Cybersecurity specialists developed an Apple AirTag clone to demonstrate that the tracking protection features of the Find My network can be easily bypassed. This device has been the subject of numerous reports related to tracking and personal security, as it can sometimes be used for malicious purposes, such as espionage.
Infosec researcher Fabian Braunlein of Positive Security has been sharing his ideas on fairly obvious evasion methods for months, considering that everything can be put into practice in real scenarios.
The expert relied on the system on OpenHaystack, a framework for tracking Bluetooth devices using the Find My network, for the development of the clone. Using an ESP32 microcontroller with Bluetooth support, a power bank, and a cable, a clone of the AirTag device was created.
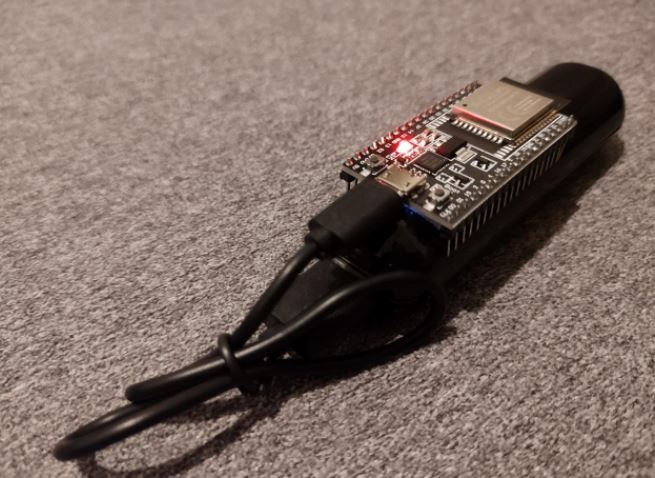
This computer uses a custom ESP32 firmware that constantly rotated the public keys, sending one periodically and repeating the list approximately every 17 hours. However, it is believed that a common seed and bypass algorithm used in the clone and a Mac application used to track it could create a key stream that is virtually never repeated.
Employing an irreversible bypass function and overwriting the seed with the result of the next round would make it impossible for law enforcement or Apple to obtain the previously transmitted AirTag public keys, regardless of whether they have physical access to the device. During their experiment, the Android Tracker Detect app did not show the cloned AirTag at all, although using other tools it was possible to track the cloned device.
The specialist considers that the main risk does not exist properly due to the existence of the AirTag, but exists due to the introduction of the Find My ecosystem that uses the client’s devices to provide this Apple service. Since the current iteration of the Find My network can’t be limited to just AirTags and hardware that officially has permission to use the network, the expert believes Apple should rethink the security of these features.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











