The use after free vulnerability, which is linked to ksmbd, affects computers running Linux distributions powered by kernels earlier than 5.15.61. This leaves susceptible systems open to cyberattacks from a remote location. SMB servers that have ksmbd enabled are vulnerable to hacking due to a serious vulnerability in the Linux kernel (CVSS score of 10). KSMBD is a file-sharing server for the Linux kernel that implements the SMB3 protocol in the kernel space. It enables users to transfer files across a network. Installations of the Linux Kernel that are susceptible to attack may have arbitrary code executed on them by an attacker who is not authorized remotely. It is an implementation of the SMB/CIFS protocol in the kernel space that allows for the sharing of IPC services and files over a network. The first aim is to enhance file I/O speed, but the overarching objective is to have certain new features that are much simpler to build and maintain within the kernel, as well as completely expose the layers.
The processing of SMB2 TREE DISCONNECT instructions is where the security weakness may be found.
“Any arbitrary code may be executed by remote attackers thanks to this vulnerability, which affects certain installations of the Linux Kernel. Exploitation of this vulnerability does not need authentication; nonetheless, the vulnerability is only present on systems that have ksmbd enabled. reads the advice that was just released by ZDI. “The exact flaw may be found in the processing of SMB2 TREE DISCONNECT instructions,” the researcher said. The problem stems from the fact that there was no attempt made to verify that an object really existed before conducting actions on the object. This vulnerability allows an attacker to execute code in the context of the kernel, which may be exploited by the attacker.
Late in the month of July, the engineers working on the Linux kernel released a patch to address the problem of remote code execution, and they patched the vulnerability in the Linux kernel version 5.15.61.
According to the researcher Shir Tamari, who is the Head of Research at Wiz IO, SMB servers that use Samba are not impacted. However, he stated that SMB servers that use ksmbd are susceptible to read access, which might result in memory leakage on the server.
Another vulnerability that allows for the remote execution of code exists in the Linux kernel (ZDI-22-1688). This vulnerability likewise affects ksmbd and was given a high severity base score of 8.5 by NIST’s NVD. To take advantage of this vulnerability would need authentication.
These three flaws have the potential to cause information disclosures as well as service disruptions:
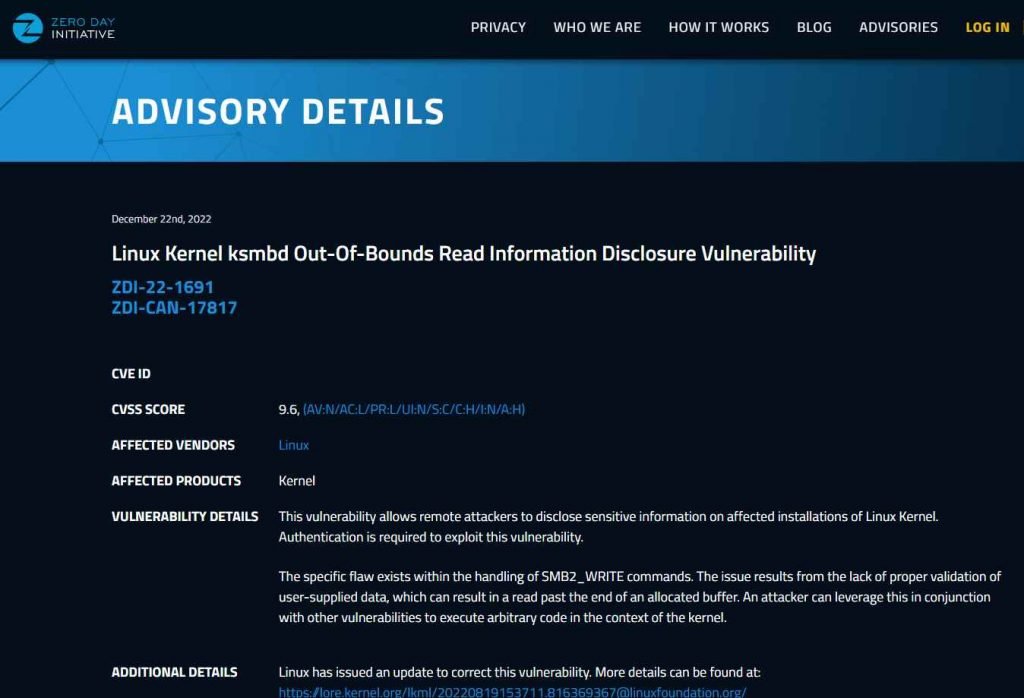
ZDI-22-1691 is a Linux Kernel ksmbd Out-of-Bounds Read Information Disclosure Vulnerability with a CVSS score of 9.6.
ZDI-22-1689 is an Out-Of-Bounds vulnerability in the Linux Kernel ksmbd (CVSS score: 6.5). Please refer to the Denial-of-Service Vulnerability report.
Memory exhaustion denial-of-service vulnerability was discovered in the Linux Kernel ksmbd (ZDI-22-1687; CVSS score: 5.3).
If you have previously installed the Linux kernel 5.15.61 versions and applied the commit, then an attack that takes use of these vulnerabilities will not be able to compromise your device.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











