The OverlayFS file system implementation in the Linux kernel is where the vulnerability, CVE-2021-3493, exist. Although it only seems to impact Ubuntu, it allows a local user without administrative rights to get root access. The vulnerability is now included in CISA’s “Known Exploited Vulnerabilities Catalog,” and government entities have until November 10 to fix their systems. Although fixing these problems is mandatory for government agencies under a binding operational mandate, CISA recommends all enterprises to make patching for vulnerabilities in its database a top priority. A stealthy Linux virus called Shikitega has successfully attacked CVE-2021-3493 in the wild. Two Linux vulnerabilities—CVE-2021-3493 and CVE-2021-4034—are used for privilege escalation as a component of the malware’s infection chain.
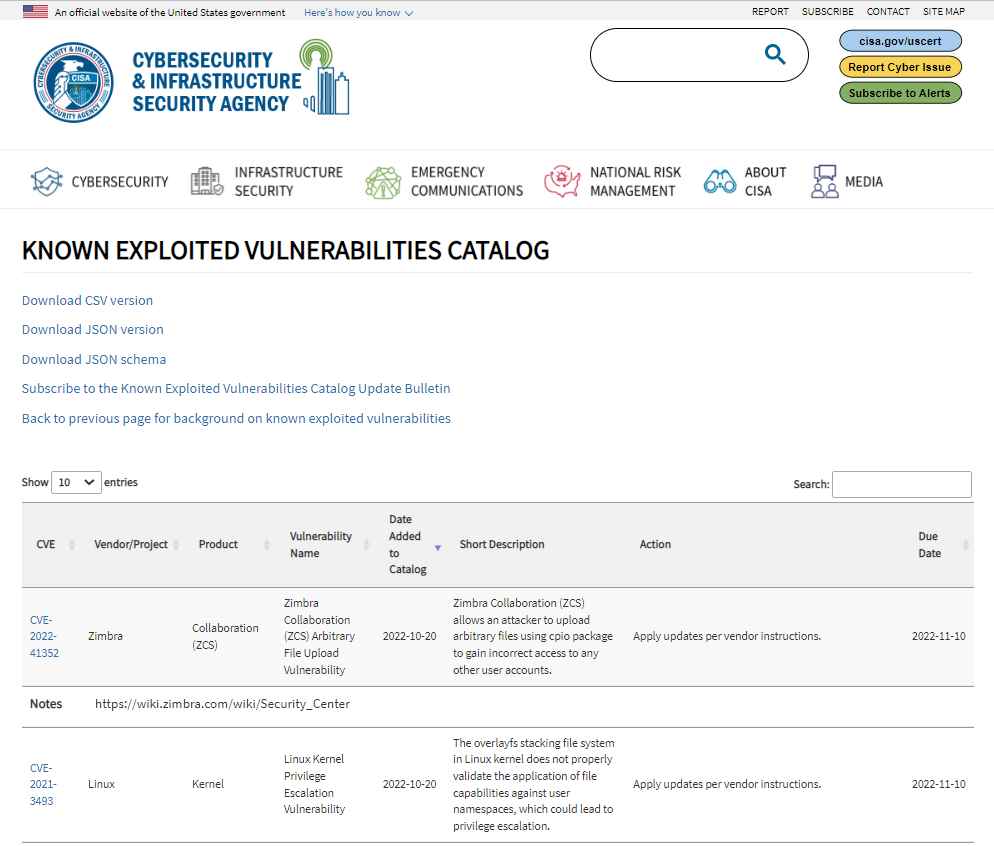
PwnKit, also known as CVE-2021-4034, affects Polkit’s Pkexec, an SUID-root software that is included in all Linux variants. When Shikitega’s existence was revealed, press stories centered on the malware rather than the fact that this could have been the first known case of CVE-2021-3493 being used maliciously.
Users and administrators were recommended by CISA and the MS-ISAC to implement mitigations to protect their organization’s systems from hostile cyber activity. In order to lower the possibility of compromise, it also suggested the following best practices:
Keep an incident response strategy current and test it.
Make sure your company has a vulnerability management program in place, and that it gives patch management and vulnerability screening for known exploited vulnerabilities top priority.
Disable unwanted or superfluous network ports and protocols, as well as disable/remove unused network services and devices. This will prevent management interfaces from being exposed to the internet.
Use zero-trust architecture and concepts, such as micro-segmenting networks and features, phishing-resistant multi-factor authentication (MFA) for all users, and restricting access to trusted devices and virtual private networks (VPNs).

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











