A web application firewall (WAF) is a program designed to analyze incoming requests to a web server and, according to the rules established by administrators, filter those requests that may be dangerous for an online platform.
According to specialists in web application security, the use of WAF solutions limits the risk of exploitation of known vulnerabilities in websites, since requests from payloads cannot reach the web server or the web application, being rejected by this security tool. That is why these solutions are a fundamental part of an adequate web security environment.
A limited solution
Implementing a WAF is not as simple as it should be, as you need to apply the correct settings. Some WAF applications simply do nothing after installation because they disable all filtering rules. Also, if all WAF rules are simply activated, the web server may stop working, as almost all web requests will be considered potentially dangerous, so web administrators will need to decide wisely which filters to implement.
There are hundreds of WAF solutions and they all vary greatly, although your configuration of some of them boils down to enabling and disabling categories of filtered threats in the web interface. To customize some of them, you need to edit text files that describe dangerous queries in your own WAF language.
To configure WAF rules as strictly as possible, Web application security specialists recommend enabling rules that deny everything except the necessary types of requests to the Web server. To do this, you need, first of all, to have a good understanding of how the protected website works, what you need and what you don’t; and, secondly, to have a good understanding of the types of attacks, how they are exploited, and how a custom WAF works.
On this occasion, web application security specialists from the International Institute of Cyber Security (IICS) will show you some tools designed to detect a WAF solution, find the manufacturer and discover possible ways to evade the filtering of malicious requests.
Wafw00f
Using Wafw00f, researchers will be able to very quickly and accurately determine the type of WAF for a specified website. In addition to this function, Wafw00f has other features:
- Crawl a site through a proxy
- Support for csv, json or plain text input and output formats
Using the program is very simple: just specify the domain of the site for which you want to find out the features of the WAF:
wafw00f URL
For example:
wafw00f wise.com
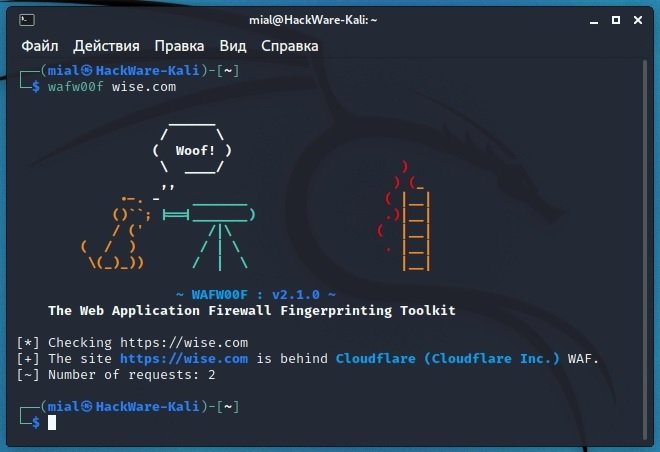
The “Number of requests” line shows the number of requests made; only two were enough. As a result, a Cloudflare WAF solution was identified.
If you think the scan may have been inaccurate, add the -a option, as a result, WAFW00F will not stop after the first match, but will check all possible records:
To send requests through a proxy, use the -p option, after which specify the proxy data: SOCKS and authentication are supported, examples of proxy parameters specified correctly:
- http://hostname:8080
- socks5://hostname:1080
- http://user:pass@hostname:8080
With the following command you can use the Tor network as a proxy:
wsudo systemctl start tor
wafw00f -p socks5://127.0.0.1:9050 admitad.com
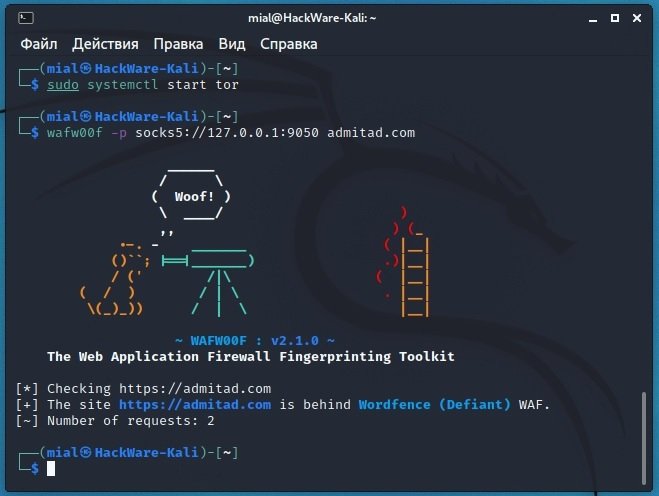
Despite the slowness of the Tor network, the authentication of web protection (which turned out to be Defiant’s Wordfence) was very fast and only required two requests.
Targets for web security identification can be compiled into a file. When you start the program, you can specify a file with a list of supported destinations, csv, json, or text formats. For csv and json, a column or element called “url” is required. Text file format: 1 URL per line. Example:
wafw00f -i urls.txt
With the -t option you can specify which WAF you want to find, this option should be especially useful by adding the -i option:
wafw00f -i urls.txt -t 'Cloudflare (Cloudflare Inc.)'
