Software development and testing platform Travis CI confirmed the second incident of exposing its users’ data in less than a year. On this occasion, the compromised records include authentication tokens that would allow access to platforms such as AWS, GitHub, and Docker Hub.
According to a report prepared by the firm Aqua Security, tens of thousands of user tokens would have been exposed through the Travis CI API, which contains more than 770 million records with multiple types of credentials belonging to users of free subscriptions.
According to the report, Travis CI did not apply sufficient protections for record numbers, which would allow the execution of an enumeration script to retrieve an undetermined number of code strings: “This is not easy with other providers since they must mention in the URL a client ID, making it difficult to execute enumeration in the records.”
During this research a second API call was also found in a documented API system that was allowing access to another set of records in plain text that were previously unavailable. Using both methods, the researchers were able to find records dating from January 2013 to May 2022.
Aqua Security estimates that valid records are in a range of between 4.2 million and 774 million. After analyzing a sample of 8 million records, experts found nearly 73,000 sensitive strings in the form of tokens, secrets, and various credentials associated with cloud services such as GitHub, AWS, and Docker Hub.
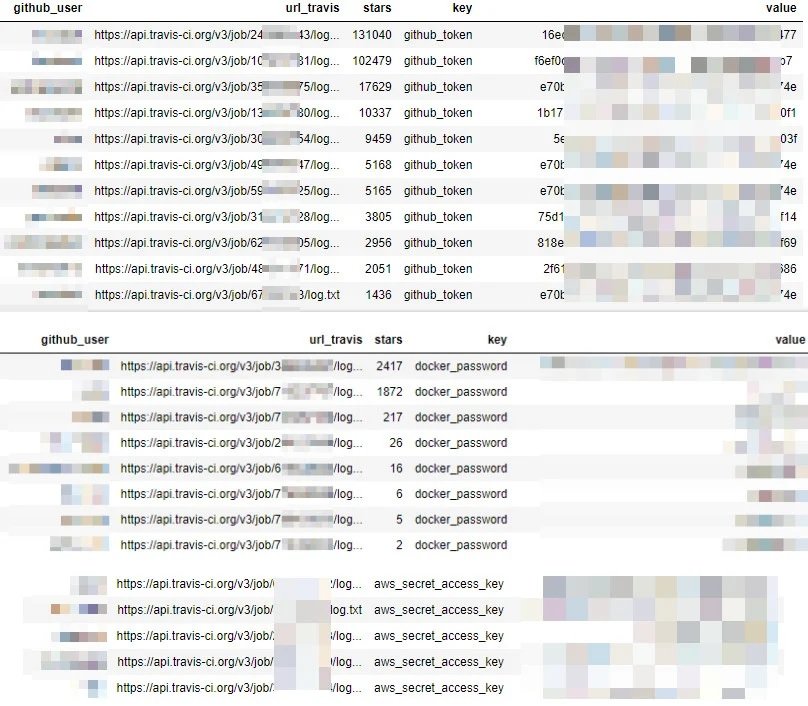
Experts note that some of the data in the historical records was obfuscated. However, this is insufficient because Travis CI allows developers to use various naming conventions for sensitive information.
“We found that, in many cases, ‘github_token’ was masked and revealed no secrets. However, we found around 20 variations of this token that were not protected in any way by Travis CI,” the researchers add.
Travis CI received a report and while the researchers believed the bugs would be addressed soon, a message from the platform responded by mentioning that this is a design issue and probably won’t be fixed. User log exposure appears to be a recurring issue for Travis CI, as reports on this type of risk have been published in 2015, 2019, and 2021.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











