Moxa users will need to upgrade MXview to versions greater than 3.2.4 in order to address five vulnerabilities in the web-based network management system. These failures received critical scores of 10/10 according to the Common Vulnerability Scoring System (CVSS).
According to Claroty researchers, unauthenticated threat actors could chain two or more of these vulnerabilities to lead to remote code execution (RCE) on any non-updated MXview server.
In this regard, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) published a notice about these flaws, mentioning that their malicious exploitation would allow threat actors to execute code, gain access to the vulnerable program, extract access credentials, disable the software and perform other malicious tasks.
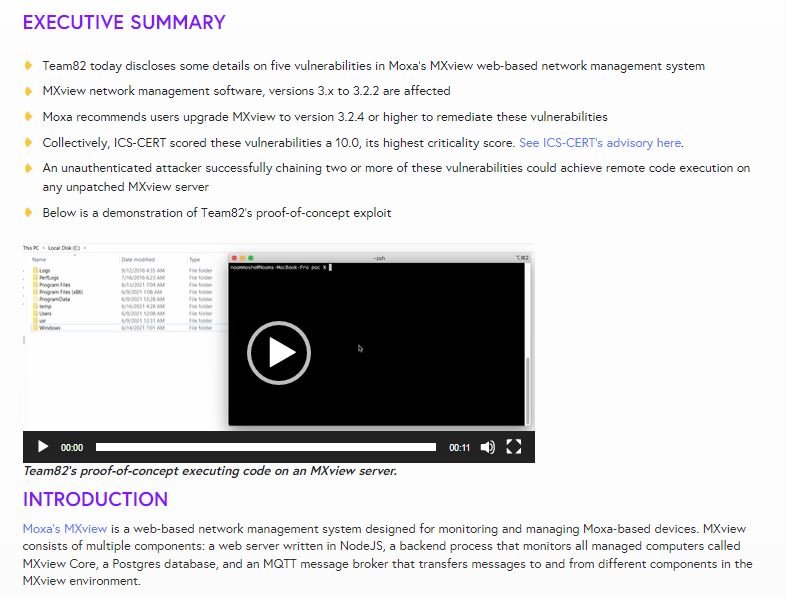
The vulnerable system was designed to monitor and manage Moxa-based devices. The researchers identified the five flaws as CVE-2021-38452, CVE-2021-38456, CVE-2021-38460, CVE-2021-38458, and CVE-2021-38454 and published a proof of concept (PoC) as a demonstration of the attack.
MXview plays an important role in the Internet of Things (IoT) industry, so the importance of these vulnerabilities is high. Specialists mention that, due to the type of manufacturing organizations that use them, not all of their end users will have the resources to mitigate the scope of failures, which makes high-severity vulnerabilities much more dangerous.
It is highly likely that these vulnerabilities will have a major impact. Recall that the 5 vulnerabilities have a CVSS score of 10/10 and, because they focus on converged networks, increases the possibility that malicious hackers can exploit them to compromise corporate networks.
Finally, these flaws would allow privilege management to be exploited, which is considered especially critical due to the damage that could be caused by a cyberattack executed with root user privileges, including malware delivery and control of critical infrastructure.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











