A researcher and ethical hacking specialist got a historic $10 million payment after reporting a critical vulnerability in Wormhole, Ethereum’s central bridge contract. Wormhole is a decentralized protocol that enables interoperability between blockchain structures such as Ethereum, Terra and Binance Smart Chain (BSC).
The report, by a researcher known simply as ‘Satya0x’, details that the exploitation of this flaw could have allowed malicious hackers to demand a ransom with the threat of blocking access to the protocol, which would have left all stored funds unusable.
In his proof of concept (PoC), published on GitHub, the researcher notes that more than $730 million in virtual assets resided in the Wormhole contract at the time of testing. In response, Wormhole approved the maximum payment set in its vulnerability rewards program.
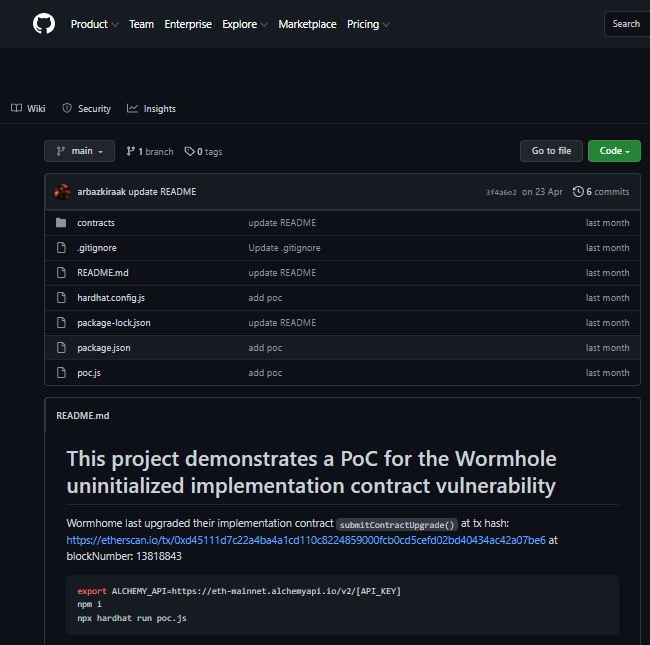
The vulnerability was described as an updateable proxy implementation self-destruct bug, and was validated and fixed in late February only a few hours after the researcher submitted his report.
Apparently, this error exists due to an implementation for a Universal Upgradeable Proxy Standard (UUPS) proxy, which was not initialized after a previous fix reversed the original initialization. The threat actors could have passed their own Guardian set and proceeded with the update as a Guardian under their control.
Subsequently, malicious hackers could force an update attempt with submitContractUpgrade(), causing a DELEGATECALL to a malicious address; at this stage, attackers could execute a SELFDESTRUCT code to permanently delete the deployment contract.
Satya0x was pleased with their work and with the willingness shown by Wormhole and Immunefi, operator of the contract’s bug bounty program: “I am proud to have participated in the mitigation of this vulnerability.”
A reward of $10 million USD seems completely excessive, although this is explained if analyzed in the large and frequent losses suffered by decentralized finance platforms (DeFi). At the beginning of 2022, Wormhole itself lost $325 million USD from a cyberattack of unknown origin, so it should not be surprising that its reward programs are so attractive to the ethical hacking community.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











