Cybersecurity specialists report the detection of a severe vulnerability in the Linux kernel whose exploitation would allow threat actors to escape from a container to execute arbitrary commands. The flaw was tracked as CVE-2022-0492 and received a score of 7/10 according to the Common Vulnerability Scoring System (CVSS).
The flaw was described as a privilege escalation error that affects the function of the Linux kernel called control groups, responsible for limiting, accounting for, and isolating the use of resources such as CPU, memory, disk inputs, and outputs from a collection of processes.
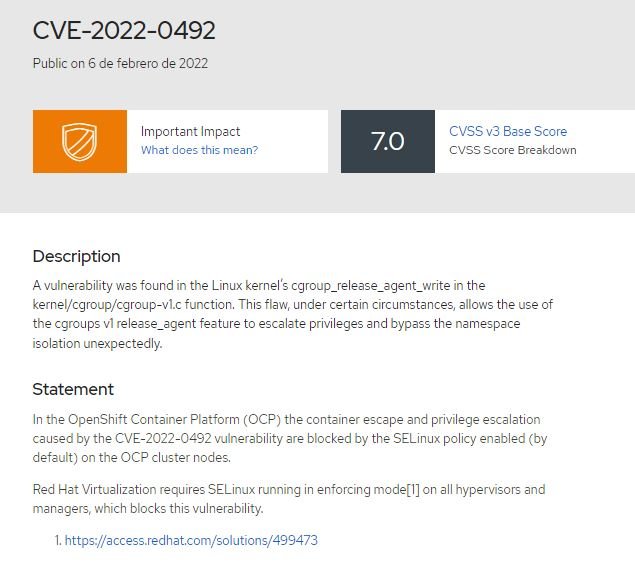
In the report, the researchers mention that a flaw was found in cgroup_release_agent_write of the Linux kernel in the kernel/cgroup/cgroup-v1 function.c. Under certain circumstances, the vulnerability would allow the use of the release_agent function of cgroups v1 to escalate privileges and avoid isolation of the namespace unexpectedly.
Major Linux distributions, including Suse, Ubuntu, and Redhat, also posted their own notices related to this flaw. Reports indicate that the flaw lies in the functionality release_agent of cgroups v1 that runs after the completion of any process in the group.
The main cause of the problem is the implementation of cgroups in the Linux kernel, which does not properly restrict access to the compromised function. Local threat actors could exploit this vulnerability to gain administrative privileges.
Moreover, Palo Alto Networks notes that CVE-2022-0492 exists due to the lack of administrative privilege checking in the release_agent configuration process. A threat actor can write to the release_agent file to force the kernel to invoke an elevated binary and take control of the affected system.
“Because Linux sets the owner of the release_agent file as the root, only the root can write to it (or processes that can bypass file permission checks through the ability CAP_DAC_OVERRIDE). As such, the vulnerability only allows root processes to increase privileges,” adds Palo Alto Networks.
Users are encouraged to install security fixes as soon as possible. Containers running appArmor or SELinux security systems are not affected, as confirmed.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











