Citrix security teams announced the release of multiple security patches that will address critical flaws detected in Hypervisor. The most severe of these vulnerabilities, tracked as CVE-2021-28697, would allow host compromise due to Grant v2 status pages being unassigned under certain conditions, causing vulnerable software to map them to other locations.
In such a case, a guest virtual machine could maintain access to pages that could have been released and then reused for another purpose, so the malicious code executed on this virtual machine could have 2 or more virtual CPUs assigned. This flaw received a score of 7.8 on the Common Vulnerability Scoring System (CVSS) scale.
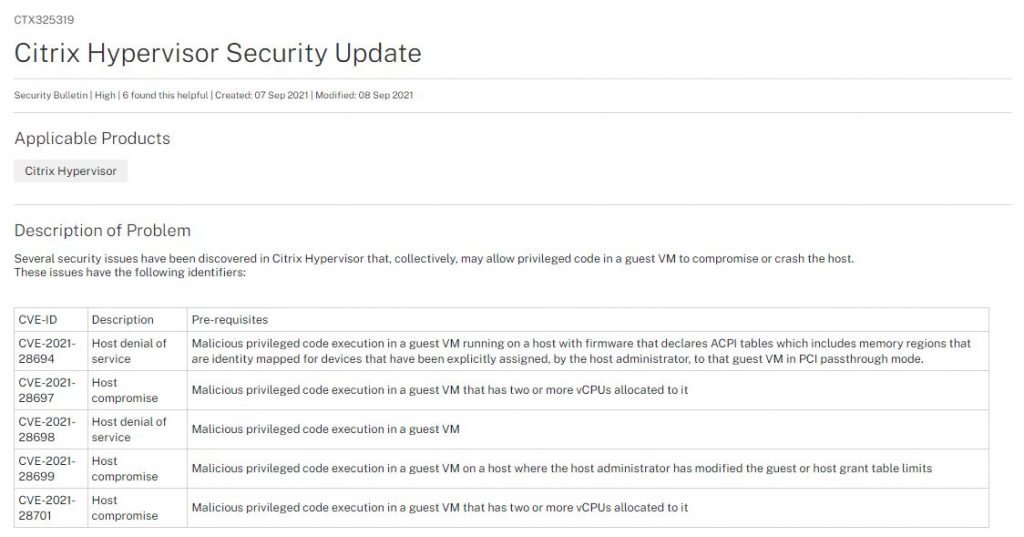
Another prominent bug is CVE-2021-28694, described as a page mapping problem that is related to ACPI tables, which can declare memory that should pass the translation phase without alterations. The hypervisor does not prevent guest virtual machines from replacing explicitly assigned device assignments by the host administrator, which could lead to a host denial of service (DoS) condition. This vulnerability received a CVSS score of 6.8/10.
Moreover, the company tackled CVE-2021-28698, another DoS flaw that received a CVSS score of 5.5/10. Apparently, this flaw exists because Hypervisor takes too long to iterate the information stored in a domain’s lease mappings.
Finally Citrix addressed CVE-2021-28699, a flaw whose exploitation could lead to host compromise if the administrator has modified the limits of the guest or host lease table. This attack is directly related to CVE-2021-28701, an error that exists because hypervisor would reassign the pages to which the guest retained permissions.
This report was also published by the Cybersecurity and Infrastructure Security Agency (CISA), which recommends users of affected implementations to update as soon as possible.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











