Those responsible for AstraLocker ransomware have decided to end its life cycle. Therefore, no more actions will be carried out with it and, in addition, they have published the necessary keys so that their victims can recover their assets. These were sent by one of AstraLocker’s people to cyber security researchers and they have verified that they are authentic and that they work.
Although it is not the most common, from time to time we hear that some group dedicated to ransomware, for whatever reason, decides to shut down and cease all operations. This is likely when a police operation takes place that allows one of these organizations to be shut down, since although the number of gangs that continue to operate is enormous, and new actors are added every week, one less threat is always One less item to worry about.
And the news is even better if the cessation of activity, whether voluntary or involuntary, is accompanied by the publication of the decryption keys, so that all those who have been victims of said ransomware, have refused to pay and still have encrypted assets, can finally get them back. A hope that, although unlikely, is fulfilled from time to time, either by an unexpected blow of goodwill by its creators, by police investigations or by the work of the community of security experts.
Using these keys, the cybersecurity firm Emsisoft has released a free decryption tool to help AstraLocker and Yashma ransomware victims recover their files without paying a ransom. The free tool is available for download from Emsisoft’s servers, and it allows you to recover encrypted files using easy-to-follow instructions. You can use this tutorial here to decrypt your file.
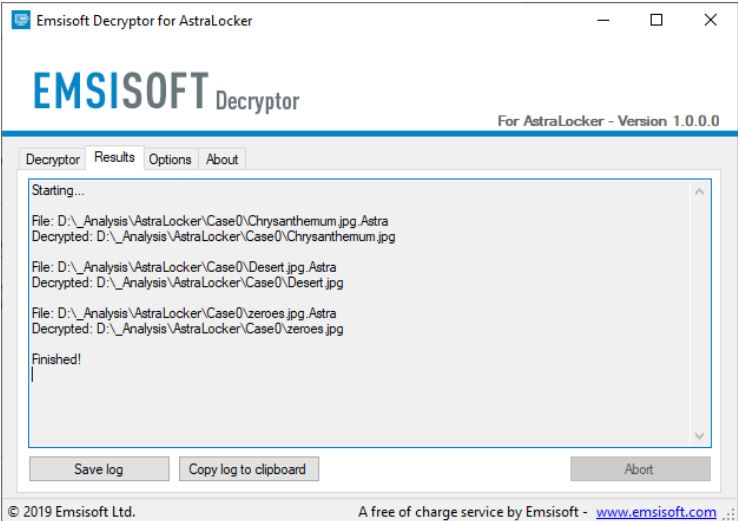
AstraLocker had recently gained popularity, which on the one hand can be considered a success but which also implies a higher level of attention on the part of investigators, police and judicial entities, etc. and, therefore, a greater risk of also ceasing activity, but in this case due to force majeure. As per the message the gang will be to cryptojaking , to other areas of cybercrime or returning to ransomware. We hope that, at least, that return to activity will take place as late as possible.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