You can display the full list of supported Web application firewalls with the following command: Web application security specialists recommend paying attention to the format in which the desired WAF is indicated. If you have any questions about how to specify the WAF correctly, go to the project page on GitHub, find the file you need, and open it. In https://github.com/EnableSecurity/wafw00f/tree/master/wafw00f/plugins, look for a line that begins with NAME, for example:
NAME = 'ACE XML Gateway (Cisco)'
The program is very fast and simple; however, due to the fact that it is impossible to change the User-Agent, sometimes the program cannot identify web protection because the server rejects requests for this tool with the default User-Agent.
IdentityYwaf
This is another simple, effective and easy-to-use program. Similar to Wafw00f, this is an identification tool that can recognize the type of web application security based on the server’s response. In addition, this tool performs additional queries to determine what types of vulnerability a web platform is protected against.
After scanning, the tool gives an estimate of the complexity to exploit vulnerabilities in the target, if any. The latest version of this program can detect more than 80 different protection products, developed by firms such as CrawlProtect, WatchGuard, Wordfence and Palo Alto, among others.
According to web application security experts, IdentityYwaf performs validation in two ways:
- Non-blind: when the WAF is identified based on messages that are its own. For example, in the message “403 (‘<title>Attention required! | Cloudflare</title>”, the name of the web application firewall is clearly shown, but at the same time it can be an attempt to confuse the attacker or pentester
- Blind: When the WAF is identified based on the payload locks sent to it
The following screenshot shows an example of a web application firewall scan:
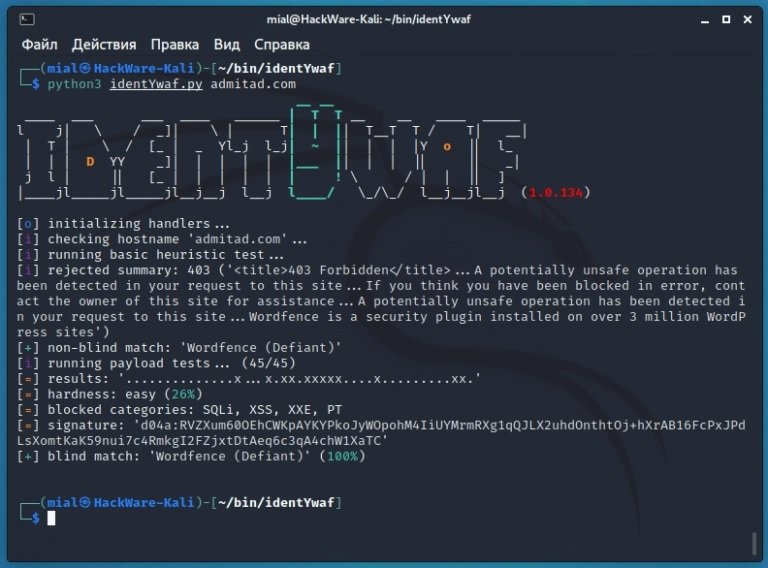
Let’s examine the output of the program.
The type of WAF according to non-blind scanning is Wordfence, from Defiant:
[+] non-blind match: 'Wordfence (Defiant)'
A total of 45 tests were conducted with various payloads (non-threatening requests that are very similar to requests to exploit vulnerabilities):
[i] running payload tests... (45/45)
The result is presented in diagram form, in which the point is not a blocked payload, and the cross is a block of WAF in response to the sent payload:
[=] results: '..............x...x.xx.xxxxx....x.........xx.'
The complexity of exploiting potential attacks is shown in a simple percentage format:
[=] hardness: easy (26%)
Categories of blocked attacks:
[=] blocked categories: SQLi, XSS, XXE, PT
The final decision based on the blind identification method and its probability:
[+] blind match: 'Wordfence (Defiant)' (100%)
One more test
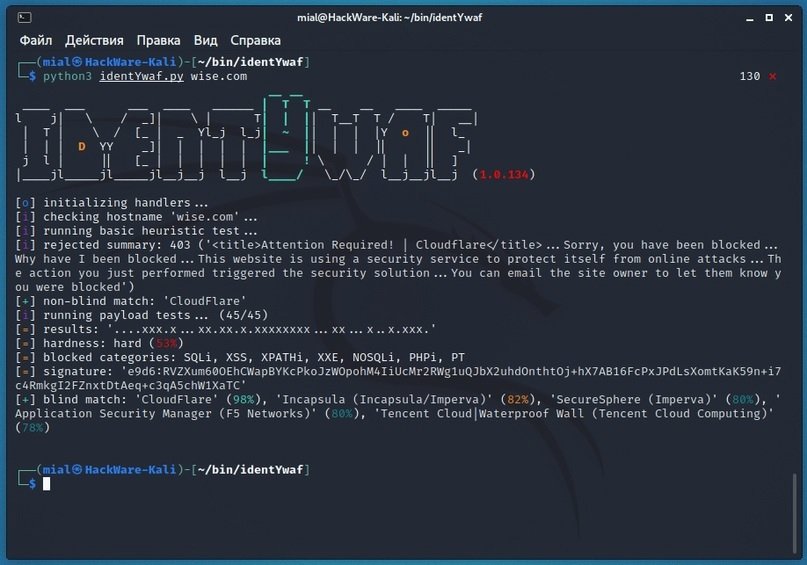
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










