Cybersecurity specialists report the detection of a new attack method on non-fungible token (NFT) sale platforms and cryptocurrency wallets such as OpenSea and MetaMask through a malicious file. These are two of the largest platforms of their kind, so the scope of a potential attack is considerable.
The attack would allow threat actors to take control of user accounts on these platforms and mine all virtual assets stored in their cryptocurrency wallets. Apparently, completing the attack simply requires creating a malicious NFT and sending it to the target user.
Check Point researchers mention that the attack would have already been exploited in real scenarios, with several users reporting that their accounts were emptied after receiving a gift NFT in OpenSea; this practice, known as “airdropping” is common among users of this platform, since it is used to promote new releases.
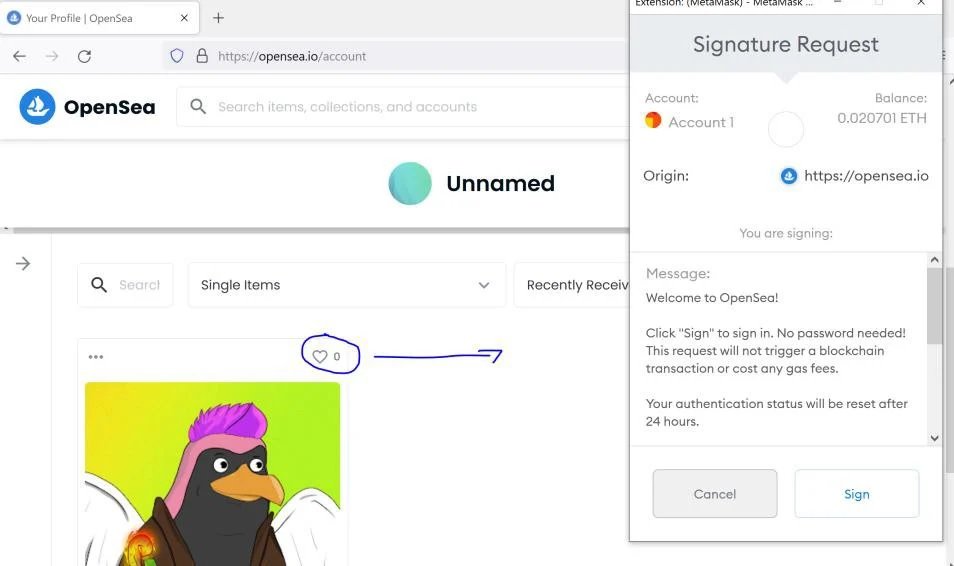
In their description of the attack, experts note that activating an account on OpenSea requires linking a cryptocurrency wallet accepted by the platform, such as MetaMask. Communication with the wallet occurs for any action on the account, so requests for Logins on MetaMask are constantly triggered.
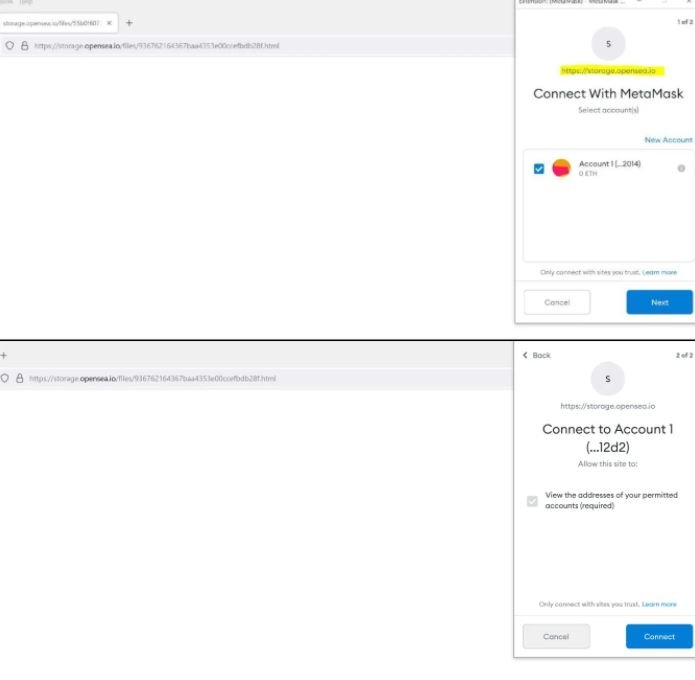
OpenSea allows any user to sell digital art in the form of files in JPG, PNG, GIF, SVG, MP4, WEBM, MP3, WAV, OGG, GLB and GLT format up to 40MB. In its tests, Check Point uploaded to OpenSea an SVG image loaded with malicious JavaScript; clicking this file to open it in a new tab starts running the file under the storage.opensea.io subdomain.
In their report, the experts mention: “During testing we asked an OpenSea user to log into their cryptocurrency wallet after clicking on an image received from a third party, something that the platform should not be in a position to do as it does not relate to the services provided by OpenSea.” Using the Ethereum RPC-API function, communication with MetaMask is initiated, opening a pop-up window to connect to the target user’s wallet. Threat actors must have the victim interact with this pop-up to take control of the cryptocurrency wallet.
Due to the way this window is displayed to users, it can be mistaken for a MetaMask and OpenSea notification, making it easier for users to fall into the trap.
This issue has already been notified to OpenSea and MetaMask, so both platforms are expected to take appropriate measures to mitigate the risk of exploitation.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











