Twelve new security flaws impacting various chipsets were disclosed in this month’s security advisory for Qualcomm’s devices, two of which have been given a critical severity rating.
Two significant flaws in Qualcomm chipsets have been identified that might allow malicious payloads to installed remotely on the Android devices.
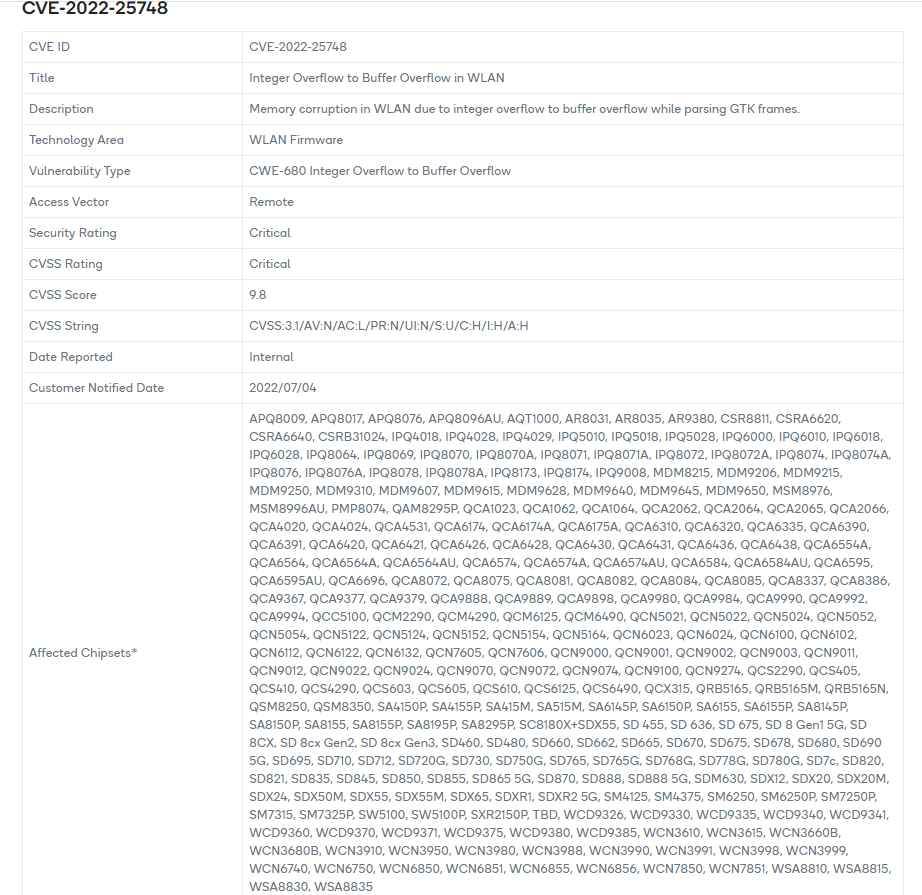
The first vulnerability, identified as CVE-2022-25748 (CVSS score 9.8), affects Qualcomm’s WLAN component and is described as a “Integer Overflow to Buffer Overflow during parsing GTK frames” . If exploited, this issue might result in memory corruption and remote code execution. This vulnerability impact all smart devices that use the Qualcomm Snapdragon APQ, CSRA, IPQ, MDM, MSM, QCA, WSA, WCN, WCD, SW, SM, SDX, SD, SA, QRB, QCS, QCN, and more series.
