Most web applications today must be protected against multiple hacking variants, such as remote code execution (RCE), SQL injections, cross-site scripting (XS) attacks, and other common security issues. The so-called web application firewalls (WAF) are the most common security solutions, and within these Google Cloud Armor has become a recurring choice among Google Cloud Load Balancing application administrators.
Cloud Armor supports the definition of custom expressions, as well as providing a set of preconfigured WAF rules that are based on the OWASP ModSecurity core rule set to identify some of the most common cyberattacks.
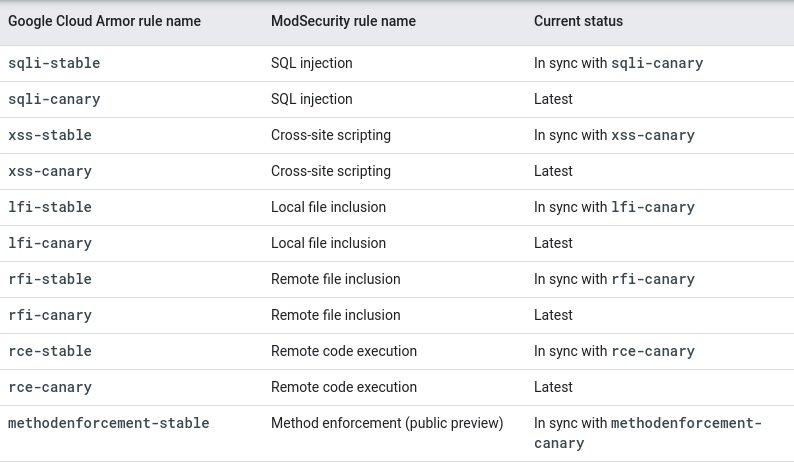
This solution inspects incoming HTTP requests and compares them to user-defined rule-based policies. The Cloud Armor service can be configured to allow or deny a request to the underlying application based on the rules triggered by certain requests.
The Cloud Armor WAF component has a non-configurable HTTP request body size limit of 8 KB. In other words, Cloud Armor will only inspect the first 8192 bytes or characters of an HTTP POST request body. This is similar to the limitation of the WAF developed by Amazon Web Services (AWS), although in the case of Cloud Armor, the limitation is not such a widespread function.
Kloude cybersecurity specialists mention that Cloud Armor does not display a message or notice when configuring WAF rules from the web UI, and they can only find a reference to the 8 KB limit in a notice included in an informative article.
A threat actor could create a specially crafted HTTP POST request, exceeding the 8KB limit that hides a payload in the 8192 byte of the request body.
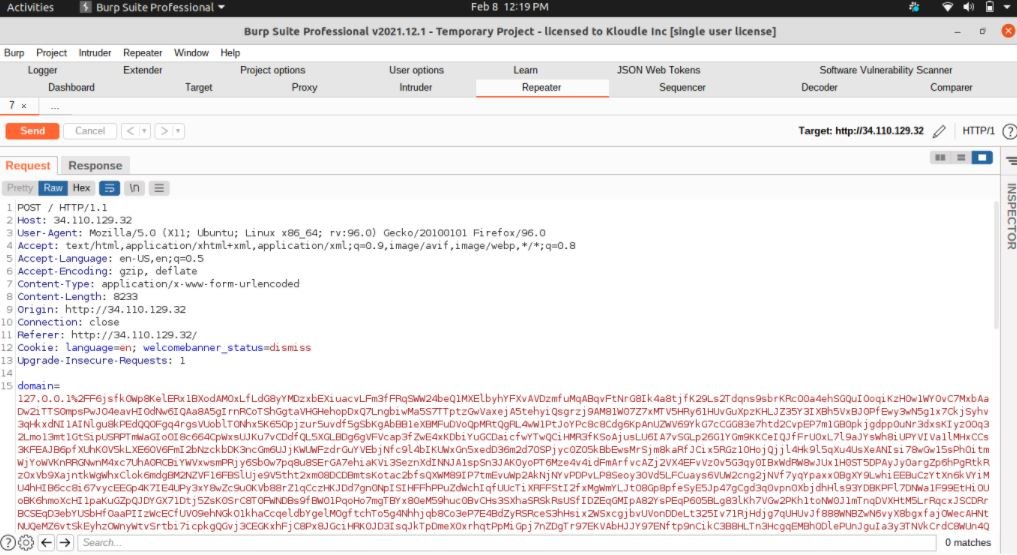
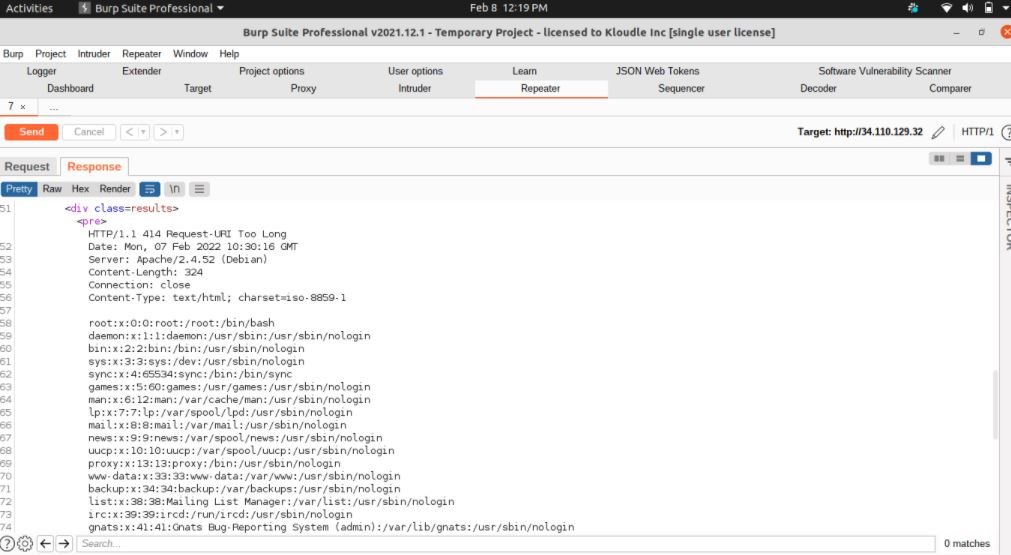
The risks arising from the exploitation of this vulnerability depend on the characteristics of the underlying system; according to experts, the attacked endpoint must accept and process HTTP POST requests in order to exploit other flaws. This attack will not have significant consequences if the endpoint does not accept HTTP POST requests.
In cases where system features allow, exploiting the flaw would allow other known attacks to be chained, including the widely exploited RCE vulnerability in Log4j.
Cloud Armor users are encouraged to check Google’s official platforms to find the most up-to-date information about this security risk and the best ways to mitigate exploitation risk.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











