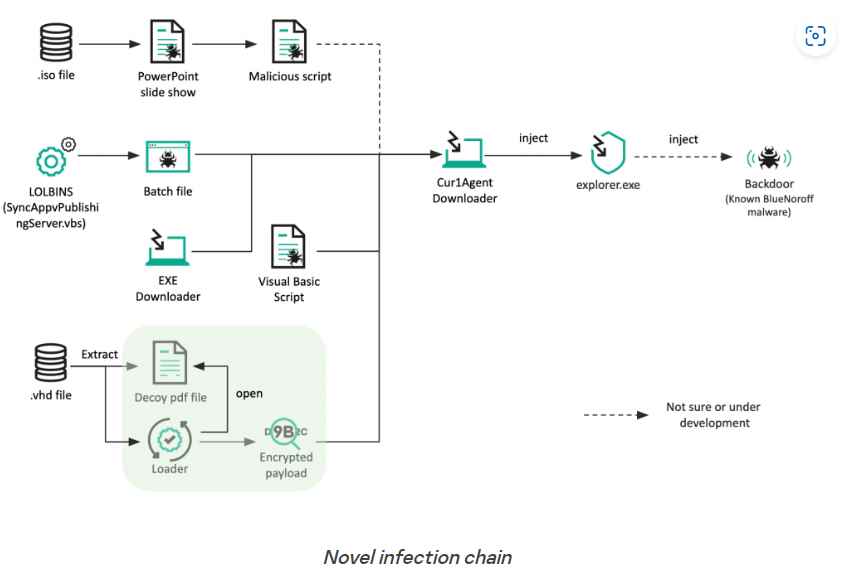
According to a research that was released today by Kaspersky, this involves the usage of file formats with an extension of .ISO for optical disk images and .VHD for virtual hard disks as part of an unique infection chain.
AppleJeus is an additional significant activity that has been connected to the organization. In this scheme, bogus cryptocurrency firms are established to entice victims into downloading programs that seem to be harmless, but they ultimately get backdoored upgrades.
The most recent malicious activity discovered by the Russian cybersecurity organization makes some minor adjustments to the way it delivers its final payload. Specifically, it replaces the attachments of Microsoft Word documents with ISO files in spear-phishing emails in order to activate the infection.
These optical image files, on the other hand, include a slide show created in Microsoft PowerPoint (.PPSX) as well as a Visual Basic Script (VBScript) that is activated when the target hits a link contained inside the PowerPoint file.
BlueNoroff, also known as APT38, Nickel Gladstone, and Stardust Chollima, is a member of the wider Lazarus threat group, which also includes Andariel (also known as Nickel Hyatt or Silent Chollima) and Labyrinth Chollima. BlueNoroff is a member of the Lazarus threat group (aka Nickel Academy).
The financial goals of the threat actor, as opposed to espionage, have made it an atypical nation-state player in the threat environment. This has enabled it to have a “wider geographic spread” and to penetrate organizations in North and South America, Europe, Africa, and Asia.
Since then, it has been linked to high-profile cyberattacks that were directed against the SWIFT financial network between 2015 and 2016, such as the daring Bangladesh Bank robbery that occurred in February 2016 and resulted in the loss of $81 million.
BlueNoroff established a large number of bogus domains, some of which impersonated banks and others venture capital firms.
Some of the fake domains have been identified to replicate legitimate companies such as ABF Capital, Angel Bridge, ANOBAKA, Bank of America, and Mitsubishi UFJ Financial Group. The majority of these legitimate companies are based in Japan, which indicates a “strong interest” in the area.
This organization is driven mostly by financial concerns and is genuinely successful at turning a profit from the hacks they launch.
The fact that one of the lure documents had Japanese file names, in addition to the fact that fake domains were created and disguised as legal Japanese venture capital businesses, is evidence that BlueNoroff most likely targets financial institutions located in the island nation of Japan.
North Korea’s reaction to the economic restrictions put on it by the United Nations and a number of other nations because of concerns about its nuclear programs has been to place a significant emphasis on its cyber warfare capabilities. Additionally, it has been an important source of revenue for the cash-strapped nation as of late.
According to the National Intelligence Service (NIS) of South Korea, state-sponsored hackers from North Korea are believed to be responsible for the theft of approximately $1.2 billion worth of cryptocurrency and other digital assets from targets located all over the world over the course of the past five years.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