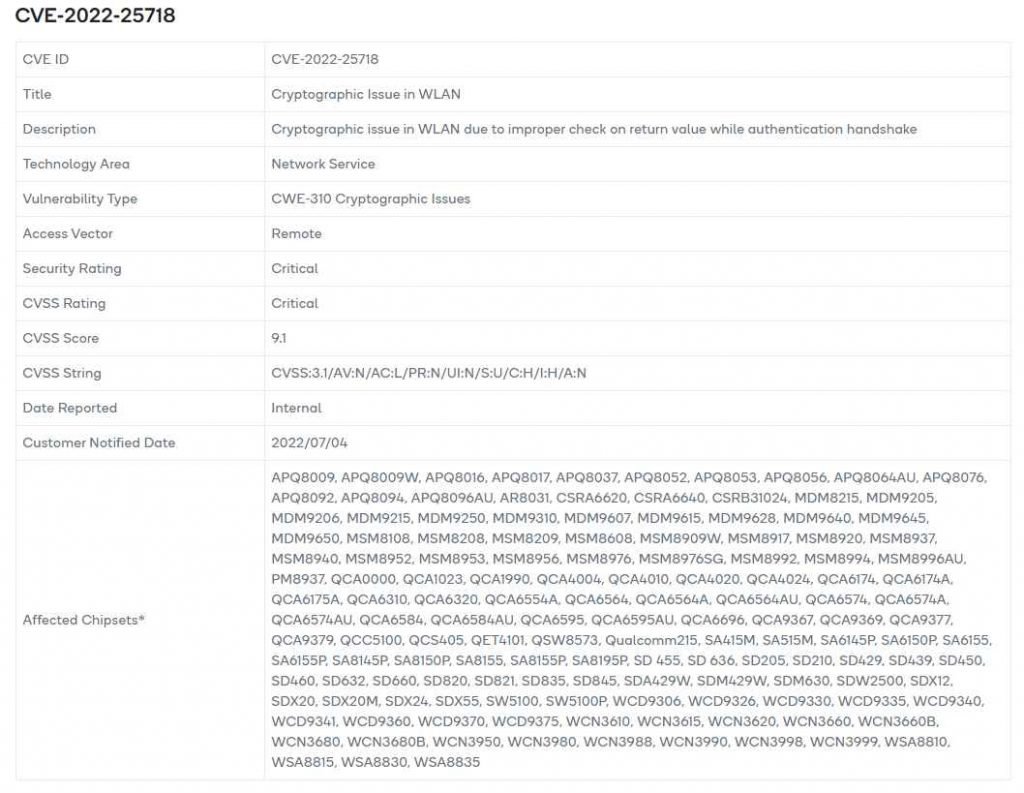
The second vulnerability, identified as CVE-2022-25718 (CVSS score 9.1), also affects Qualcomm’s WLAN component and is described as a “Cryptographic issue in WLAN due to improper check on return value while authentication handshake” . If exploited, this issue might result in memory corruption and remote code execution. This vulnerability impact all smart devices that use the Qualcomm Snapdragon APQ, CSRA, IPQ, MDM, MSM, QCA, WSA, WCN, WCD, SW, SM, SDX, SD, SA, QRB, QCS, QCN, and more series.
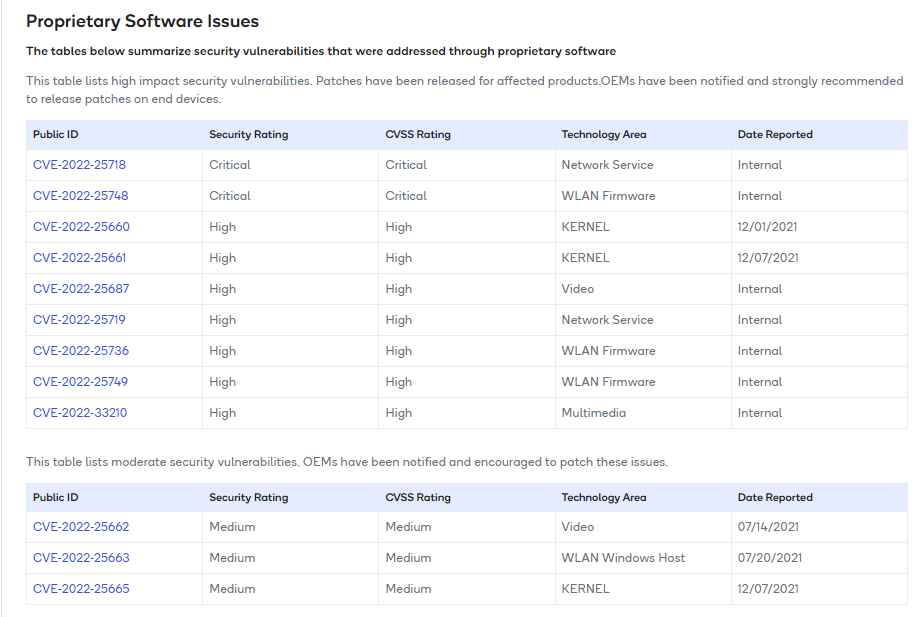
The Android Security Patch for October 2022 addressed CVE-2022-25718, CVE-2022-25748, CVE-2022-25660, CVE-2022-25661, CVE-2022-25687, CVE-2022-25736, and CVE-2022-25749.
The most recent Android security updates should always be downloaded by consumers as soon as they become available in order to keep their Android devices safe from any potential threats.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.










