In its latest security update, SAP announced the patching of a total of 13 security flaws, all considered critical and of high severity. The most serious of these failures were tracked as CVE-2020-10683 and CVE-2021-23926, two XML injection errors that received scores of 9.8/10 according to the Common Vulnerability Scoring System (CVSS).
As some users may recall, the XML injection vulnerability allows threat actors to intervene in the processing of XML data, triggering an information leak scenario and allowing interaction with backend systems for malicious purposes. No additional technical detail has been shared by SAP yet.
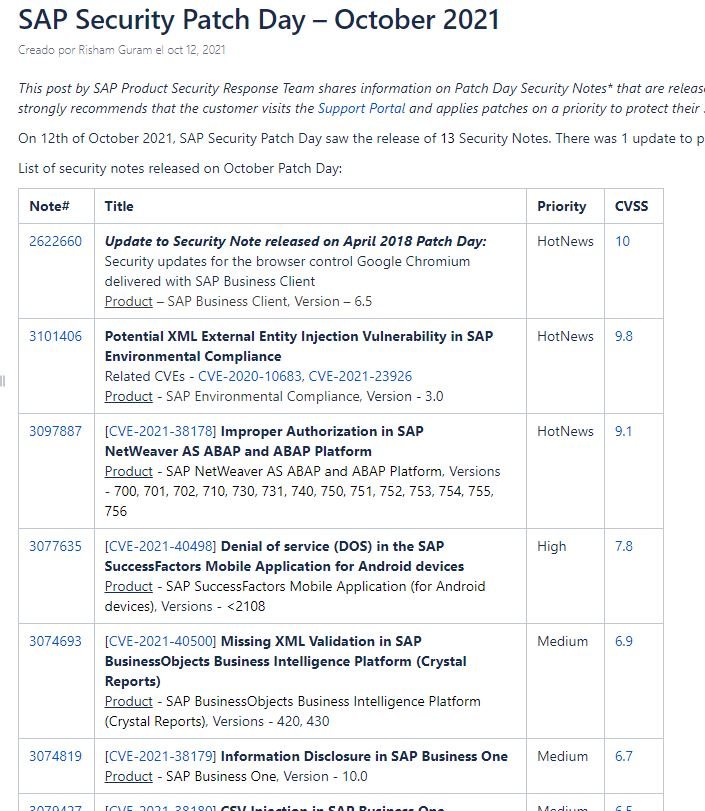
The report also mentions the correction of CVE-2021-38178, an improper authorization flaw in NetWeaver AS ABAP and ABAP Platform that received a CVSS score of 9.1/10. Apparently, this vulnerability could be exploited to evade security mechanisms and extract information from affected applications. As seen above, this Security Patch Day includes an unusual amount of critical-ranked errors in SAP solutions, so users are advised to apply the updates as soon as possible.
Besides critical flaws, SAP issued security patches for a few high-severity vulnerabilities, including a denial of service (DoS) flaw in SuccessFactors Mobile Application for Android devices tracked as CVE-2021-40498.
According to the report, the execution of this flaw on Android would allow the interaction of the system with other malicious applications, leading to failures in various services and opening the possibility of deploying phishing attacks.
Finally, 10 additional bug reports included minor bug descriptions such as sensitive information disclosure scenarios, DoS conditions and cross-site scripting (XSS) attacks.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











