Cybersecurity specialists report the detection of a massive phishing campaign in which threat actors pose as WhatsApp employees in order to trick the user into downloading and installing a banking Trojan on their devices.
Apparently, the campaign operators pretend to send the user a backup of their conversations and call history, so it is highly likely that potential victims will fall into the trap.
In one of the detected messages, a subject line can be seen mentioning “WHATSAPP BACKUP *913071605”, although it is most likely that all the messages that are part of this campaign use this tactic with all potential victims knowing that such a message will attract the attention of any user.
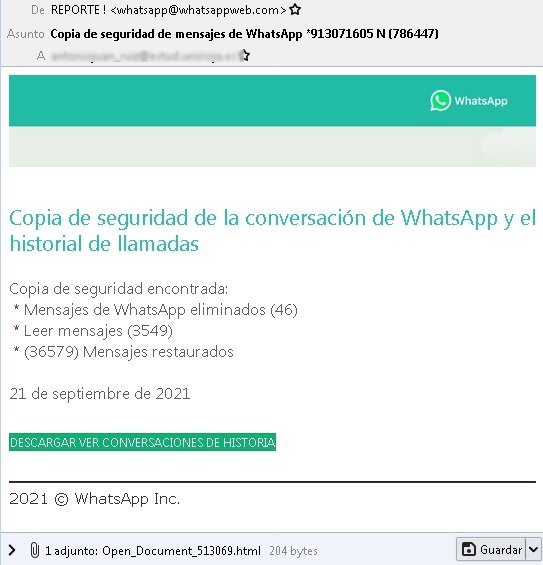
Specialists indicate that it could be difficult for users to distinguish that the message was written by a hacking group, since it is well written and does not contain serious spelling faults, in addition to using a well-designed fake WhatsApp template.
On the other hand, the domain from which the message was sent is easily identifiable as an illegitimate address, although threat actors compensate for this disadvantage with the fact of a rapid infection process that starts as soon as the user clicks on the malicious link received.
When redirected to the malicious website, the user will initiate the automatic download of a ZIP file where the Trojan is hidden, which will be released at the end of the installation.
As in any other phishing scam, users are advised to ignore these kinds of messages and always remember that technology companies, government agencies and online stores never approach the user in this way or send unsolicited files, so prevention is the best way to avoid an attack.
On the other hand, users who have interacted with this email are recommended to perform an intensive scan of their systems in search of any indicator of compromise, in addition to keeping their antivirus solutions installed to the latest versions in order to stay protected against the eventual execution of the malicious file.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











