Mozilla security teams announced the detection of a critical memory corruption flaw residing in its Network Security Services (NSS) cryptography libraries. This is a tool for server and client application development with security enabled for SSL v3, TLS, PKCS #5, PKCS #7, PKCS #11, PKCS #2, S/MIME, X.509 v3 certificates and other security standards.
This flaw was reported by Google Project Zero researcher Tavis Ormandy and resides in NSS versions prior to 3.73 and 3.68.1, as well as being tracked as CVE-2021-43527. Successful exploitation of the flaw could result in a heap-based buffer overflow while handling DER-encoded DSA or RSA-PSS signatures on email clients and PDF readers employing vulnerable versions of NSS.
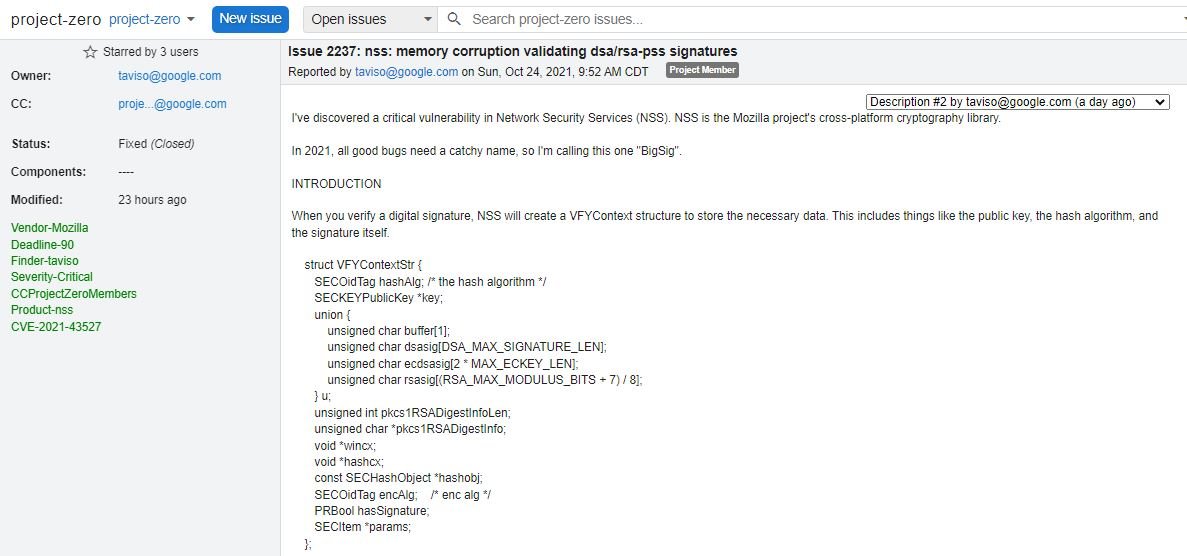
If threat actors manage to trigger buffer overflow, they could lead to scenarios of arbitrary code execution, evasion of security tools, and other risks to the target system.
In its security alert, Mozilla notes that applications that use NSS for certificate validation and other TLS, X.509, OCSP or CRL functions could be affected: “We believe that all versions of NSS since v3.14 are vulnerable. Mozilla plans to produce a complete list of affected APIs, but at the moment any standard use of NSS could be affected, as the flaw is easy to reproduce and affects multiple algorithms.”
The good news is that the vulnerability does not appear to affect the Mozilla Firefox browser, although it is believed that all email clients and PDF viewers that use NSS for signature verification could be affected. Both Mozilla and other companies use NSS in all sorts of products, including:
- Firefox OS
- Open source client applications such as Evolution, Pidgin, Apache OpenOffice and LibreOffice
- Red Hat server products such as Red Hat Directory Server, Red Hat Certificate System, and SSL module mod_nss for Apache Web Server
- Oracle server products such as Oracle Communications Messaging Server and Oracle Directory Server
- SUSE Linux Enterprise Server
Users of affected deployments are advised to stay on top of any updates released by Mozilla and immediately apply patches released by the company.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











