During a routine security scan, Rapid7 specialists detected five vulnerabilities in SonicWall Secure Mobile Access (SMA) Series 100 devices, including SMA 200, 210, 400, 410 and 500v iterations. According to the report, the exploitation of the most severe of these flaws could lead to a remote code execution condition on the affected devices.
The flaws were notified to the manufacturer, which has already issued a patch to address bugs on affected devices. Below are brief descriptions of the reported flaws:
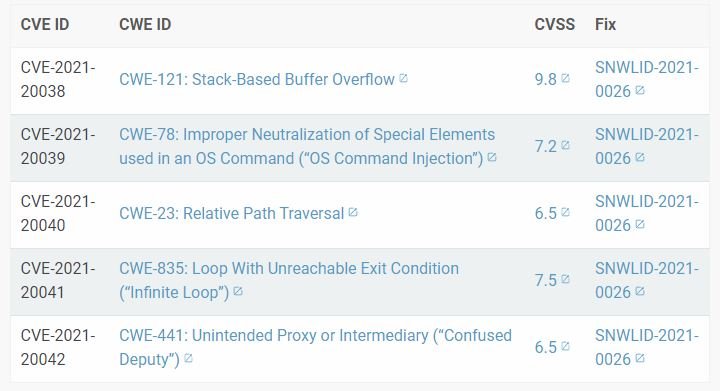
CVE-2021-20038: The web server on tcp/443 (/usr/src/EasyAccess/bin/httpd) is a slightly modified version of the Apache httpd server. One of the notable modifications is in the mod_cgi module (/lib/mod_cgi.so), plus there is a custom version of the cgi_build_command function that aggregates all environment variables into a single stack-based buffer using strcat. If a threat actor generates too long a QUERY_STRING, it can overflow the stack-based buffer.
CVE-2021-20039: The web interface uses a function to scan strings for shell metacharacters and prevent command injection attacks. This function looks for normal characters (&|$><;’, etc.), but does not look for the new-line character (‘n’), which is considered a problem since when used in a string passed to the system, it will act as a terminator. Hackers could abuse this behavior to evade security controls and attack the target system.
CVE-2021-20040: The SMA 100 series allows users to interact with remote SMB shares over the HTTPS server. This functionality resides on the endpoint https://address/fileshare/sonicfiles/sonicfiles. Most of the functionality flows through the SMA series device and actually leaves nothing on the device itself, with the exception of RacNumber=43, which is supposed to write a file to the /tmp directory, but is vulnerable to a cross-path attack.
CVE-2021-20041: Remote hackers can consume all resources on the device’s CPU due to designed HTTP requests sent to hxxps://address/fileshare/sonicfiles/sonicfiles, resulting in an infinite loop in the file explorer process.
CVE-2021-20042: Unauthenticated malicious hackers can use Series SMA 100 devices as an unwanted proxy or intermediary. In other words, threat actors can use these computers to access accessible systems through the device’s internal network interface.
Updates are now available, so users are encouraged to upgrade as soon as possible. To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











