Zoom announced that it published an update (5.11.5) of its video call app that corrects a security flaw in its version for Mac computers. They explained that the vulnerability in the program’s source code allowed cybercriminals to access the computer and take control of it from a distance.
The Zoom code bug was nothing new as detailed by cybersecurity expert Patrick Wardle, who exposed the flaw during a computer security event called Def Con last week.
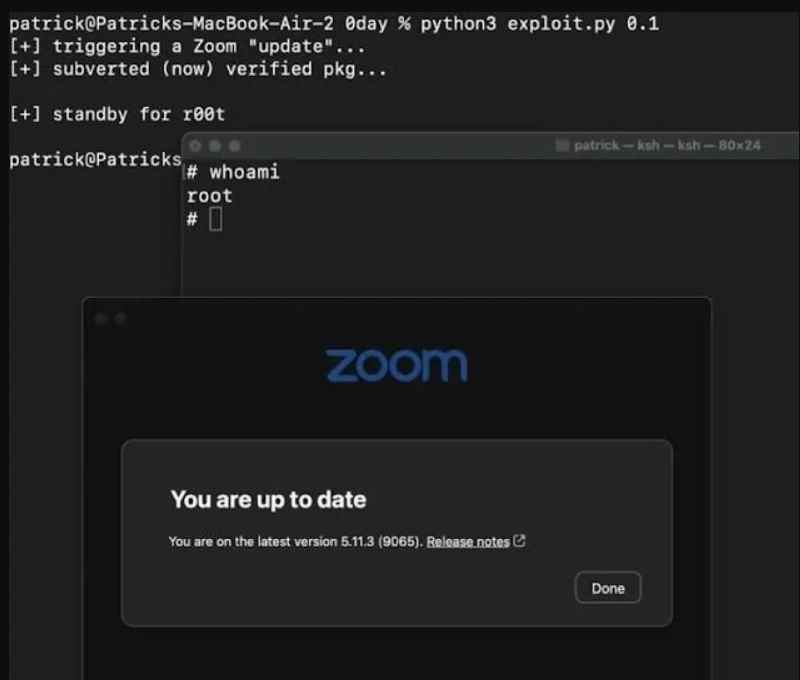
Wardle points out that the problem had its origin in the Zoom installation program, which at the time of starting to operate asks the user to enter their personal password in order to have the necessary permissions. It is at this moment that the program starts running a subroutine in the background that has superuser privileges.
In practical terms, this means that the program has sufficient permissions to be able to access and modify any aspect of the computer.
This, according to the expert, opens the possibility of a “privilege escalation attack”, in which hackers can gain control of a superuser with which they can even delete their victim’s user if they wish.
The update published by Zoom shows that the claims made by Wardle could be true and therefore that thousands of Mac users were in danger for an undetermined time. That is why it is complex to estimate the scope of the failure and to be able to know how many users could be affected by this situation.
Likewise, it is also unknown if the hackers were aware of this security flaw and had been using it until now.
Version 5.11.5 can be downloaded both from the Zoom website and from the application itself. To do this ,it is only necessary to start the app and it should automatically show a pop-up text box indicating that there is a new version available and ask if you want to download it, to which the user must accept.
Once this is done, the system will download and install the update completely automatically.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











