Tech firm Accenture has confirmed that its systems were compromised by a ransomware attack allegedly deployed by LockBit 2.0 operators. In addition to encrypting thousands of files, hackers threaten to leak a large amount of Accenture’s sensitive information if their demands are not met.
Although the operators of this ransomware variant have shown no evidence of the attack, they claim that they will sell the information if the company does not pay the ransom: “We expect their customer service to be better than their security is. If anyone is interested in buying this information, they can contact us,” reads an announcement posted on LockBit’s dark web website.
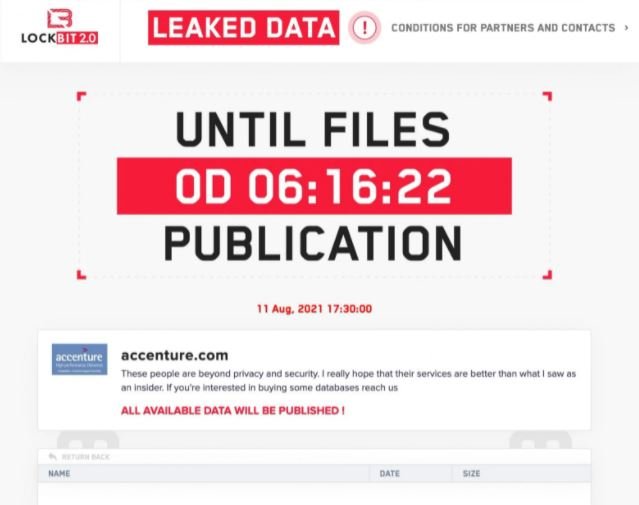
However, a cybersecurity researcher was contacted by an alleged member of LockBit 2.0 operation, who claims that hackers managed to steal a total of 6 TB of confidential information and that the ransom demanded of Accenture is $50 million USD. In addition, this alleged hacker claims that they managed to compromise the company’s networks in collaboration with an insider.
By the time of writing, Accenture should already be notifying its customers about this incident, in addition to having implemented a contingency plan. This company works with thousands of organizations around the world, providing IT services in the automotive, banking and technology industries, besides working with dozens of government organizations.
A subsequent report from cybercrime intelligence firm Hudson Rock claims that Accenture is operating at least 2,500 compromised computers inside its technology infrastructure.
LockBit has been involved in some high-profile incidents recently. Just a few days ago the Australian government issued a security alert notifying public and private organizations about a new wave of ransomware infections using LockBit 2.0; for these new attacks, hackers decided to start recruiting members of the affected organizations, which seems to make it considerably easier to access a target.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











