After rebranding themselves as a new operation dubbed as El_Cometa, the SynAck ransomware group decided to publish the master keys for the decryption of systems infected by this malware variant.
As some users may know, when ransomware operations encrypt files an encryption key is generated on the victim’s device, which in turn is encrypted using master keys. This key is embedded in the encrypted file or in the ransom note and can only be decrypted using the decryption master keys of the ransomware group.
This morning it was confirmed that the SynAck ransomware operation released the master keys and decryptors to remove the infection, plus a manual for using the published tools. This information was posted on the dark web platform employed by SynAck to publish samples of information stolen from the victims.
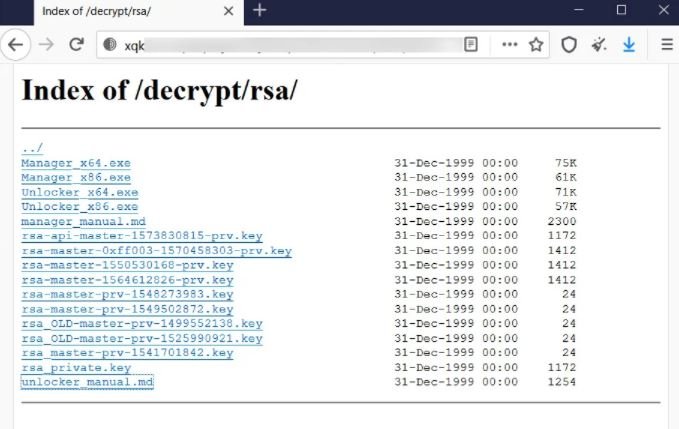
The tools revealed by the hackers were shared with celebrated ransomware researcher Michael Gillespie, who verified the authenticity of these master keys and pledged to develop a decryption tool so that victims could recover their infected files without having to pay a ransom.
About SynAck, cybersecurity specialists point out that this operation was launched in the fall of 2017, although it recorded its highest activity rates until mid-2018 and then returned to an intermittent inactivity extended until last year.
As mentioned above, this ransomware operation changed its name to El_Cometa, further announcing that they will begin working as a ransomware as a service platform (RaaS) to significantly increase their reach.
Cybersecurity experts report that this is a common practice of ransomware groups that decide to close operations or switch to a new malware variant. Other groups that have made similar decisions are Avaddon, Crysis, FilesLocker, TeslaCrypt, and Ziggy.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











