This morning, Microsoft security teams issued an alert related to the detection of a new vulnerability in the Windows Print Spooler service. Tracked as CVE-2021-36958, this flaw exists due to a remote code execution issue when the print service incorrectly performs operations on privileged files.
According to the report, threat actors who manage to exploit this vulnerability could execute arbitrary code with SYSTEM user privileges, acquiring the ability to install programs, view and modify sensitive data, and create new user accounts with high privileges.
Microsoft notes that there are no patches available for this flaw, so the only possible fix at this time is to disable the Print Spooler service until further notice. Microsoft attributes the report of this new vulnerability to Victor Mata, a researcher at security firm FusionX.
In this regard, vulnerability analyst Will Dormann mentions that this vulnerability is compatible with the exploit published a couple of weeks ago by researcher Benjamin Delpy and described in previous reports. The expert also notes that Microsoft appears to have described this flaw as a remote code execution error, although a successful attack can only be launched with local access to the affected systems, something he expects the company will be fixing in the coming days.
As mentioned above, Microsoft has not released updates to address this flaw; although they point out that it is possible to eliminate the attack vector by disabling the print service. For obvious reasons, this will prevent affected devices from being able to print files, so a less aggressive mitigation method is to allow the Windows system to install printers only from authorized servers.
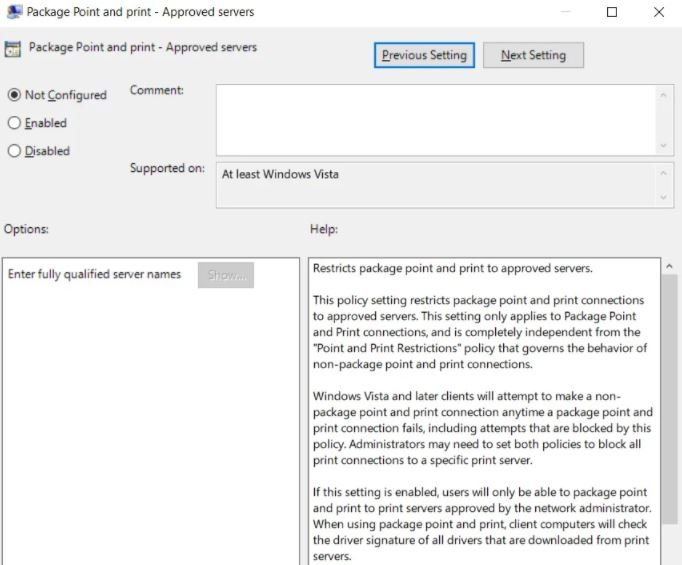
To enforce this protection, you must use the “Package Point and Print Approved Servers” group policy, which will prevent any non-administrative user from installing print drivers that have not been approved.
Remember that it is necessary to enter into the system a list of servers allowed by the administrator to use as a print service. If you do not have a print server on your network, you can use a false server name to enable this feature. Enabling this group policy will protect Windows users against exploitation of CVE-2021-36958, but it will not prevent threat actors from taking over an authorized print server with malicious drivers.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











