Through a statement, Taiwanese firm Acer confirmed that its aftermarket systems in India were compromised by what they described as an “isolated incident.” Acer reported it activated its security protocols immediately after detecting the attack, in addition to being in the process of notifying affected users and submitting a report to the competent authorities.
Acer is a Taiwanese multinational specializing in hardware and electronics, consolidated as the sixth largest supplier of computer equipment in the world according to recent figures. The company has approximately 7,000 employees in 40 countries, generating revenues of more than $8 billion USD a year.
The company did not add details about those responsible for this incident, although a hacking group has already claimed responsibility for the attack through its platform on the dark web. These hackers claim to have extracted a total of 60 GB of confidential Acer files, including customer data, employees and confidential internal operation details.
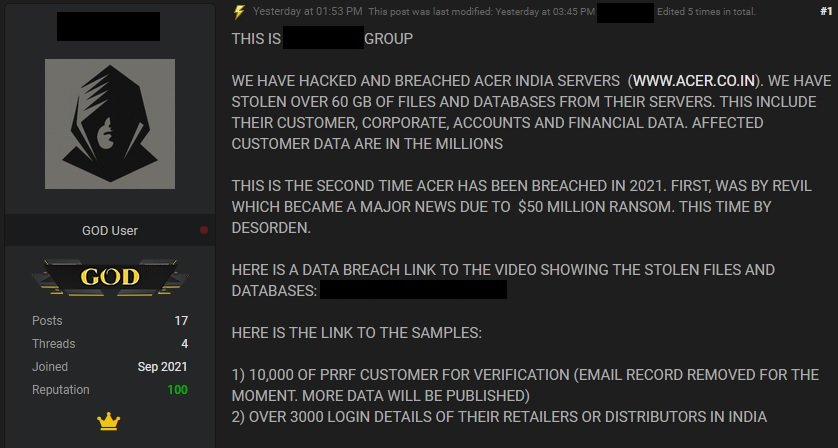
In addition to the post, threat actors shared a video exploring the compromised files, plus some screenshots showing that the leak involves the confidential records of more than 10,000 customers in India.
At the moment Acer has not shared more information about the attack, as the investigation is still ongoing.
It should be noted that this is the second time this year that Acer has suffered an attack capable of interrupting its operations. A few months ago, cybersecurity experts confirmed that the company’s systems were affected by a ransomware infection operated by hacking group REvil, which demanded payment of a $50 million USD ransom.
At the time Acer refused to confirm the incident, simply mentioning that its security teams had detected anomalous activity on its systems. However, the technology firm had to notify the authorities and potentially affected users of the situation, in addition to issuing a statement indicating that an investigation had been initiated, so it was not possible to share more details.
Soon after, cybersecurity experts confirmed that the Revil ransomware group managed to infect the company’s systems by compromising a Microsoft Exchange server.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











