A bug in the Hive ransomware encryption algorithm would allow victims to recover their information without having to negotiate with hackers. This is a ransomware-as-a-service (RaaS) operation that resorts to the double extortion method, encrypting information and demanding a ransom in exchange for not leaking this sensitive data.
This operation experienced an excessive growth in the first half of 2021, so the Federal Bureau of Investigation (FBI) published an alert detailing the characteristics of the Hive ransomware, its technical details and some recognizable indicators of compromise. A report by the security firm Chainalysis points out that this was one of the 10 most successful ransomware operations of 2021, using all kinds of resources at its disposal.
According to researchers at Kookmin University in South Korea, Hive uses a hybrid encryption scheme, employing its own symmetric encryption to block access to infected files, which made it possible to recover the master key and generate a decryption key independently. The researchers claimed that the infected files were successfully recovered using this method.
This is considered the first successful attempt to remove the encryption of the Hive ransomware registered so far, demonstrating a success rate of over 95%, a process described in the following diagram:
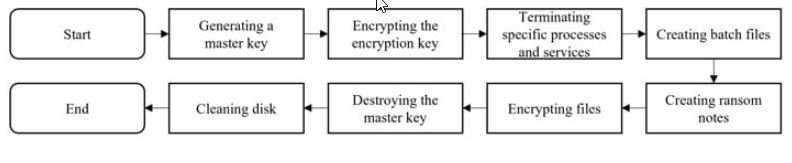
In more detail, the researchers mentioned that this ransomware variant generates 10MiB of random data to use as a master key, extracting from a segment of the master key 1MiB and 1KiB of data for each file to be encrypted and uses these pieces of information as a key stream.
These fragments of the master key are stored in the name assigned to each affected file, so it is possible to determine the rest of the master key and decrypt the compromised files.
Of all the keys recovered, approximately 72% of the files were decrypted, while the restored master key managed to decrypt approximately 82% of the infected files, which could prove incredibly beneficial for users who are still dealing with the attacks of this malware variant. It is true that the developers of Hive could correct this problem in the following versions of the ransomware, but in the meantime the researchers have made an important finding to impact their operations.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











