Samba announced the release of some updates that aim to address various vulnerabilities whose successful exploitation would allow threat actors to lead to an arbitrary code execution scenario with high privileges on affected systems.
As you may know, Samba is a popular implementation of the Server Message Block (SMB) protocol that allows users to access files, printers, and other commonly shared resources over a network.
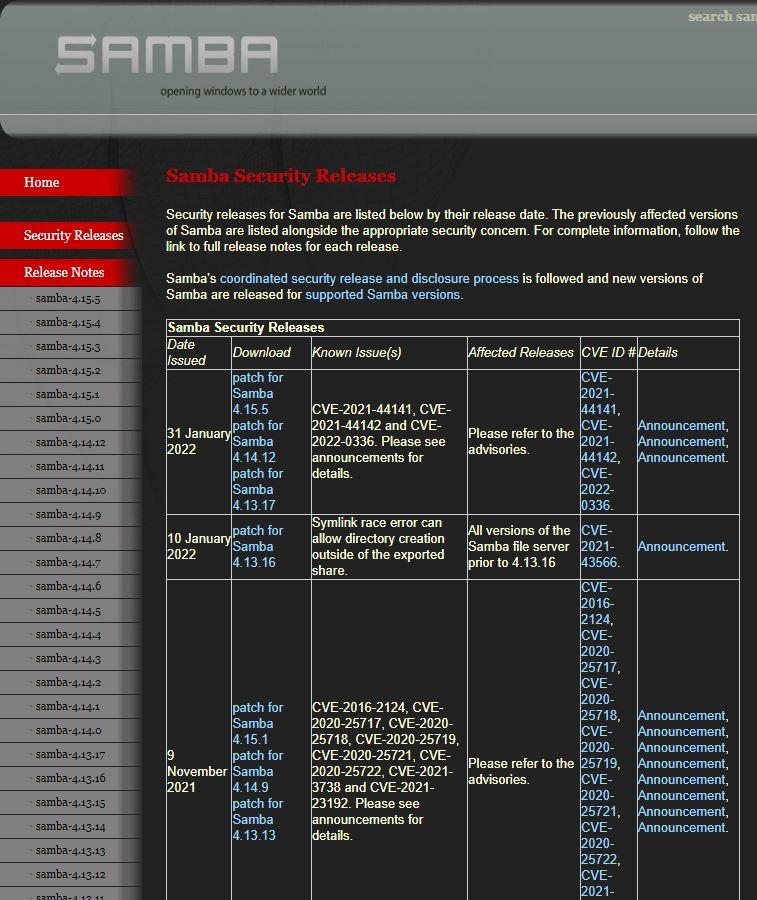
The most severe of these flaws was tracked as CVE-2021-44142 and resides in all Samba versions prior to v4.13.17; Described as an out-of-bounds heap read/write error, the flaw affects the VFS module “vfs_fruit”, which provides compatibility with Apple SMB clients. This vulnerability also affects some widely used Linux distributions, such as Red Hat, SUSE Linux, and Ubuntu.
As if that were not enough, the flaw received a score of 9.9/10 according to the Common Vulnerability Scoring System (CVSS), so it is considered a critical security problem.
The report also highlights CVE-2021-44141, a problem of information leakage through symbolic links; and CVE-2022-0336, a flaw that allows Samba users to write to an account to impersonate an arbitrary service. These flaws got CVSS scores below 4.0/10.
Mitigations are now ready, so Samba administrators are advised to upgrade to secure versions or apply security patches as soon as possible, as the risk is considered active.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











