Two vulnerabilities in Cisco’s product line, including high-severity flaws in the Cisco Email Security Appliance, Cisco Secure Email and Web Manager, and Cisco Secure Web Appliance Next Generation Management products, have been patched, according to Cisco.
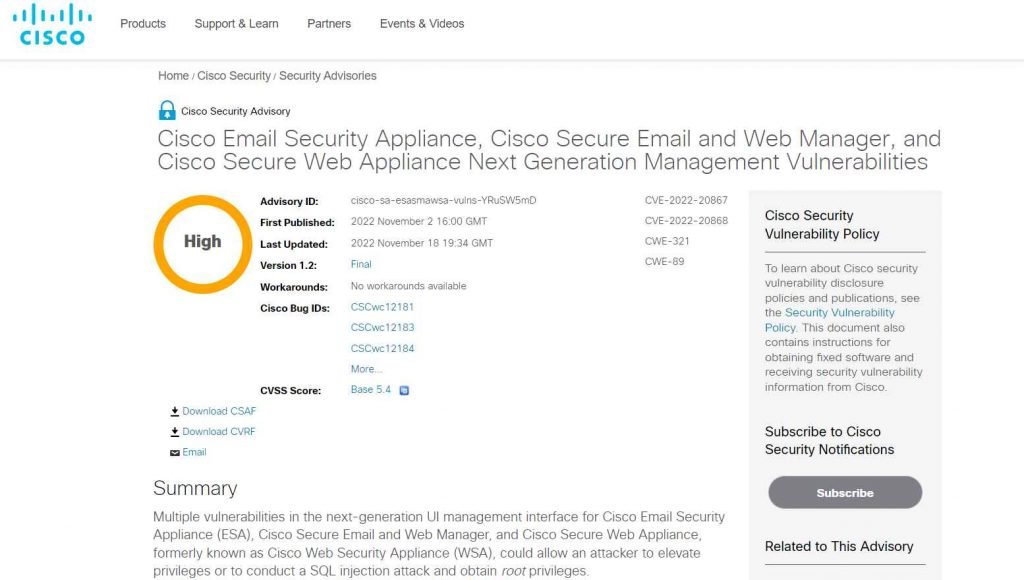
A SQL Injection vulnerability known as CVE-2022-20867 (CVSS score: 4.7) affects Cisco ESA and Cisco Secure Email and Web Manager Next Generation Management. Because the vulnerable devices’ next-generation UI administration interfaces for Cisco ESA, Cisco Secure Email, and Web Manager do not validate user-submitted parameters, a problem occurs.
Additionally, Cisco released fixes for CVE-2022-20868, a security flaw that affects Cisco ESA, Cisco Secure Email and Web Manager, and Cisco Secure Web Appliance Next Generation Management (CVSS score: 5.4). An authorized, remote attacker could be able to increase their privileges on a weak system thanks to the issue.
An independent security researcher who collaborated with SSD Secure Disclosure found the flaws. A security researcher recently published two in-depth studies on the flaws and exploit code that revealed the technical information about the vulnerabilities. Since the attacker would need to be authenticated for CVE-2022-20868, the impact isn’t as severe.
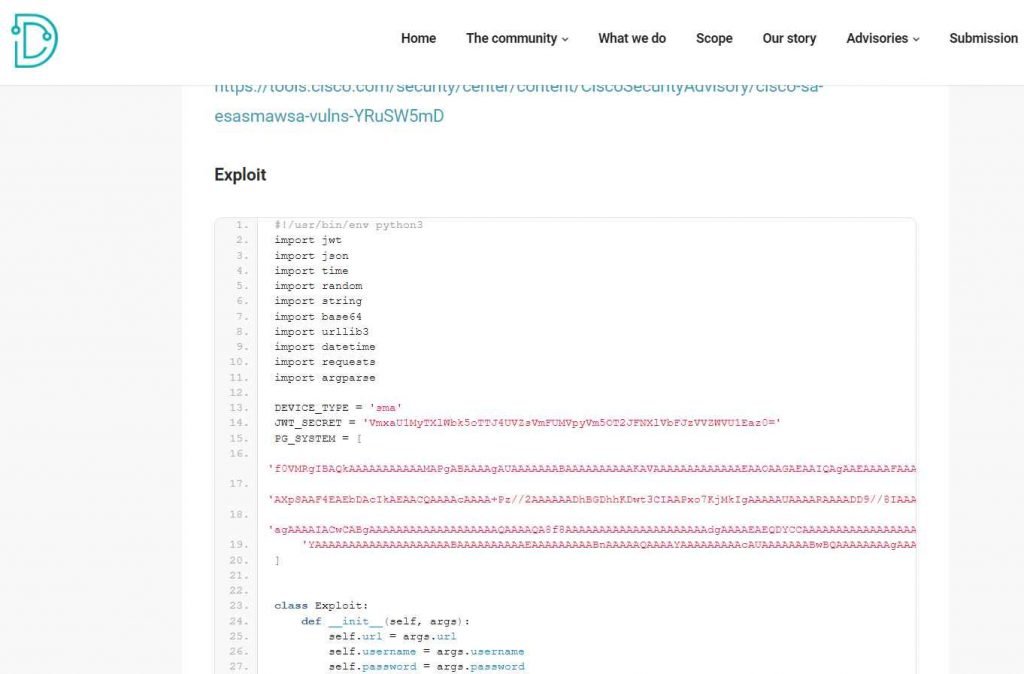
There is no connection between these vulnerabilities. It is not necessary to exploit one vulnerability in order to exploit the second vulnerability. By combining the two flaws, a user with low privileges can get complete administrative access to a vulnerable system.
On vulnerable installations of the Cisco Secure Manager Appliance and Cisco Email Security Appliance, remote attackers are able to raise their privileges using this exploit. In order to exploit this flaw, authentication is needed.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











