Microsoft’s Dynamics 365 Customer Voice is a software that is primarily used to collect customer feedback.
It may be utilized to gather data into actionable insights, track consumer feedback, and conduct polls of client satisfaction.
To communicate with victims, hackers are exploiting the Static Expressway. In a nutshell, it’s a method for evading security scanners that makes use of reliable websites. According to this reasoning, security services cannot simply ban Microsoft since it would be unable to do any tasks. Instead, people tend to immediately believe these connections from reliable sources. As a result, hackers now have a place to insert themselves.
Hackers are using genuine links from Microsoft notifications in this attack to transmit sites that collect login credentials. In the past two weeks, Avanan has witnessed hundreds of similar assaults.
For example in this is an official Microsoft Customer Voice link. Scanners will believe that this email is valid because the URL is authentic. But when you press the “Play Voicemail” button, hackers are waiting with greater cunning. The email’s purpose is to click on the “Play Voicemail” button, which leads to a phishing site rather than the voicemail itself. When you click on the voicemail link, a fake Microsoft login page is shown. The threat actors take your account and password at this point. Observe how the URL differs from the original one.
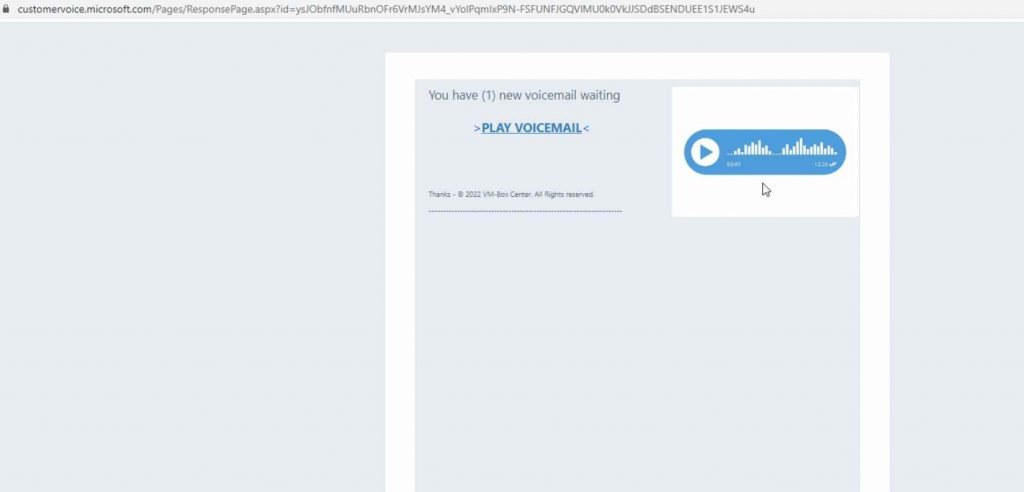
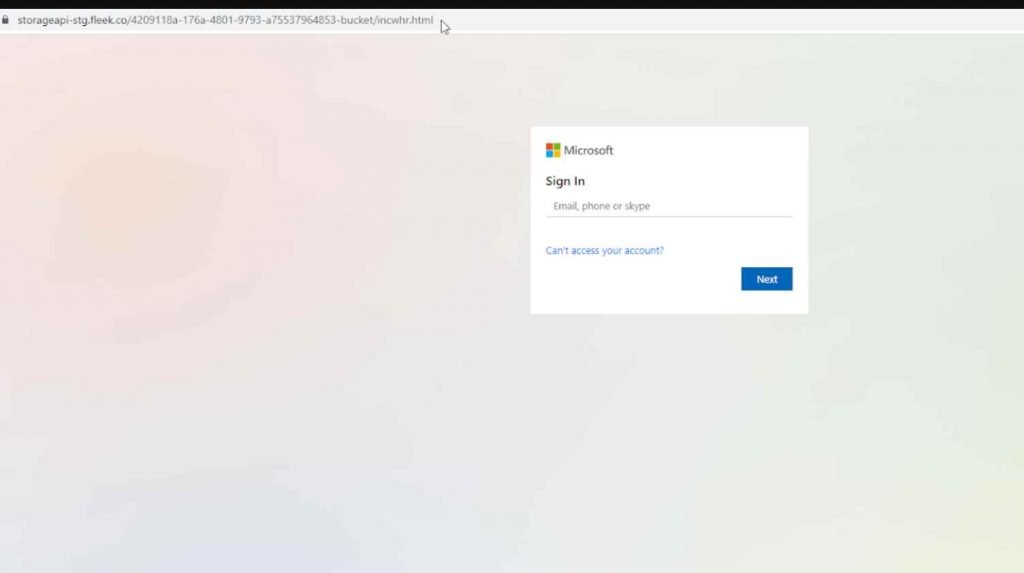
Security tools have a very tough time distinguishing between what is real and what is hidden behind a legal connection. Additionally, many services default to skipping a scan when they encounter a known-good link. Why scan quality content? Hackers are hoping for it to happen.
Due to the fact that the phishing link doesn’t show until the very last stage, this attack is exceptionally challenging. Hovering over the URL in the email body won’t offer protection because users are first sent to a reliable website. It would be crucial to remind users to check all URLs in this situation, even if they are not in an email body.
Scanners find it extremely challenging to block these assaults, and users have much more difficulty identifying them.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











