The government of Houston, Texas, warns its citizens about a new variant of fraud in which threat actors place fraudulent QR codes on the parking meters of some streets in order to take users to fraudulent websites where their confidential information could be stolen.
As you may recall, a QR (Quick Response) code is a two-dimensional barcode that, when scanned with a mobile device, can almost instantly link the user to a website, information platform, and other sets of information without having to enter through the browser. In the midst of the COVID-19 health crisis, these codes have once again been used massively in shopping malls, restaurants, and public transport and government offices to limit contact between people to the minimum possible.
Over the past week alone, authorities found five payment stations with these fraudulent QR codes, most in the city center. These codes are carefully placed on the machines, although they must be in sight so that potential victims can scan them.

By scanning one of these codes, users will be redirected to a website like the one shown below:
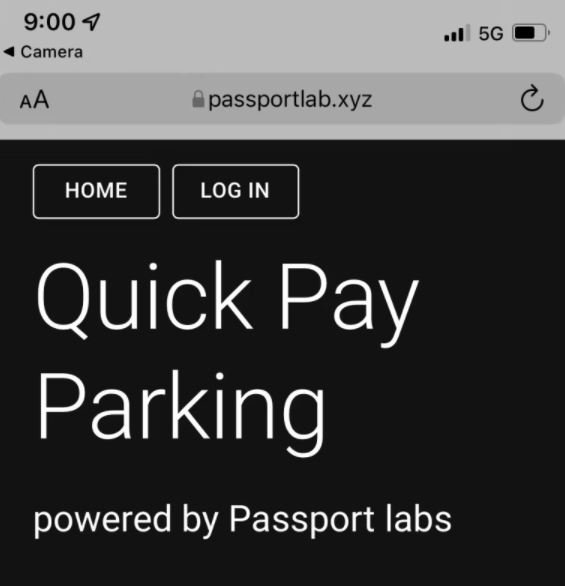
The authorities recommend that citizens refrain from scanning any QR code they find on the street, since the city does not accept any payment through these codes. Houston will continue to monitor payment stations in the search for more malicious QR codes.
It should be remembered that, at the moment, Houston only accepts four means of payment for parking meters in the city: coins, banknotes, credit card and the ParkHouston mobile app. The local government also asked citizens to report any suspicious activity near these payment stations, either through the 911 emergency numbers or through ParkHouston’s official platforms.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











