A new cybercriminal operation identified as Prometheus is helping multiple hacking groups distribute malware across various compromised websites. Researchers point out that Prometheus operates a service variant known as a traffic distribution system (TDS).
This system operates similarly to a conventional online service, as hackers must create accounts on Prometheus and pay a fee to access the services. Threat actors upload the payload they want to distribute to the platform, establish a profile of users to attack, and provide a list of compromised web servers.
Once the hackers have established their attack profile, Prometheus will scan the list of compromised websites to deploy its own backdoor on the hacked servers. This will allow cybercriminals to launch phishing campaigns with links to malicious websites.
If the affected users arrive at the compromised websites, the Prometheus backdoor analyzes some indicators on the target system (processor, web browser, operating system, among others) in order to redirect the victim to a website where a malware variant is hosted that fits the analyzed features.
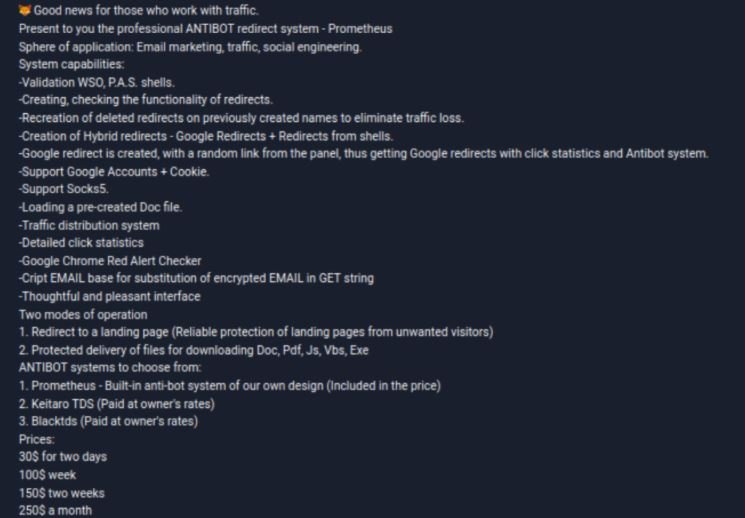
This cybercriminal system was discovered by Group-IB researchers, who found some ads on dark web hacking forums offering subscriptions of between $30 USD for a couple of days up to $250 USD per month. Analyzing posted announcements and other activity traits, experts suggest that this group has been active since at least mid-2020.
Researchers claim that some notorious recent cybercriminal campaigns could have been deployed with the support of Prometheus TDS, including infections from malware variants such as Buer Loader, Campo Loader, IcedID, SocGholish and QBot.
This is a new example of the latest cybercriminal trends, with malicious campaigns that no longer involve only a hacking group, but involve multiple actors dedicated specifically to the operation of a specific step. The new campaigns can be divided into groups for malware development, antivirus scanning, encryption, social engineering and traffic distribution, among other malicious activities.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











