During the Christmas season, the risks of cyberattack increase for multiple targets, including the gamer community. Cybersecurity experts report that this is because several developers decide to launch their strong cards during the last months of the year. Video game enthusiasts are waiting for the release of anticipated titles, such as Forza Horizon 5, Skyrim, and Battlefield 2042, which threat actors will try to exploit for their own benefit.
According to a report by Malwarebytes, during the last 24 hours videos began to appear on YouTube as a result of some video game-related searches, including Skyrim, PUBG, Cyberpunk, COD, GTAV and many others.
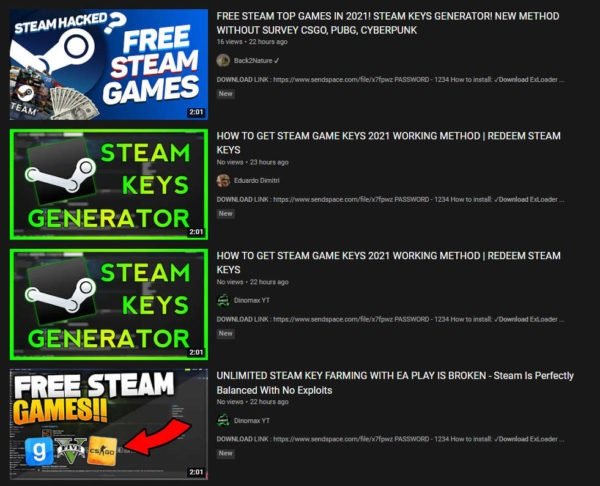
The results of these searches have something in common: they all lead the user to videos that advertise supposed free Stream keys. Although these videos are posted by various channels on YouTube, clicking on the links included in the description redirects the user to the same download website.
Once on this website, users will find a file identified as SteamKeyGeneration.rar, less than 5MB. In addition, the YouTube channels that contain these links also include instructions for downloading this file and running it on the user’s system.
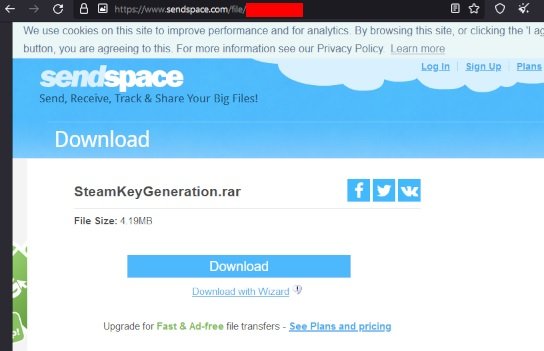
The downloaded file is password protected, which is in the description of the respective video. Once the file is executed on the affected system, the infection will be completed.
The malware was identified as Trojan.Malpack, a generic concept for suspiciously packaged files. While the payload can be any malware variant, this is undoubtedly a malicious tactic. A similar campaign was identified in 2018, when various Fortnite users were tricked by a hacking group into installing Trojan.Malpack on their own systems. On that occasion, hackers managed to steal the information of thousands of people.
YouTube frequently faces similar campaigns with varied themes, such as free VPN solutions, cryptocurrency investing, how-to guides, and other topics. Videos with bitly links send victims to download sites like Mega. Non-abbreviated links redirect to taplink to push Racoon Stealer. Target machines are scanned for card details, passwords, cryptocurrency wallets and other forms of data, which are sent to threat actors.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











