A report specialized in WordPress security points to a 150% increase in reported flaws during 2021 compared to the previous year, in addition to establishing that almost 30% of the vulnerabilities detected in plugins for WordPress do not receive updates.
Since this is the most widely used content management system (CMS) in the world, this should be a worrisome issue for tens of millions of website administrators.
According to Patchstack specialists, of all the flaws reported in 2021, only 0.58% resided in the WordPress core, while the rest affect themes and plugins created by dozens of developers. In addition, about 92% of these flaws are in free plugins, while paid plugins were affected by 8.6% of the failures reported last year.
Of all the vulnerabilities reported in that time period, five critical bugs were detected in 55 WordPress themes, most of them related to the abuse of the file upload feature.
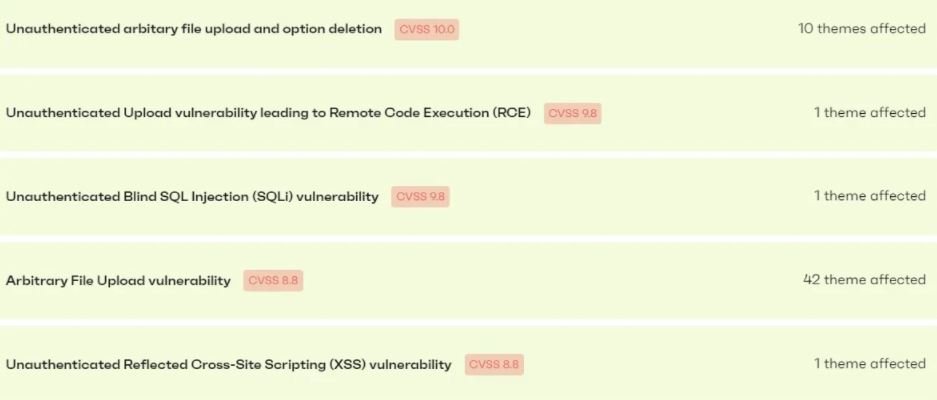
Regarding plugins, 35 critical vulnerabilities were reported, two of which could be present in up to 4 million websites.
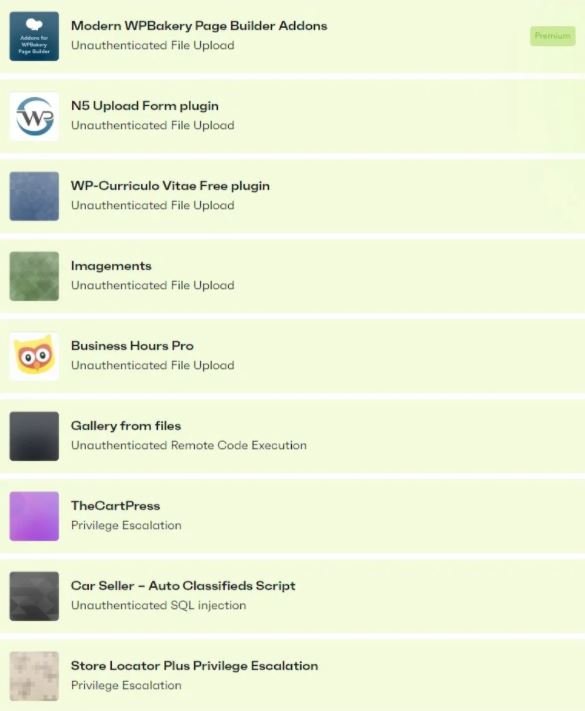
Some of the security issues in WordPress that caught the most attention of researchers reside in Optimonster, a plugin used in about 1 million websites, and in All in One, an SEO plugin with more than 3 million active installations.
Although these critical vulnerabilities were fixed, nine other plugins with millions of installations never received updates for the severe security flaws detected over the past year. In addition to uploading potentially malicious files, these plugins are affected by privilege escalation flaws and SQL injections.
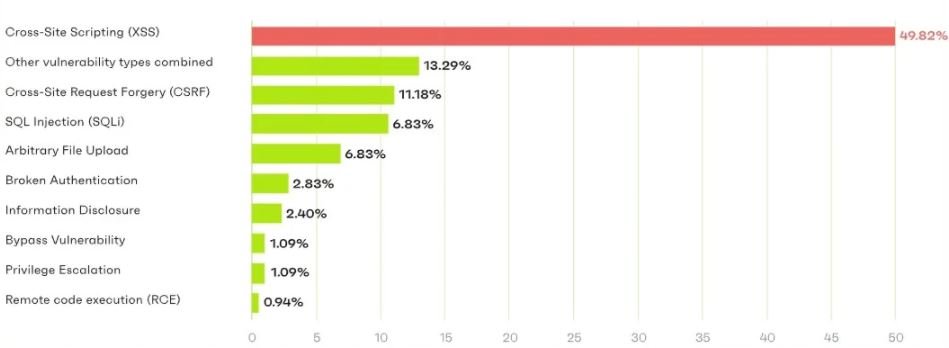
On the most common security issues in WordPress plugins, the researchers note that cross-site scripting (XSS) errors are the most reported, followed by request spoofing flaws, SQL injections, and arbitrary file loading into the system.
Faced with this situation, experts recommend that website administrators acquire paid versions of plugins, use as few tools as possible on their platform and keep their plugins always updated to the latest version available, which will considerably mitigate their exposure to this kind of security risks.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











