The U.S. Department of Justice (DOJ) announced the seizure of $34 million USD in cryptocurrency that was under the control of a dark web vendor. Authorities seized 640.26 Bitcoin, 640.27 Bitcoin Cash, 540.27 Bitcoin Gold, 640.27 Bitcoin S.V. and 919.30 Ethereum.
In their investigation, authorities report that the individual from whom these virtual assets were seized was engaged in the sale of stolen confidential information on an unspecified dark web platform. Identified as “Moniker 1”, the seller made more than 100,000 transactions before being detected, though he couldn’t help but transact with undercover agents.
Transactions made by this seller include:
- In January 2016, an undercover agent purchased ten Netflix account usernames and passwords
- In April 2016, an undercover agent purchased a username and password from a World Wrestling Entertainment account
- In September 2016, an undercover agent purchased nearly 70 Uber account usernames and passwords
- In March 2017, an agent purchased three Xfinity account usernames and passwords
- In March 2017, an agent purchased access credentials to an HBO Go account
The work of the undercover agents made it possible to trace two residences in Florida, USA, allegedly belonging to the seller. Apparently, Moniker 1 used these addresses as a shipping address for some narcotics purchases.
The person associated with the shipping addresses lived at a residence in Parkland, Florida. The researchers identified the resident and, using a call log, monitored Internet traffic to and from the IP address associated with this residence. Authorities later identified the defendant’s bank account and requested an access order for his transaction history. Once with access to this information, the researchers confirmed that these records matched the seller’s activity, recorded in cryptocurrency transactions.
In mid-May 2017, agents completed a search warrant during which a laptop owned by the defendant was seized, eventually leading to the seizure of the cryptocurrency accumulated by the seller.
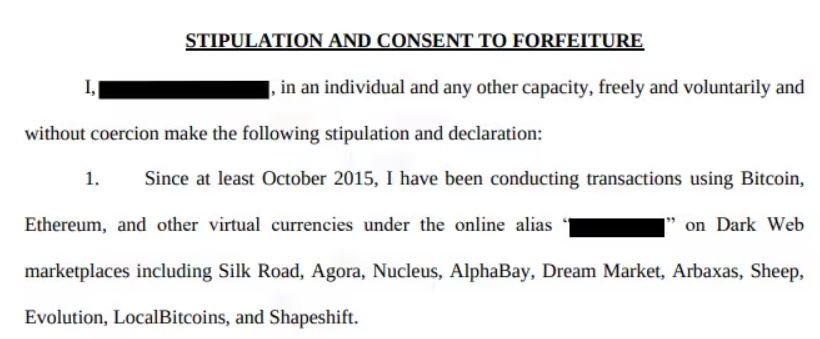
After his arrest, the defendant acknowledged making thousands of transactions on platforms such as Silk Road, Agora, Nucleus, AlphaBay, Dream Market, Abraxas, Sheep and Evolution.
Blockchain analysis confirmed that 96% of transactions at the defendant’s cryptocurrency address were associated with various dark web platforms. Court documents mention that the individual obtained thousands of Ethereum units by converting Bitcoin obtained from illegal transactions into illegal online platforms.
Apparently, Moniker 1 turned Bitcoin into Ethereum using a virtual exchange platform that did not require users to provide personal information to complete the transaction, completing their illegal operations anonymously. According to information from other court documents, this exchange platform could be ShapeShift, as it shares the characteristics described by the agents.
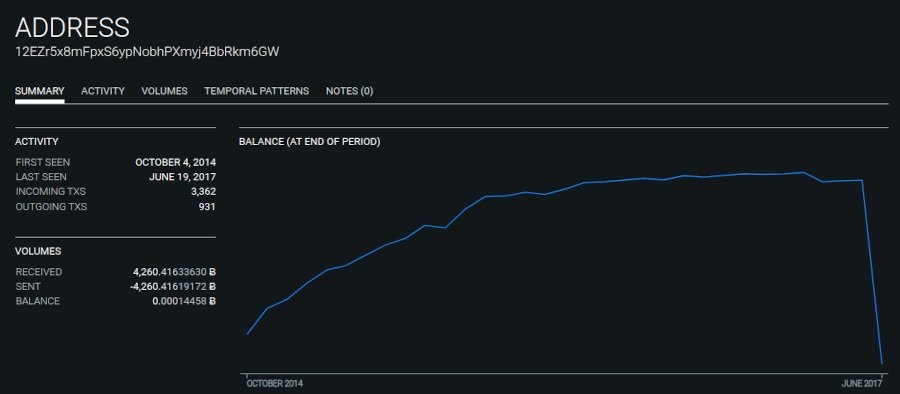
A history review to the Ethereum blockchain showed that approximately 919.30 Ethereum units were deposited into the Ethereum 7800 wallet through nine transactions between March 16 and 17, 2017 or approximately. These deposits were traced back to a known Ethereum address associated with the first exchange platform.
Another review, this time on the Bitcoin blockchain, showed that approximately thirty-two Bitcoin units were sent through nine transactions from the m6GW Bitcoin wallet to other Bitcoin addresses, and from those addresses, transfers were made to hide traces of these operations.
At the end of 2021, the defendant signed a consent to confiscation, which the DOJ released through its official communication platforms. Because no one filed a lawsuit against this decision, so no one will be able to file any more legal remedies to access these assets in favor of the defendant. It is not yet known what sentence the defendant faces, although he is expected to face severe charges including conspiracy to commit fraud, money laundering and other crimes.
According to the DOJ press release, this case was the result of so-called “Operation TORnado,” described as a joint investigation arising from the ONGOING efforts of the OCDETF. The forfeiture lawsuit lists the value of the seized cryptocurrency at $47 million USD, while the figure of $34 million USD appears in the USAO announcement.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











